Online Banking customers are being hit hard by steadily innovating phishing techniques which are being used by fraudsters to steal money and identities. The Netcraft Toolbar community has recently received two different attacks against Charter One Bank customers. In the first incident discovered last week, fraudsters exploited a facility which allowed them to display their own content within the Charter One Personal Online Banking SSL site at www.totallyfreebanking.com. The second incident was discovered at the start of this week and affects the www.charterone.com site.
In the first incident, the fraudster exploited a weakness that allows one of the bank’s own web sites to display contents from any arbitrary URL within a frame. As the containing page is served securely over SSL, the user’s browser displays a padlock symbol which is signed by Verisign and confirms that the site belongs to Charter One Financial.
Despite the reassuring presence of the browser padlock, the specially crafted URL causes one of the frames to display a form hosted on an ip address registered to Inktomi Corporation [now part of Yahoo] at https://s.p5.hostingprod.com/@www.totalfree.biz/ssl/. The fraudster’s site also uses the SSL protocol, to avoid warning dialogs being displayed when a user visits the parent phishing URL.
This particular fraudster even exhibits a sense of awareness to those involved with combating phishing – just as the security community have coined the terms “phishing” and “pharming” to analogize fishing and farming, he refers to the form in the page as a “phorm”.
The second incident uses an iframe to neatly inject arbitrary content onto a page at www.charterone.com, making it very difficult to tell that anything is awry. Wall St. Journal writer Jeremy Wagstaff comments on this in his blog and also told us that of the several anti-phishing tools he tried, the Netcraft Toolbar was the only one to successfully block this attack.
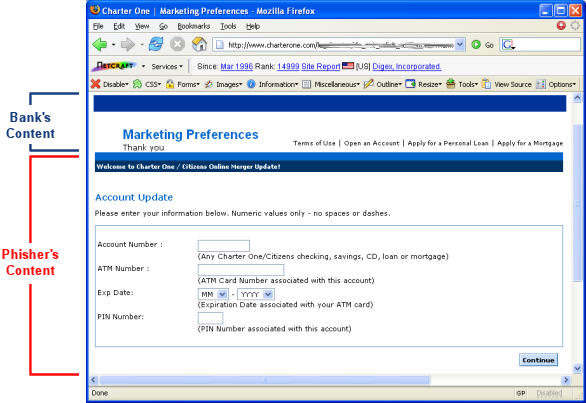
One surprising facet of hosting frauds on banking sites is that banks to date have tended to be significantly slower than hosting companies to react to fraudsters using their sites. Fraudsters have benefited from the longevity of frauds hosted on banking sites as well as their plausibility.
Netcraft’s Toolbar database collates a large number of confirmed phishing sites every day, the most effective of which use cross site scripting and page injection to commit fraud. Netcraft provides a range of services for banks and other financial institutions to eliminate these kinds of errors from their systems, including comprehensive application testing and training for developers and designers of web based applications.