Key Data
Netcraft researchers have observed the cybercriminals behind darcula, the phishing-as-a-service (PhaaS) platform, have released a new update to their darcula-suite, accelerating phishing kit creation with AI, confirming the use of AI to more quickly create high-quality, customized phishing kits. We first covered darcula’s platform, which enables widespread and highly targeted smishing attacks, in March 2024 and February 2025. darcula has continued to evolve into a sophisticated, subscription-based ecosystem with tooling and speed that rivals modern tech startups.
As of yesterday morning, April 23rd BST, Netcraft researchers have identified a major enhancement: the darcula-suite toolkit, which allows users to create their own phishing pages, now leverages generative AI capabilities. This addition lowers the technical barrier for creating phishing pages, enabling less tech-savvy criminals to deploy customized scams in minutes. The new AI-assisted features amplify darcula’s threat potential by simplifying the process to build tailored phishing pages with multi-language support and form generation — all without any programming knowledge.
Darcula is one of several communities under the loosely affiliated Smishing-Triad, known for mass-targeting individuals globally via SMS-based phishing (smishing) attacks.
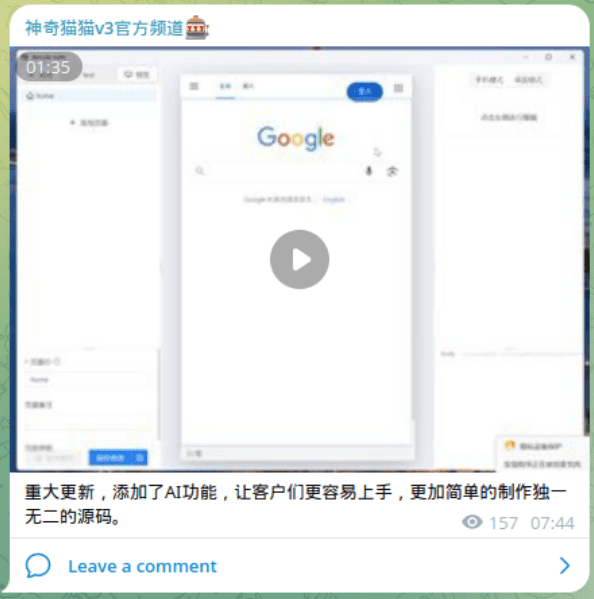
Announcement of AI functionality added to darcula-suite, Google translation reads as: “A major update adds AI functionality, making it easier for customers to get started and create unique source code.”
Darcula: a phishing platform built like a startup
Darcula is not just a phishing platform; it’s a service model designed for scale. Users pay for access to a suite of tools that enable impersonation of organizations in nearly every country. Built using modern technologies like JavaScript frameworks, Docker, and Harbor, the infrastructure mirrors that of legitimate SaaS companies.
Distribution is also modernized. Attackers spread phishing lures through SMS, RCS, and iMessage, even using tactics to trick recipients into replying so links become clickable on iOS. The high-volume campaigns seen with darcula v2 were just the start of the ongoing innovation.
From templates to toolkits: the rise of darcula-suite
In early 2025, Netcraft observed the emergence of darcula v3, which introduced a redesigned admin dashboard and support for custom phishing templates built using the new darcula-suite desktop application. Unlike earlier versions that came with prebuilt templates, darcula-suite empowers less technical users, including those with no coding or web development experience, to create their own phishing kits.
The process is simple: users provide a URL of a legitimate brand or service, and the tool automatically visits that website, downloads all of its assets, and renders an editable version. Users can then inject malicious content such as phishing forms or credential capture fields directly into the cloned page. It creates a custom-built, branded phishing site that closely impersonates the real site.
This customization enabled attackers to target niche and regional brands that had rarely been the target of phishing kits due to low awareness and reduced ROI. Since each phishing page can be different vs. relying on a static number of templates, traditional signature-based detection methods are increasingly ineffective, and to outpace these threats, organizations must adopt more dynamic, behavior-based approaches.
April 23 update: darcula-suite’s AI upgrade raises the stakes
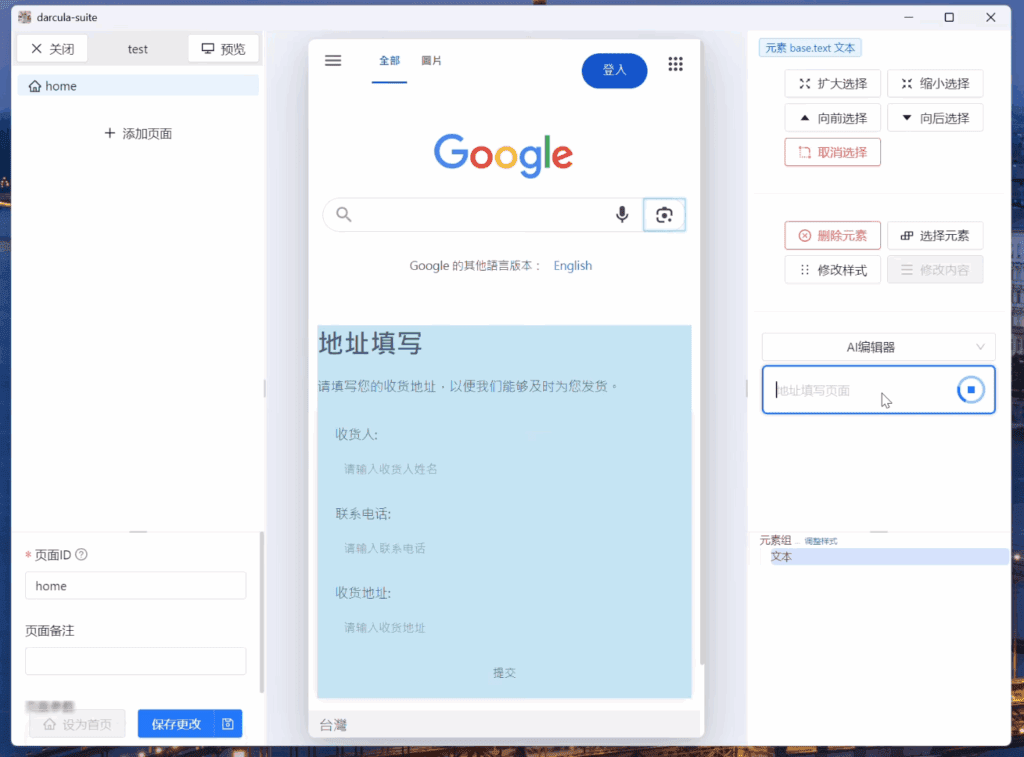
Demonstration of darcula-suite AI functionality: AI is used to generate and then translate a phishing form into a cloned Google page.
On April 23rd, Netcraft detected the release of a new feature in darcula-suite: generative AI integration. This video of darcula AI capabilities demonstrates how users can now:
- Generate phishing forms (e.g. address collection forms) in any language.
- Customize form fields, adding inputs like postal code, email, and more.
- Translate entire phishing forms into local languages automatically, reducing time and effort.
- Maintain layout and visual styling with minimal manual input.
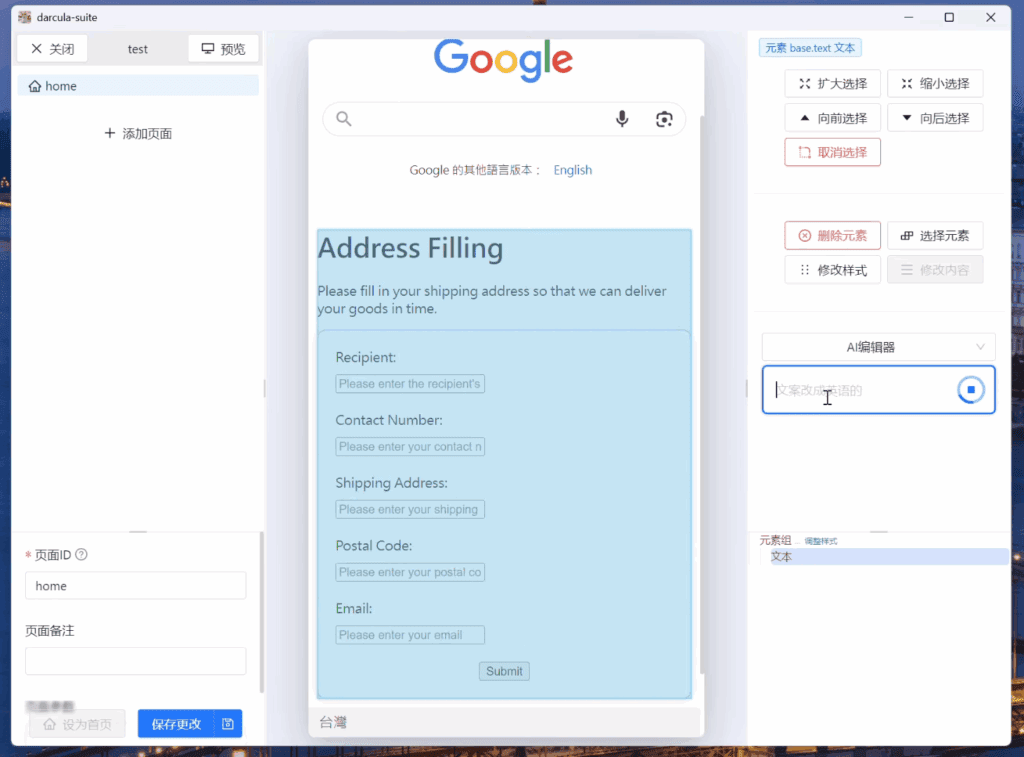
In the demo, an attacker cloned Google’s homepage and asked the AI to generate an address collection form in Chinese. The AI complied, and the user further instructed it to add more fields and translate the content to English.
This kind of flexibility means a novice attacker can now build and deploy a customized phishing site in minutes.
Criminal enablement at scale
The generative AI upgrade expands darcula’s usability:
- Accessibility: Attackers with minimal technical background can now generate convincing phishing pages.
- Speed: Campaigns can be launched faster, with rapid AI-generated content and translations.
- Scalability: The ability to target any brand in any language multiplies the number of potential victims.
- Evasion: Each page’s uniqueness makes automated detection and takedown more challenging.
Demonstration of darcula-suite AI functionality: User has requested an ’Address Filling Page,’ which is live generated by the AI.
Netcraft countermeasures in action
In response to Darcula’s global phishing operations, Netcraft has taken down 25,000+ fake websites, blocked nearly 31,000 IP addresses, and flagged more than 90,000 phishing domains since March 2024. We’re not only seeing the launch of these tools—we’re finding the threats that originated in darcula’s environment. And we’re taking them down.
We expect this latest iteration of darcula-suite to surpass the popularity of its predecessor as the new AI features become more widely adopted within cybercriminal circles.
Demonstration of darcula-suite AI functionality: Form is translated from Chinese to English.
Recommendations: safeguarding against modern phishing
Organizations and individuals should consider the following steps:
- Exercise caution about messages sent in RCS groups. It is unlikely legitimate brands would alert users in these channels.
- Be skeptical of RCS or iMessage messages coming from unknown numbers or email addresses. With end-to-end encryption, phone-carrier scam protection is bypassed so identification of malicious messages relies on on-device detection and human recognition.
- A broader range of targets are at risk with darcula’s new customization capabilities so when visiting smaller or niche sites across the internet, stay vigilant to ensure you’re interacting with the legitimate brand.
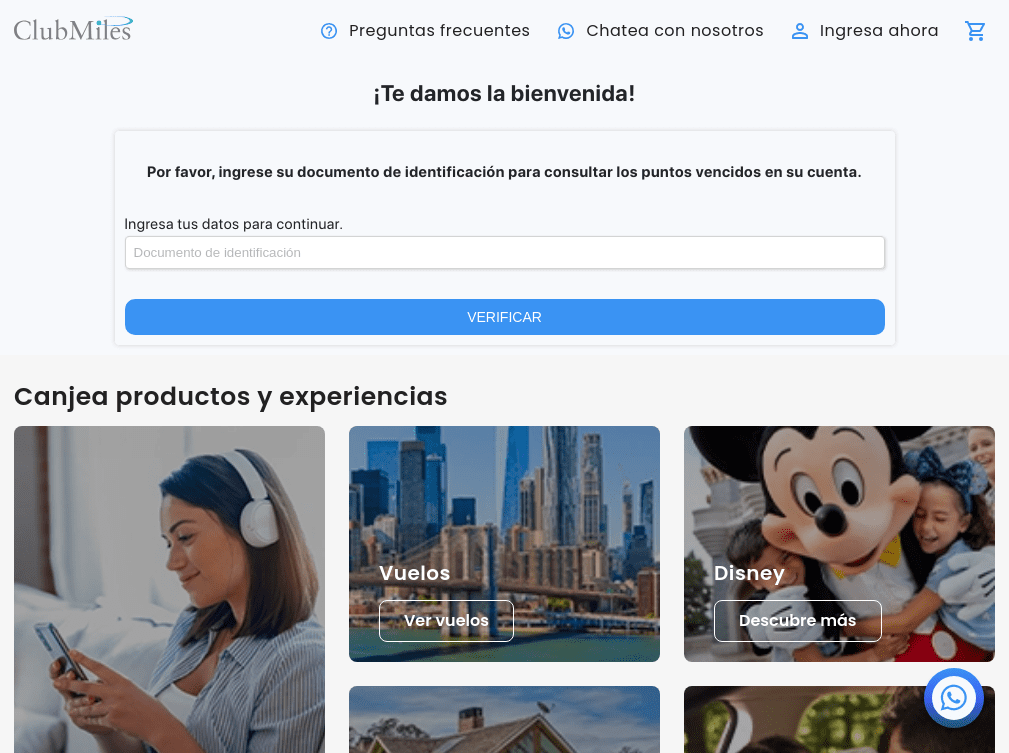
Phishing page impersonating ClubMiles, detected by Netcraft, which appears to have been created using darcula-suite
Learn more about Netcraft’s brand protection capabilities
Netcraft’s research and disruption capabilities are constantly evolving to counter emerging threats like darcula. Our data-driven intelligence helps detect and dismantle phishing infrastructure at scale, safeguarding global brands and end users.
To stay informed on evolving phishing tactics—and how to counter them—visit our blog and or request a demo.