WikiLeaks is currently under another distributed denial of service (DDoS) attack. This time the target appears to be cablegate.wikileaks.org – the website which hosts the leaked US embassy cables.
When the cablegate site was launched on Sunday, WikiLeaks’ main website at www.wikileaks.org was subjected to a similar attack, causing it to go offline for several hours. The cablegate site itself was not affected by those attacks.
Today’s attack is still ongoing, and has caused noticeable downtime over the past couple of hours:
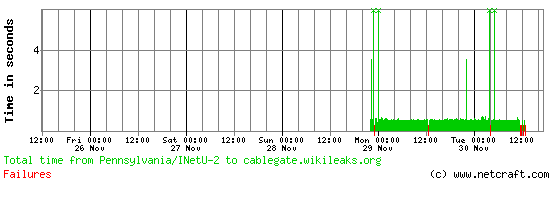
The cablegate hostname is still configured to use three different IP addresses on a round-robin basis, essentially acting as a load balancer, although this does not appear to have prevented the current attack from succeeding. The performance graph shows the site may have been attacked over shorter periods earlier in the week, even though it has only made available a small fraction of the 250,000 cable messages. The attacks are likely to be symbolic more than anything else, as several large media groups have already been supplied with the full set of leaked messages.
A real-time performance graph for cablegate.wikileaks.org can be viewed here.