The website of the Agency for the Safety of Aerial Navigation in Africa and Madagascar (ASECNA) has been hijacked by hackers. Browsing to the site’s homepage currently presents visitors with a PayPal phishing site, where visitors are asked to submit PayPal account details, including their password, address and credit card details. After entering these details, victims are redirected to the real PayPal website.
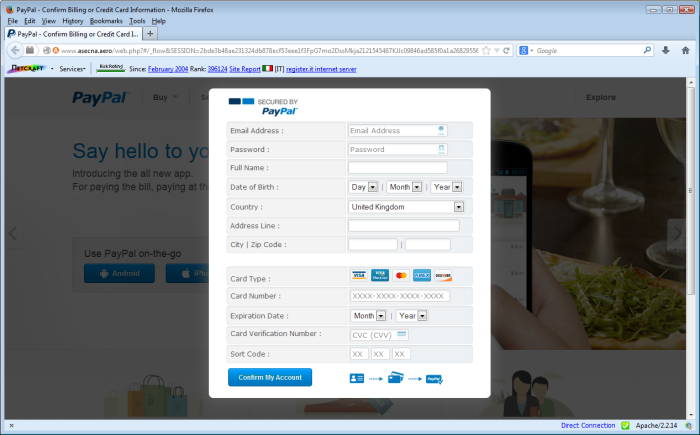
Visitors to the ASECNA homepage are automatically redirected to this phishy PHP script in the root directory.
ASECNA is responsible for managing 16 million square kilometers of airspace (1.5x the size of Europe), covering six flight information regions, but has yet to remove the phishing site from its own homepage. Netcraft detected and blocked the above PayPal phishing site on Tuesday, yet visitors to www.asecna.aero who ignore their browser’s warnings are still being presented with the phishing content today (Friday). Comments within the source code suggest that the phishing site was designed by a man living in Salé, Morocco.
A second PayPal phishing site was also found in a subdirectory on the same server, but it has since been deleted. It is possible that it was deleted by the fraudster behind the current attack, as it would be peculiar for ASECNA to have deleted phishing content from a subdirectory while leaving the more obvious phishing content on its homepage. The deleted phishing site used a phishing kit which hid its author’s hotmail.fr email address in a Base64 encoded string. This made it less obvious to anyone deploying the kit that a duplicate copy of any stolen credentials would also be surreptitiously emailed directly to the kit’s author. The phishing kit author’s email address links him to a Facebook account which places him in Rabat, a Moroccan city which attracts many commuters from Salé. The same email address has been found in several other phishing kits, including some which target Visa customers.
It is rather unusual to see phishing sites hosted on .aero domains because they can only be registered by eligible members of the aviation community. SITA (an air transport IT and communications specialist) is responsible for verifying eligibility, and may ask applicants to provide company documents and pilot licenses, which reduces the likelihood of a fraudster registering a .aero domain specifically for the purpose of phishing. Many other top-level domains are easier to register, and some are even free.
.aero is a sponsored top-level domain (sTLD). The original agreement for the domain was signed in 2001, and domains became available for registration in March 2002. In 2009, SITA signed a new 10-year sponsorship agreement for the .aero sTLD with ICANN.
How the ASECNA site looked prior to the compromise.
Netcraft’s April 2014 survey found more than 9,000 sites using the .aero sTLD, and in the past 6 months they have hosted a total of 9 phishing sites. Each attack used an established .aero website which was compromised to host phishing content, rather than using a .aero domain registered specifically for fraud.
It is not apparent how the ASECNA website was compromised, although it appears to be running Apache 2.2.14, which could be vulnerable to a plethora of security issues which can be exploited remotely. The server also uses PHP 5.2.5, which was released in 2007, and the entire 5.2 branch of releases reached end of life status at the beginning of 2011. Unless the server is using a backporting approach to software maintenance, this old version of PHP could also expose a large number of vulnerabilities to remote attackers.
Netcraft’s continuously updated, professionally validated phishing feed is used throughout the internet infrastructure industry. In addition to internet registries, all of the main web browsers, along with major anti-virus companies, firewall vendors, SSL Certificate authorities, large hosting companies and domain registrars use Netcraft’s feed to protect their user communities. Please contact us for more information about these services, or about Netcraft’s phishing site takedown service.