Just like Coronavirus itself, the Coronavirus-themed cybercrime it has spawned is quickly becoming a pandemic of its own. Cybercriminals have been quick to take advantage of the media attention on the story, using lures with a Coronavirus theme. Many of the attacks Netcraft has observed have used the fear and uncertainty surrounding the situation to trigger a response from their victims.
Netcraft has tracked Coronavirus-themed cybercrime since 16th March, shortly after it was declared a pandemic by the WHO. This post covers some of the trends Netcraft has observed since our previous post on the topic.
Coronavirus certificates
Analysis of certificate transparency logs for new certificates covering hostnames containing keywords “COVID” and “Coronavirus” shows increasing numbers of certificates are being issued for Coronavirus-themed hostnames.
Whilst some of the certificates included in the graph will be being used for legitimate purposes, many certificates – particularly those which have been registered since the outbreak started – are being used to spread disinformation, host fake shops and pharmacies, serve phishing websites and to disseminate malware.
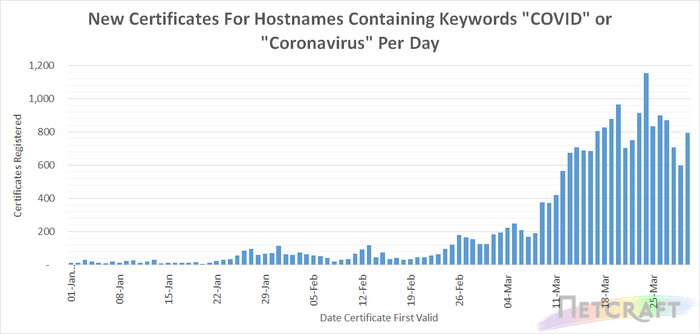
Numerous governmental, research and healthcare organisations are making use of organisation and EV certificates to provide higher levels of assurance to visitors to their website. Organisation and EV certificates (excluding Cloudflare organisation validation certificates which validate Cloudflare, not the website owner, as the organisation responsible for the certificate) account for 10.5% of certificates included in the chart above.
The more recent plateau in certificate issuance for Coronavirus related hostnames may in part be due to registrars, such as Godaddy and Namecheap, restricting the registration of these domains in response to the New York Attorney General’s request on March 20th. Richard Kirkendall, Namecheap CEO wrote to customers on March 25th stating:
we are actively working with authorities to both proactively prevent, and take down, any fraudulent or abusive domains or websites related to COVID19. This includes banning certain terms such as “coronavirus”, “covid”, and “vaccine” from our domain search tool so they cannot be purchased and used for abuse – Richard Kirkendall, Namecheap
Recently observed Coronavirus-themed threats
SMiShing
Netcraft has observed cybercriminals making use of SMS to deliver Coronavirus-themed lures to their victims. Many of the messages that have been sent within the UK have latched onto the news that the British Government will be providing support to individuals and companies who are struggling with the economic effects of the crisis.
Interestingly, whilst the SMS messages have a Coronavirus theme, in many cases, the phishing sites themselves have remained unchanged from the regular HMRC or bank phishing attacks Netcraft typically observes.
Follow the website hxxps://gocgglee[.]com/en to receive your tax refund due to the corona virus pandemic – Sent from Payback
[HMRC]: As a result of the current Coronavirus Outbreak, we have been forced to issue you with the full amount of your current tax refund. You have a pending tax refund of up to £450.47GBP. Please follow the link to calculate your claim. hxxps://taxuk-id[.]com – Sent from +44754XXXXX75
From HMRC: You are due a tax refund. Please fill out form at hxxps://hmrc-refund-covid-19[.]com/payment – Sent from Govt_UK
URGENT: The UKGOV has issued a payment of £258 to all residents as part of it’s promise to battle COVID 19. TAP here hxxps://uk-covid-19-relieve[.]com to apply – Sent from COVID19
[HMRC]: As a result of the current Coronavirus Outbreak, we have been forced to issue you with the full amount of your tax refund. You have a pending tax refund of up to £388.67. Please follow the link to calculate your claim. hxxps://tax-verifyuk[.]com – Sent from +44771XXXXX47
[HMRC]: As a result of the current Coronavirus Outbreak, we have been forced to issue you with the full amount of your current tax refund. You have a pending tax refund of up to £388.67. Please follow the link to calculate your claim. hxxps://taxuk-return[.]com – Sent from +44771XXXXX47
[HMRC]: As a result of the current Coronavirus Outbreak, we have been forced to issue you with the full amount of your current tax refund. You have a pending tax refund of up to £450.47GBP. Please follow the link to calculate your claim. hxxps://uktax-id[.]com – Sent from +44754XXXXX77
As Part of the NHS promise to battle the COV- 19virus , HMRC has issued a payment of £258 as a goodwill payment. Follow link to apply hmrc-cov19.payment.estrodev[.]com – Sent from CORONAVIRUS
BANKIA-ONLINE > Confirme la informacion de su ceuenta bancaria en> hxxps://bit[.]ly/SPAIN-COVID-19 , #751773 – Sent from COVID-19-SP
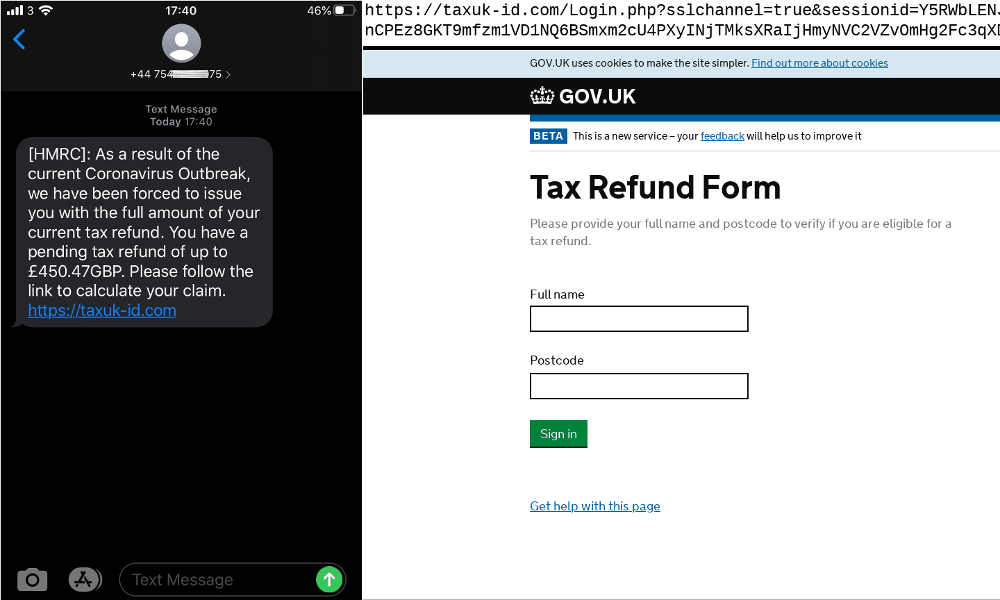
Coronavirus-themed SMiShing lure directing visitors to a standard HMRC tax refund phish
Fake shops using cloud platforms
Cybercriminals have set up a large number of Coronavirus-themed fake shops selling related goods which are in high-demand – including masks, hand sanitiser, gloves, and toilet paper – as well as individual testing kits and cures for COVID-19. At the time of writing the latter two are not available to the general public in many jurisdictions.
One trend that Netcraft has observed is the reliance on shopping cart cloud platforms for the deployment of Coronavirus-themed fake shops – in particular Shopify. This is in contrast with the pattern Netcraft typically observes in which fake shops utilise self-hosted platforms such as Zencart or Opencart. This may be due to cybercriminals, who have not previously been involved in this area, recognising the demand for such products but not having the infrastructure or expertise so choosing to leverage the easiest and cheapest option available. It could also be because they recognise that the window in which their fake shops can generate revenue is much smaller than usual, making the additional measure of self-hosting to increase the time they stay up unnecessary.
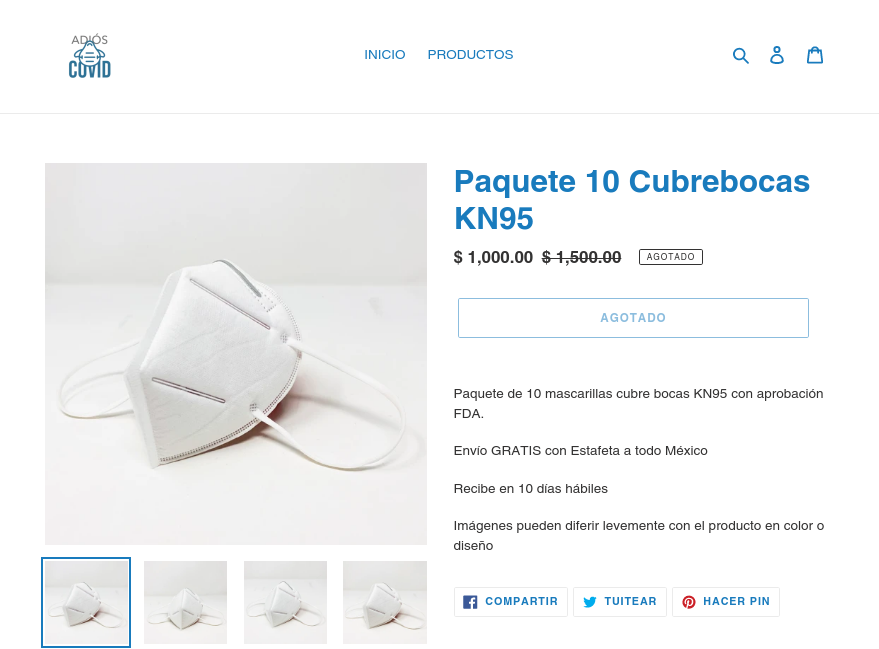
A recently created fake shop – hosted at Shopify and selling highly sought after face masks at an inflated price
Business Email Compromise & Phishing
In one incident cybercriminals used the compromised email accounts of a British employment charity to send out targeted emails with a Coronavirus-themed lure. The emails were especially convincing as the recipients are likely to be concerned about their job security during the ongoing crisis. Clicking the link in the email sends the victim to a Sharepoint page which purportedly offers a PDF for download. Victims who attempt to download the PDF are instead redirected to a Microsoft OneDrive phishing site which logs the victim’s email address and password before redirecting them to an unrelated PDF. In this instance, the cybercriminals made use of a HTML sandbox (codesandbox.io) and image sharing site (imgur.com) to host their attack. Leveraging these free services makes launching a campaign cheap and easy for the criminal.

Phishing attack impersonating Microsoft OneDrive which victims arrive at in the belief they will receive advice about their job
Password stealing malware
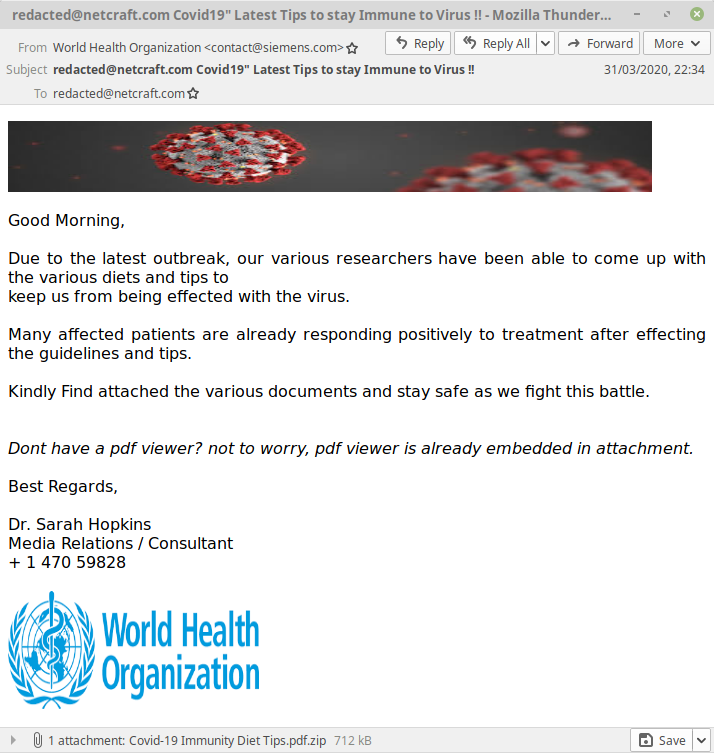
In one malware campaign, Netcraft observed, an email claiming to be from the World Health Organisation contains an attachment enticingly named “Covid-19 Immunity Diet Tips.pdf.zip”. The email claims the attachment contains “various diets and tips to keep us from being effected (sic) with the virus.” and that “Many affected patients are already responding positively to treatment after effecting the guidelines and tips.". However, anyone who opens the attachment will find their computer infected with another kind of virus – Agent Tesla. Agent Tesla is a password stealer capable of retrieving credentials saved in the victim’s web browser, email and FTP clients as well as logging all their keystrokes.
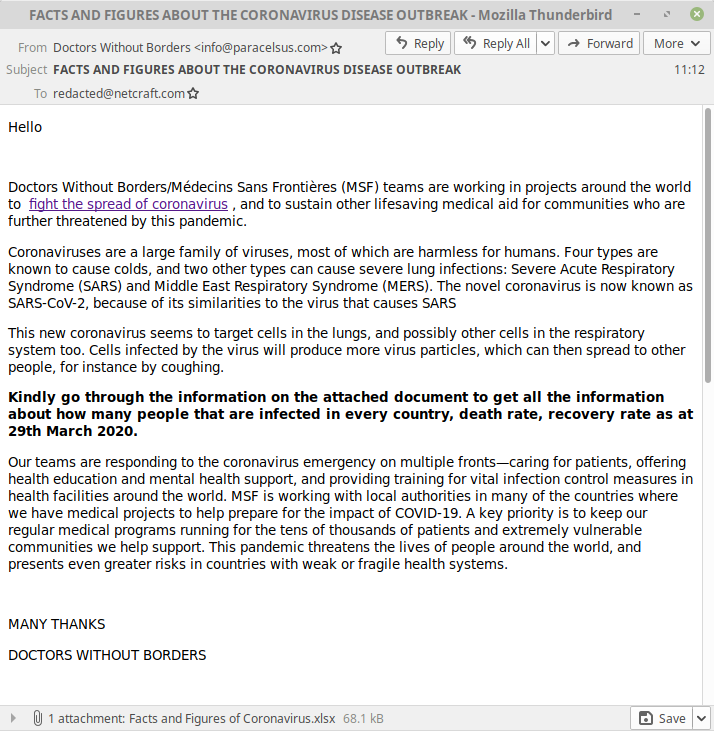
Meanwhile, a malware campaign posing as Doctors without borders includes a Microsoft Excel spreadsheet named “Malicious Facts and Figures of Coronavirus.xlsx” under the false pretence that it contains Coronavirus infection statistics. When in reality the spreadsheet exploits a buffer overflow in Microsoft’s Equation Editor to download and install an encrypted copy of NanoCore RAT from Google Drive. NanoCore is a Remote Access Trojan capable of stealing personal information including passwords and payment information as well as secretly recording the user’s audio and video.
Protecting yourself and others from cybercrime
Netcraft’s browser extensions and mobile apps provide protection against online threats, such as phishing, SMiShing and malicious JavaScript. To help protect the internet community you can also report cybercrime using the extensions or report.netcraft.com.