Bangladesh is one of the world’s largest producers of fish; but lately, its government has also become an inadvertent exporter of phish.
Over the past week, several phishing sites have popped up on Bangladeshi government websites, under the .gov.bd second-level domain. These fraudulent sites have been used in phishing attacks against customers of Wells Fargo bank, Google, AOL, and other email providers.
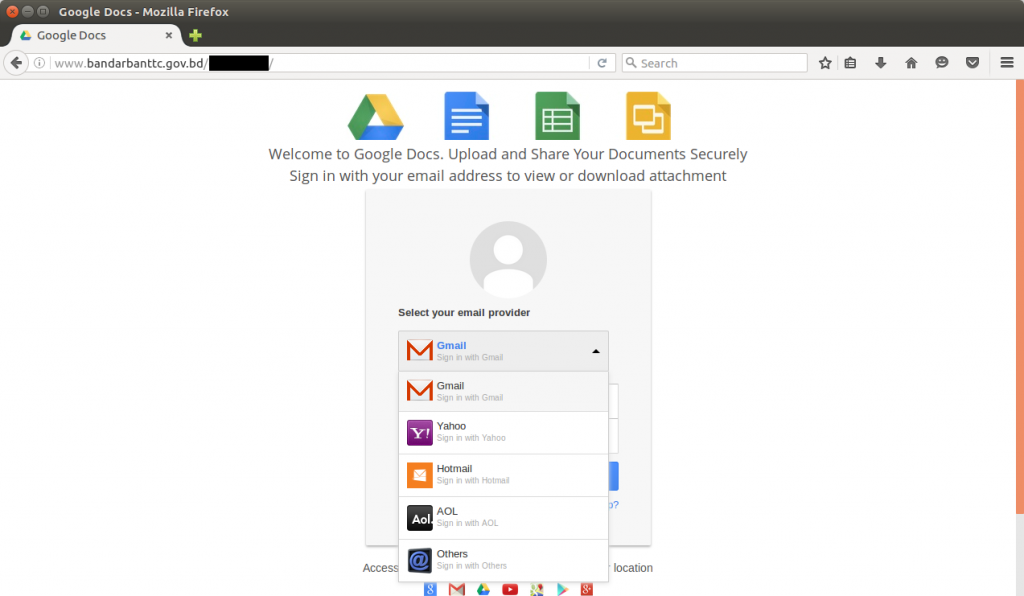 One of the phishing sites currently using a .gov.bd domain is hosted on a website belonging to the Bandarban Technical Training Center in Bangladesh. The fraudulent content imitates Google Docs in an attempt to steal victims’ email credentials, whichever mail providers they use.
One of the phishing sites currently using a .gov.bd domain is hosted on a website belonging to the Bandarban Technical Training Center in Bangladesh. The fraudulent content imitates Google Docs in an attempt to steal victims’ email credentials, whichever mail providers they use.
Domain name registrations under .gov.bd are restricted to government-related entities in Bangladesh, although it is unlikely that the government is directly responsible for these attacks. As with most phishing sites, the fraudulent content has probably been placed on these government sites by remote hackers; nonetheless, this would make the Bangladesh government at least responsible for poor security.
The vast majority of websites under .gov.bd are hosted within Bangladesh, but the apparently-compromised server involved in these attacks is one of a few that are hosted in the United Kingdom, on a static IP address used by the hosting company Nibs Solutions. No Bangladeshi servers are currently serving phishing sites from .gov.bd domains.
After more than a week since this spate of phishing attacks started appearing on UK-hosted .gov.bd sites, none of the fraudulent content has been removed. The presence of multiple live phishing sites on the affected server, and the fact that the previous compromises have not yet been cleaned up, suggests that whatever security vulnerabilities might have affected the server are yet to be resolved.
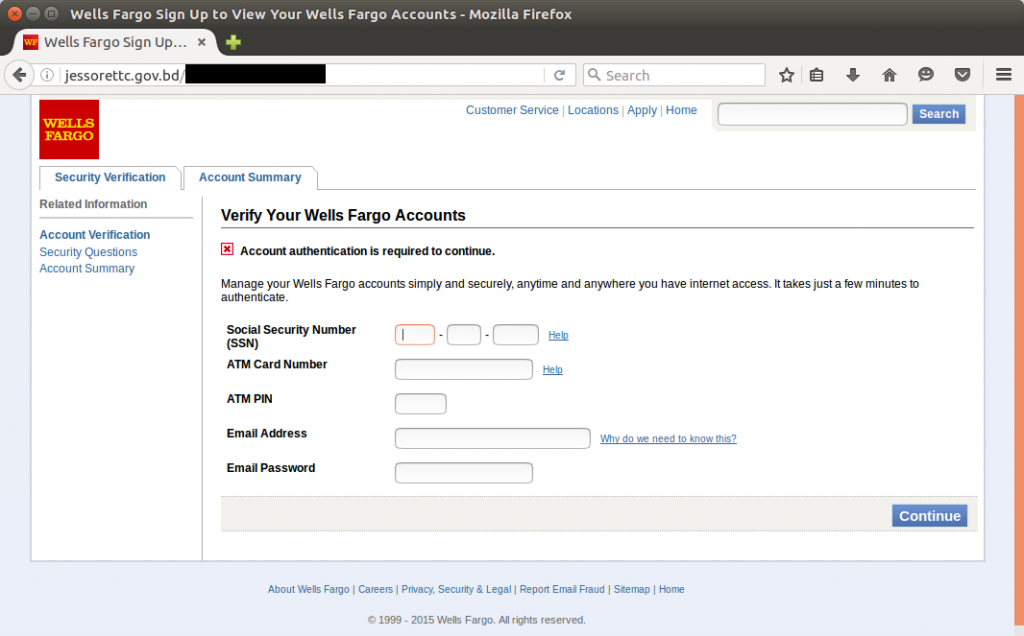 Detected just over a week ago, the oldest phishing site in this spate of attacks targets Wells Fargo customers and remains accessible today on the Jessore Technical Training Center website at jessorettc.gov.bd. This training center was established by the Government of the People’s Republic of Bangladesh in 2004, hence its eligibility to use the .gov.bd domain.
Detected just over a week ago, the oldest phishing site in this spate of attacks targets Wells Fargo customers and remains accessible today on the Jessore Technical Training Center website at jessorettc.gov.bd. This training center was established by the Government of the People’s Republic of Bangladesh in 2004, hence its eligibility to use the .gov.bd domain.
Bangladesh has a relatively small presence on the web, with just over 30,000 websites making use of the entire .bd country code top-level domain. However, the ratio of phishing incidents to sites is quite high at roughly 1 in 100.
Users of the Netcraft anti-phishing extension are already protected from these attacks, including the examples shown above, even though the fraudulent content has not yet been removed by the sites’ administrators.