Criminals are running massive dedicated phishing campaigns against online dating sites, marking an interesting – but not unusual – shift in focus from the traditional phishing targets such as banks and other financial institutions. The most recent attack used a single compromised website to host hundreds of fraudulent PHP scripts, most of which were designed to steal usernames and passwords from users of the most popular dating sites.
The online dating sites targeted by the latest attack include match.com, Christian Mingle, POF (PlentyOfFish), eHarmony, Chemistry.com, SeniorPeopleMeet, Zoosk, Lavalife, amongst others. Only eight of the 862 fraudulent scripts on the server targeted banks.
It is likely that the criminals who steal accounts on these sites will go on to use them to commit online dating fraud — many dating sites only allow messages to be exchanged with other users after a subscription fee has been paid; by compromising existing paid accounts, the fraudsters can reduce their traceability by avoiding the need to make payments.
Online dating fraud is often orchestrated by criminal gangs who use fake profiles to trick victims into developing long distance relationships. Once the fraudsters have gathered enough sympathy and trust from a victim, they will exploit this by claiming they need money to pay for travel costs, or to afford medical treatment for a family member. After the money has been stolen, the criminals will make up further reasons why they need more money. In some cases, the fraudsters blackmail their victim into sending money – if the victim has sent any explicit photos or videos to the criminals, they may threaten to send them to the victim’s friends and family.
The amount of money involved in these scams can be considerable. In 2011, a woman in Britain was tricked into sending more than $59,000 to a pair of fraudsters who pretended to have inherited millions of dollars from a military friend in Nigeria. The fraudsters – who were actually a mother and daughter in America – managed to net more than a million dollars before being jailed in 2013.
While many online dating sites take measures to identify fake profiles, phishing for genuine established accounts gives fraudsters the edge. If a legitimate profile has been in active use for several months without cause for concern, then compromising this profile will allow the fraudster to benefit not just from the plausible appearance of the profile, but also take over several ongoing conversations. The real owner of the hijacked account will have already done the hard bit by establishing dialogues with other members on the site, possibly gaining enough trust to allow the fraudsters to strike immediately with success.
The latest attacks make use of a phishing kit which contains hundreds of PHP scripts, configured to send stolen credentials to more than 300 distinct email addresses. More than half of these addresses used the yahoo.com domain, while gmail.com was the next most common choice. Although most of the fraudster’s scripts target online dating sites, some of them are also designed to steal credentials from users of these webmail platforms. Email accounts are often shut down after the provider notices they have been used for fraudulent purposes, so ensuring a fresh supply of compromised accounts gives fraudsters the opportunity to send even more phishing emails before the accounts get closed.
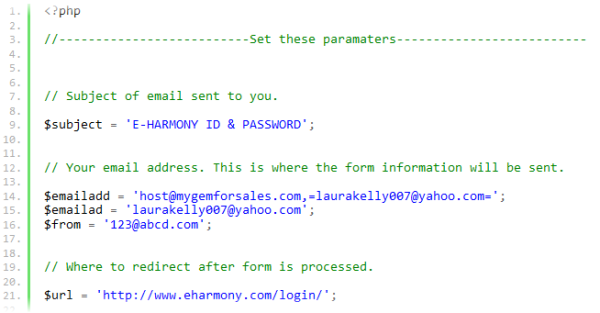
An attacker would typically deploy the phishing kit by uploading a zip file to a compromised web server and unzipping the tree of contents into a writable directory. Similar kits uploaded over the past few months have used various file names, such as moving.zip, send.zip, orokionline.zip, amioroki.zip and samoroki.zip. Each script within these kits is very similar in terms of functionality — they simply collate a set of POST parameters into the body of an email message, and then send it to two or more email addresses. The subject of the email is modified to describe what type of credentials are in the email (e.g. "MATCH ID & PASSWORD"), and after the emails have been sent, the victim is redirected to an appropriate URL on the target website, such as http://www.match.com/login/login.aspx?lid=2.
Each compromised server which hosts these scripts acts merely as a "dropsite" in the fraudsters’ phishing campaigns. Rather than displaying any phishing content, the server simply accepts values that have been submitted from elsewhere, such as a form hosted on another website or within a phishing email. The victim is then immediately redirected to the legitimate website, most likely without realising that his credentials have just been transmitted to a different website.
Some of the scripts are also designed to steal credentials from Photobucket users, possibly so the fraudsters can host photos and other images to further their scams. It is not unusual for fraudsters to encourage their victims to migrate to instant messaging software or even text messages instead of continuing to chat on a dating site, which could be monitored to prevent such fraud.