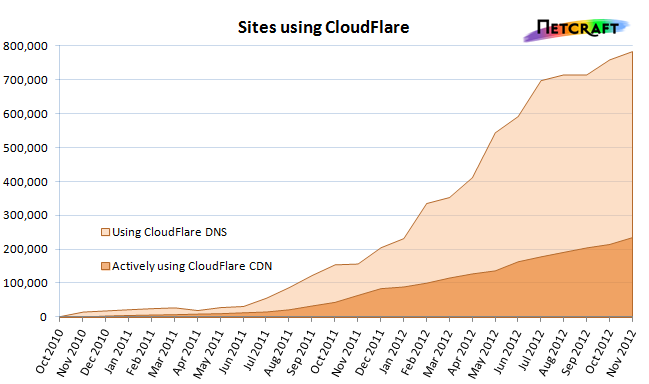
Just over two years since its launch, the CloudFlare content distribution network is being actively used to accelerate traffic to more than 235,000 websites in Netcraft’s Web Server Survey. In total, we found 785,000 sites currently configured to use CloudFlare’s DNS servers. Once a domain has been configured to use these servers, any of its subdomains can be routed through the CloudFlare system at the click of a button. Paying customers can also route their traffic through CloudFlare by setting up a CNAME within their own DNS.
CloudFlare’s network is globally spread across 23 datacenters, half of which are entirely remotely operated. Nine of these datacenters were opened during a month-long expansion effort which ended in August and resulted in a 70% increase in network capacity. CloudFlare’s content distribution network spreads website content around these datacenters, allowing visitors to request pages from geographically closer locations. This typically reduces the number of network hops, resulting in an average request taking less than 30ms.
In addition to moving static files closer to visitors, CloudFlare also offers an automatic web optimisation feature called Rocket Loader. This combines multiple JavaScript files into a single request, which saves both time and bandwidth. Pro, Business and Enterprise users can also enable beta support for SPDY requests, which achieve better latency than HTTP through the use of compression, multiplexing and prioritisation.
![]()
In October, CloudFlare introduced support for OCSP stapling, which it claims has increased the speed of SSL requests by 30%. The Online Certificate Status Protocol allows browsers to ask a certificate authority (CA) whether an SSL certificate it has issued has been revoked. Handling these requests in realtime can be challenging, particularly if the CA has issued a large number of certificates, or has issued certificates to extremely busy websites. OCSP stapling solves this problem by delivering the OCSP response directly from CloudFlare’s network, removing the need for the browser to perform an additional DNS lookup and send a request to the CA’s own OCSP server. OCSP performance is often overlooked when considering which CA to buy a certificate from, but can have a crucial impact on the overall performance of a customer’s website.
With its insight into the kind of requests being sent to many different websites, CloudFlare is well-positioned to identify malicious traffic and provide protection to all of its customers. Depending on which level of security is enabled, CloudFlare can deny requests which are attempting SQL injection attacks, comment spam, excessive crawling, email harvesting, or exploiting cross-site scripting vulnerabilities. Business and Enterprise users can also benefit from CloudFlare’s advanced DDoS (distributed denial of service) protection.
CloudFlare’s growth accelerated significantly in the summer of last year. This is when many people first became aware of the service, after it was used to handle traffic for the Lulz Security website. High profile attacks against Sony, Fox, PBS and the X Factor helped LulzSec garner 350,000 followers on Twitter, where it extolled the virtues of using CloudFlare to mitigate DDoS attacks.
Some notable high-traffic users of CloudFlare include The Hacker News, Uber Humor, Android firmware site Cyanogen Mod, and the content management system Moodle.