The FluBot strain of Android banking malware, which was initially observed in Spain in late 2020 before spreading more widely across Europe over the following months, is now targeting Australian banks.
Once installed, FluBot periodically sends a list of apps installed on the device to one of its command-and-control servers. The server responds with a list of apps the malware should overlay. Upon one of these apps being launched, FluBot immediately displays an overlay on top of the legitimate app. The overlays impersonate the legitimate apps and are designed to collect the victim’s online banking credentials, which are sent to the criminals operating FluBot via the command-and-control server.
Netcraft monitors the list of apps targeted by FluBot, and today discovered that FluBot for the first time is serving overlays for Australian banking apps, including Bank Australia, Bank of Melbourne, BankSA, CommBank, Great Southern Bank Australia, HSBC Australia, National Australia Bank, St.George Bank, Suncorp, and UBank.
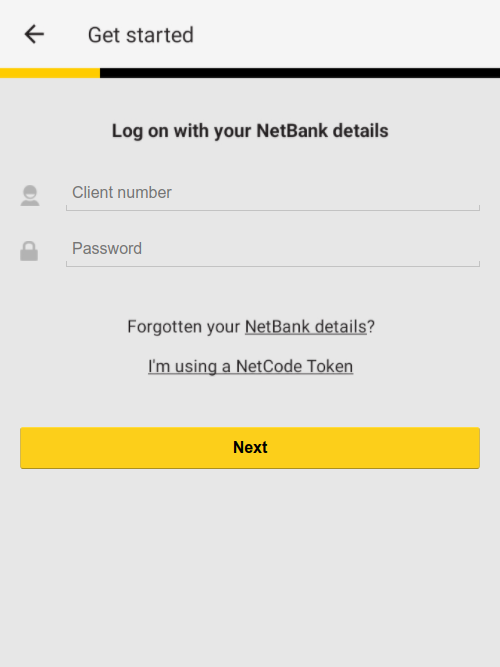
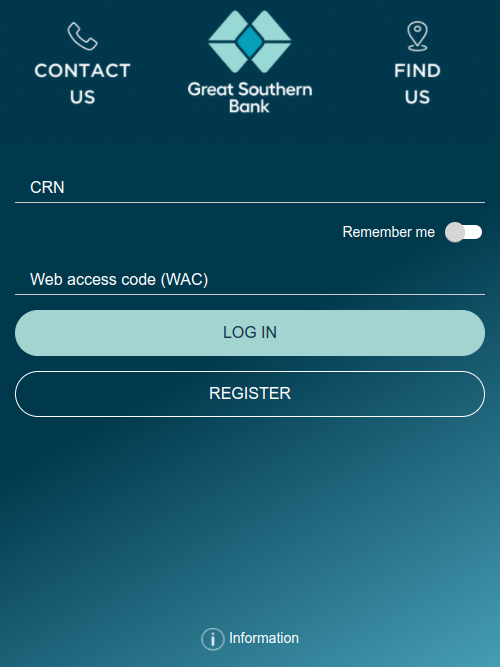
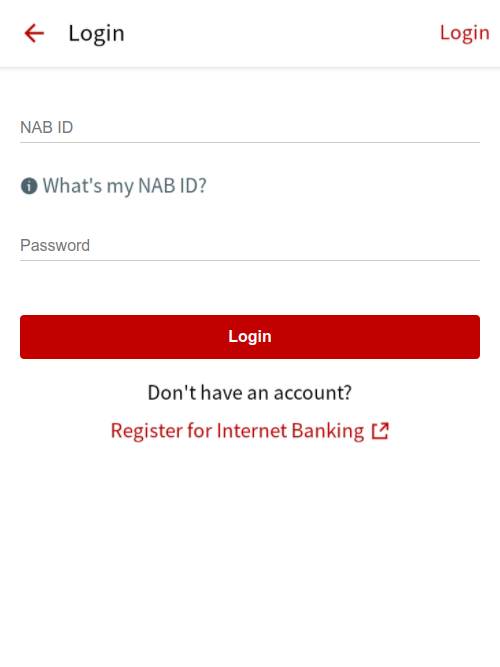
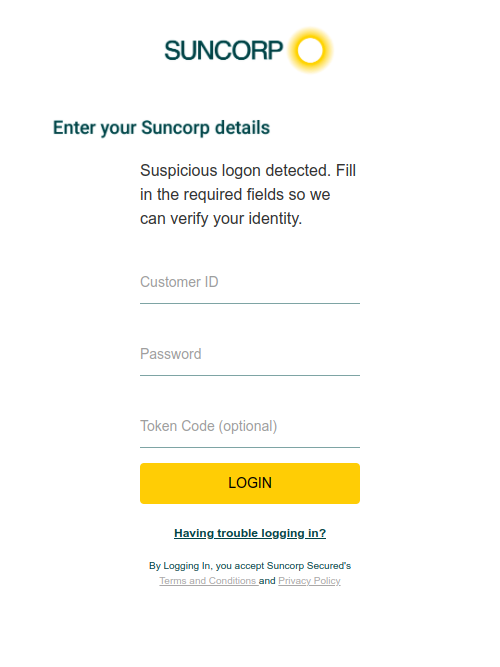
banks.
FluBot is spread through text messages, which usually purport to be from a delivery company providing a tracking update and contain a link to a lure page. The lure page attempts to trick potential victims into downloading and installing the malware, which is disguised as a parcel tracking app.
Android users can protect themselves with Netcraft’s Android app, which blocks FluBot lure pages and other malicious sites – preventing users from being tricked into downloading and installing FluBot in the first place. Banks can protect their customers through a range of countermeasures Netcraft provides.