Netcraft has tracked Coronavirus-themed cybercrime since 16th March, shortly after it was declared a pandemic by the WHO. Scammers have been quick to take advantage of the massive worldwide attention to Coronavirus (COVID-19), and are increasingly making use of it as a theme for online fraud.
Netcraft is the largest provider of anti-phishing takedowns in the world and provides countermeasures against some 75 other types of cybercrime for governments, internet infrastructure and many of the world’s largest banks and enterprises. Coronavirus-themed cybercrime accounts for around 5% of all the attacks we perform countermeasures against, even without accounting for attacks that may otherwise be attributed to existing phishing targets.
Coronavirus Phishing attack impersonating the World Health Organisation
Coronavirus Themed Attacks
Advance Fee Frauds
Advance fee frauds typically involve promising the victim a large amount of money, with only a relatively small up-front fee required (for example, to cover processing). These attacks have required only very small changes to adapt to Coronavirus. Examples include:
I am currently receiving treatment for the COVID-19 in Huoshenshan Hospital, Wuhan, China. I am 68 years old and I have been told that I will not survive this virus. I need you to help claim and distribute my funds (us$7.5M.) to support people with the COVID-19…
My Name is Andrew Contarini from Venice Italy. I was diagnosed with Leukemia which has defied all forms of medical treatment, and last week miraculously survived Coronavirus infection… I intend and willing to empower the change of ownership for the transfer of my wealth to your possession for further Investment and Charity Disbursement to the Less Privileged and Homeless…
The COVID-19 Cash Donations policy is a 30-day free coverage that provides you to help people in your community, for hospital confinement and a benefit lump sum payout ($2,000,000.00) for you .
The United Nations in cooperation with World Bank have agreed to compensate you with the sum of One Million Two Hundred Thousand US Dollars ($1.2M)… This payment Program is organized for charity organization/Scam victims and current Corona Virus issue
Since i resume office i saw some files of Abandon compensation funds , and for the case of this Corona virus issue we also agree to compensate every citizin with little cash
There are some examples however of slightly more carefully crafted AFF scams, such as the following impersonation of the Bill & Melinda Gates foundation.
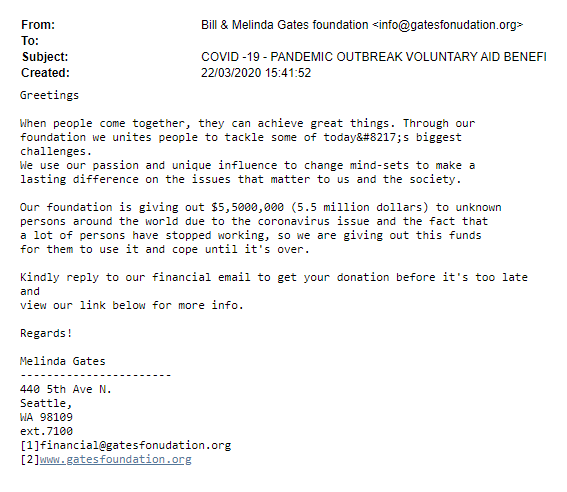
Coronavirus themed Advanced Fee Fraud
Malware Attachments
Coronavirus has additionally presented fraudsters with an effective lure to encourage victims to open email attachments. These emails are typically impersonating health organisations and governments with updates on Coronavirus, new recommendations or guidelines, information on cures, tests, and face masks.
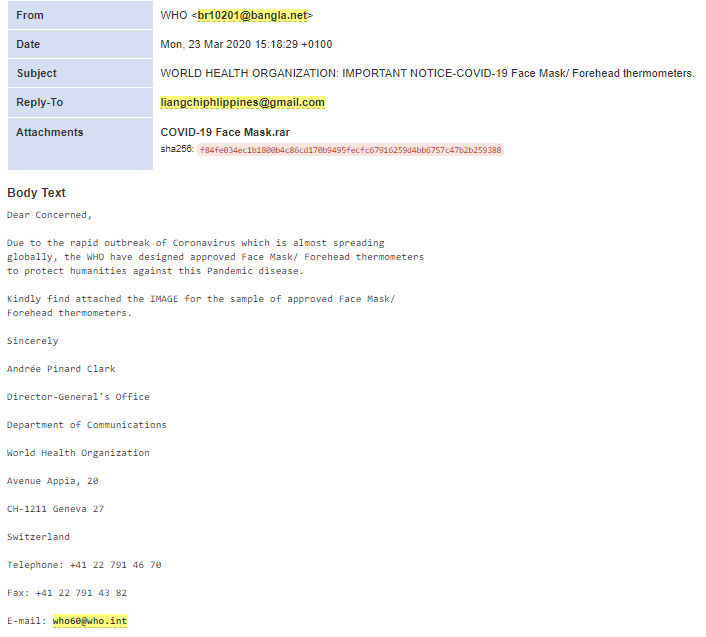
Email with a malware attachment that impersonates the World Health Organisation
Social Media Pages
All of the fraudulent social media pages seen to date are fairly basic, and have claimed to have a cure/vaccine available, and encourage victims to DM or otherwise contact the page creator.
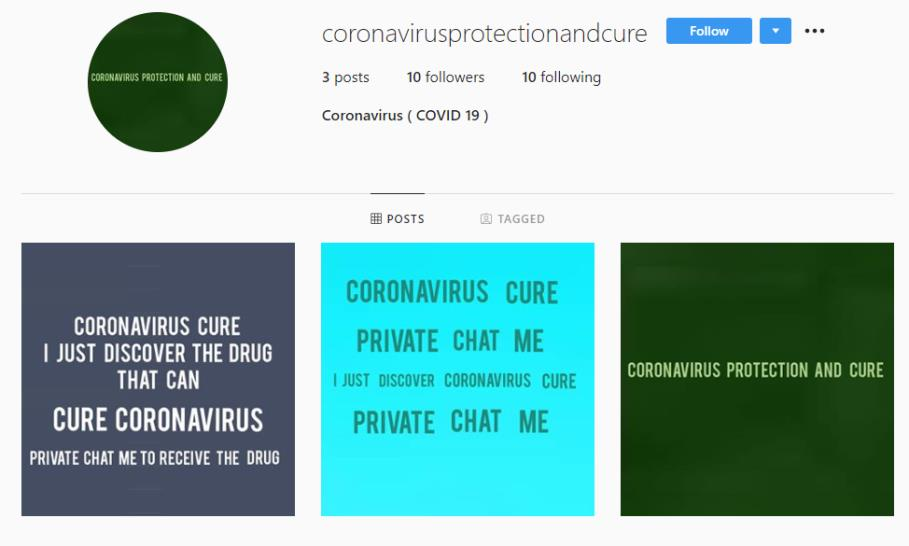
Coronavirus fake cure social media pages
Fake Shops
Fake shops have become prolific in recent years, providing criminals with a good alternative to phishing, where their attacks are more routinely disrupted. Fake shops claim to offer highly discounted luxury goods, typically for premium clothing, shoe or electronics brands. However, in reality they are simply a front to capture users’ payment information: after the victim completes the checkout process, they will be delivered counterfeit products, or possibly even no products at all.
In the wake of coronavirus, new fake shops have appeared offering protective products such as face masks, and detectors.
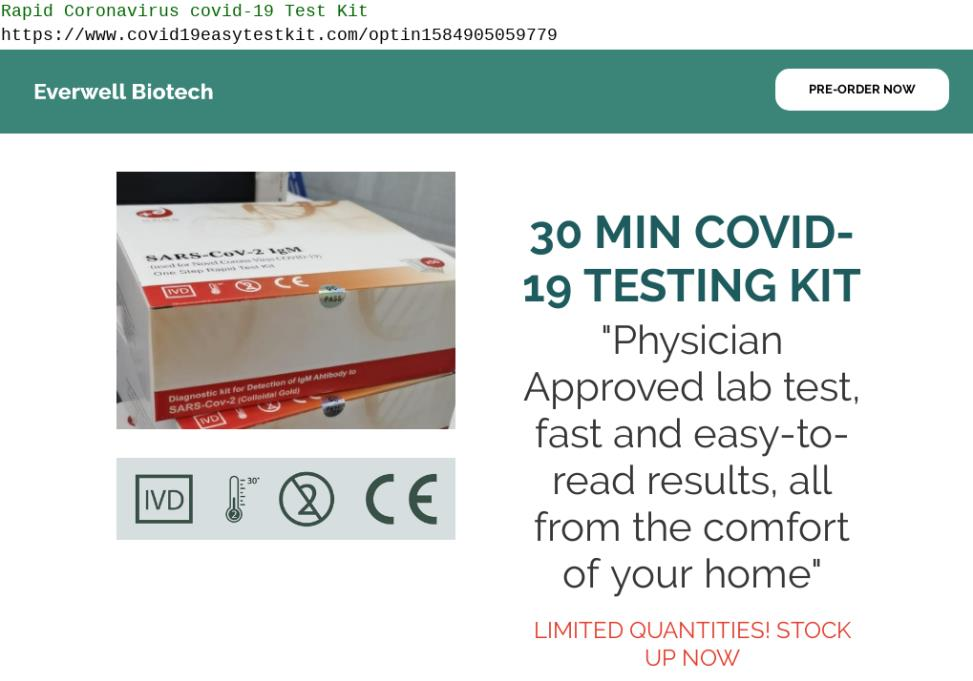
Coronavirus themed fake shop
Phishing Attacks
The World Health Organisation
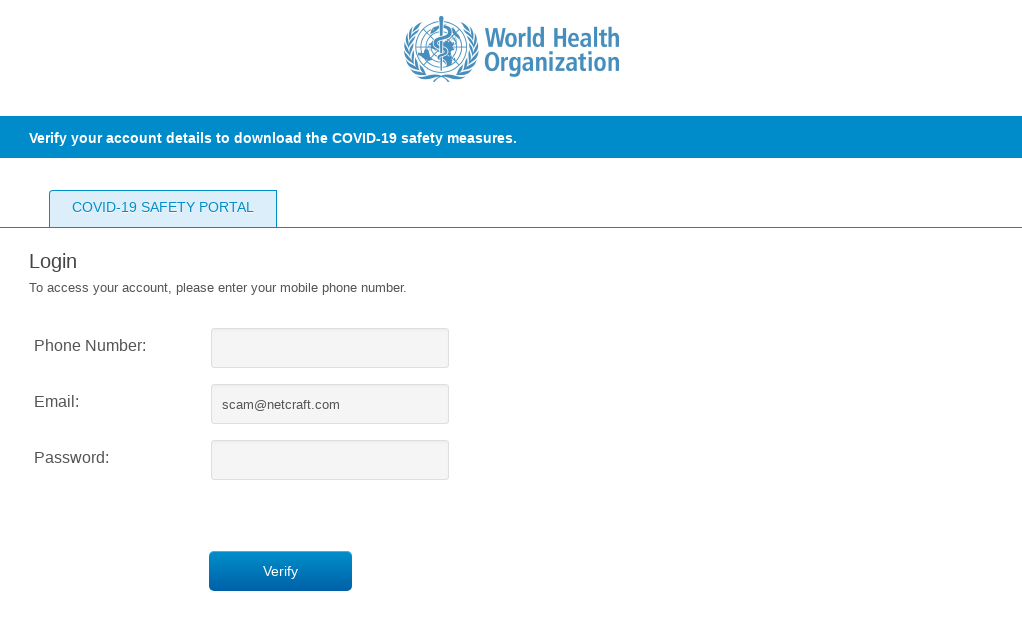
A number of phishing attacks have appeared impersonating the World Health Organization, offering access to a COVID-19 safety portal.

Coronavirus Phishing attack impersonating the World Health Organisation
Government Tax Refunds/Relief
As governments begin to offer various financial protections for citizens, we expect to rapidly see fraudsters launching fake sites for claiming money or tax relief. The following example impersonates the UK Government.
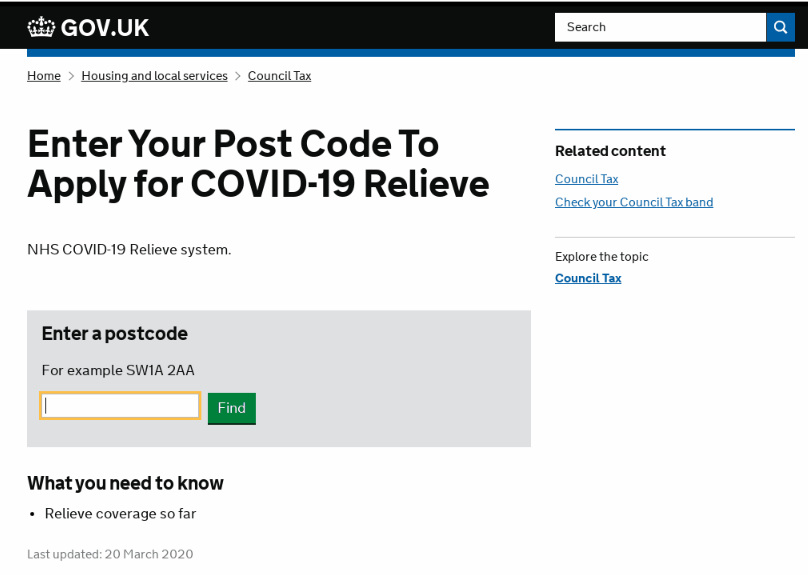
Coronavirus government tax refund scam
Office 365 lures
We are also seeing attacks mentioning Coronavirus that are attributed to other targets. The following screenshot shows a SharePoint-themed attack using a COVID-19 CURE lure to steal credentials for Microsoft Office 365, Google, Yahoo, as well as arbitrary email providers.
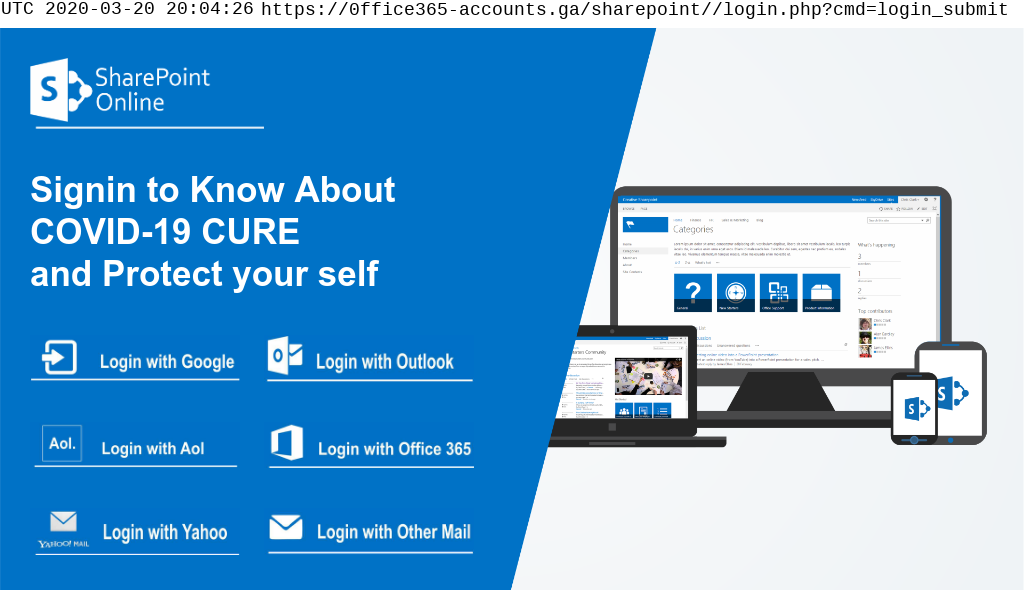
Coronavirus phishing attack using Office 365 lure
Following the ‘Login with Google’ link, then leads to a Google-themed sign-in page.
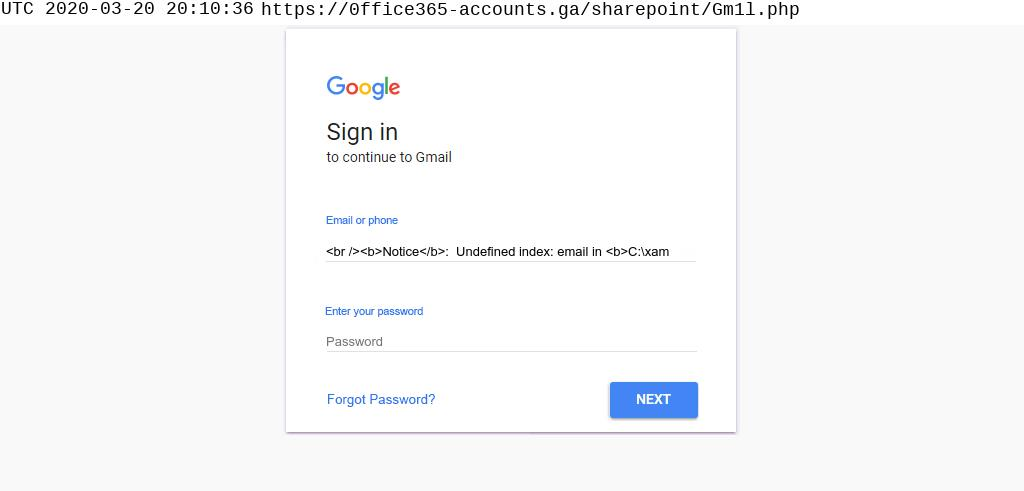
Coronavirus phishing attack redirects to fake Google Sign-in page
Other Microsoft-themed attacks redirect to cdc.gov after harvesting corporate Outlook credentials through a spoof Outlook Web Access page or serve the victim a malicious executable binary with the name ‘Interim Guidance for CoViD19′ from a fake Microsoft OneDrive page.
Supermarket Impersonations
As panic buying leaves supermarkets struggling to remain stocked, fraudsters have been seen targeting potential suppliers with requests for in-stock goods. The following example impersonates Sainsbury’s Supermarkets, a large UK retailer, suggesting payment within 30 days.
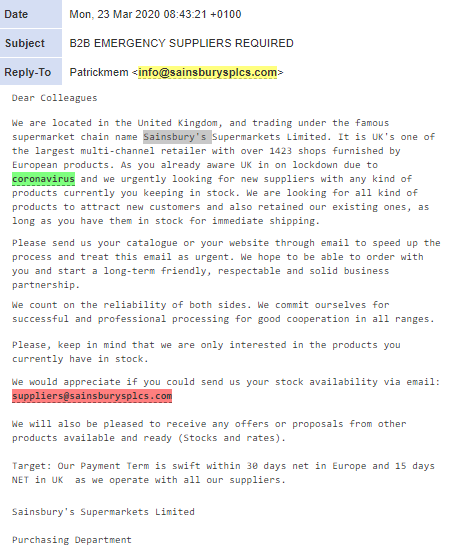
Coronavirus themed supermarket impersonation email
What’s Next
We expect attacks leveraging coronavirus to evolve rapidly. The attacks seen to date have required relatively simple changes by fraudsters on existing themes, and there are many more similar opportunities available for them to exploit. In particular we expect:
-
Fake shops to evolve from face masks and other protective products into fake vaccines/cures.
-
Investment scams to evolve, given the large amount of infrastructure involved, into Coronavirus scams. These scams currently involve fake news articles purportedly evangelised by widely respected people promoting get-rich-quick schemes.
-
Fake insurance claim emails.
-
Traditional phishing attacks against banks to make use of Coronavirus themed mails.