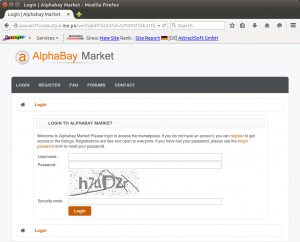
Fraudsters operating on the AlphaBay darknet market are using phishing attacks to steal login credentials from other criminals. In this particular attack, the phishing site mimics the address of one of AlphaBay’s Tor hidden services.
AlphaBay describes itself as a darknet market that specialises in all kinds of illegal goods, and so its users are reminded to access the site directly through the Tor anonymity network, rather than via a WWW to .onion gateway. However, this is not the only thing that users need to worry about: some of the criminals on AlphaBay also try to steal other users’ credentials by sending messages to trick them into visiting phishing sites.
AlphaBay was originally founded by members of Russian carding forums, but the range of illegal goods being sold on the anonymous marketplace now includes drugs and weapons as well as credit card details. AlphaBay uses a .onion address which allows the website to run as a hidden service on the Tor network – this means that the physical location of the website remains anonymous, as well as the locations of Tor users who access it.
The genuine AlphaBay hidden service uses the address pwoah7foa6au2pul.onion. A hidden service’s address is derived from the public key used to authenticate the connection, so it is difficult to convincingly impersonate the site without having access to the owner’s key pair. However, the fraudster could easily have computed a partial match using tools such as scallion; for example, Netcraft generated the lookalike address pwoah7f5ivq74fmp.onion within minutes.
However, in the case of this phishing attack, the fraudster has simply created a lookalike domain on the public internet, using the address pwoah7foa6au2pul.me.pn.
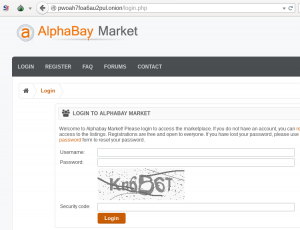 The genuine AlphaBay Market login form, accessed via its .onion address using the Tor Browser Bundle.
The genuine AlphaBay Market login form, accessed via its .onion address using the Tor Browser Bundle.
The address used by the phishing site will look familiar to regular users of the AlphaBay darknet market, but rather than pointing to an anonymous hidden service, it points to a phishing site hosted by AttractSoft GmbH in Germany.
The phishing site used in this attack was discovered on Thursday and is still operating at the time of writing. It mimics the genuine AlphaBay Market login page, and prompts the victim to enter his username and password. A client-side check forces the victim to also complete the security code CAPTCHA field, although the phishing site does not care whether the correct value was entered.
The stolen credentials are then submitted to a PHP script, which immediately redirects the victim to the genuine AlphaBay hidden service.
This phishing attack makes use of a me.pn domain, which was likely chosen because addresses under this domain can be registered for free, and the “.me.pn” string bears a (somewhat tenuous) similarity to the .onion TLD, at least in terms of its length.
Ironically, some of the services that can be bought and sold on the AlphaBay Market include spam sending services, “bank drops” (for receiving fraudulent bank transfers), account details, and other services useful to fraudsters engaged in phishing. This attack could therefore be viewed as yet another example of fraudsters defrauding fraudsters.
In a further show of there being no honour amongst thieves, the HTML source of the phishing site appears to have been copied from a previous lookalike site using the onion-market.co domain name. This domain name has since been repossessed by its registrar, GoDaddy, which is typical of domains that have been paid for with fraudulent funds or subjected to chargebacks.
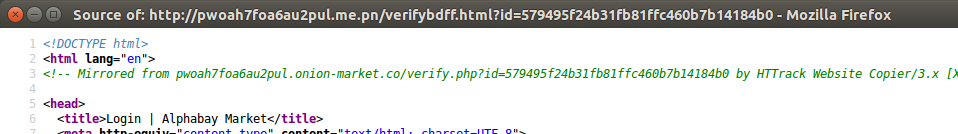 The content of the phishing site was mirrored from another site that has since been suspended.
The content of the phishing site was mirrored from another site that has since been suspended.
AlphaBay has been operating since the end of 2014, when it helped fill the void left after the demise of Silk Road and Silk Road 2.0. It has since become one of the largest darknet markets, gaining wide publicity after it was used to sell compromised Uber accounts and data stolen from the TalkTalk breach in 2015.