Key Data
- darcula-suite represents a significant shift in criminal capabilities, reducing the barrier to entry for bad actors to target any brand with complex, customizable phishing campaigns.
- Novel use of Headless Chrome and browser automation tool allows even non-technical criminals to quickly and easily clone any brand’s legitimate website and create a phishing version.
- The latest version of darcula-suite is expected to launch in mid-February.
- Since March 2024, Netcraft has detected and blocked more than 90,000 new darcula phishing domains, nearly 31,000 IP addresses, and taken down more than 20,000 fraudulent websites on behalf of Netcraft clients after first exposing darcula.
Overview
The criminals at darcula are back for more blood, and they mean business with one of the more impactful innovations in phishing in recent years. The new version of their “Phishing-as-a-Service” (PhaaS) platform, darcula-suite adds first-of-its-kind personalization capabilities to the previously built darcula V2 platform, using Puppeteer-style tools to allow criminals to build advanced phishing kits that can now target any brand with the click of a button.
In March 2024, Netcraft analysts exposed the innovative darcula phishing platform, created with advanced capabilities and pre-built phishing content aimed at many of the world’s largest brands, most notably the United States Postal service (USPS). The criminal group behind darcula is set to launch its next wave of innovation in February 2025 with darcula-suite.
The darcula V2 platform had a major impact on more than 200 brands worldwide, which the criminal organization targeted with pre-built phishing kits in its darcula library. For example, Netcraft has identified and blocked more than 95,000 malicious darcula URLs — and taken down more than 20,000 malicious domains on behalf of clients — over the last 10 months.
The combination of traditional phishing and smishing with AI-driven improvements make phishing a lucrative business. And, platforms like darcula-suite continue to make criminal behavior more accessible than ever before. With this new suite of tools, less technical criminals can now build do-it-yourself (DIY) phishing kits that target any brand with the click of a button — building on previously launched darcula V2 functionality that drove a massive scale of threats since its launch last year.
Within this post, we’ll examine advanced tactics embedded within darcula-suite (darcula 3.0), the differences between this version and the previous PhaaS platform, and why intervention and advanced detection are critical to disrupt criminal advances like this.
Darcula V3: DIY Phishing of Any Brand
Next-Generation Phishing
It seems we’ve all had them: the text that we have a package waiting for us and all we need to do is reply yes and click the link, right? But, these limited phishing kits, like fake packages from USPS or Royal Mail, and the frequency that consumers have received them, have helped the public get smart on these common phishing attempts.
However, crime doesn’t sleep and the darcula team, like any business, is looking to increase the return on investment for its criminal customers by expanding the ability to target any brand in the world.
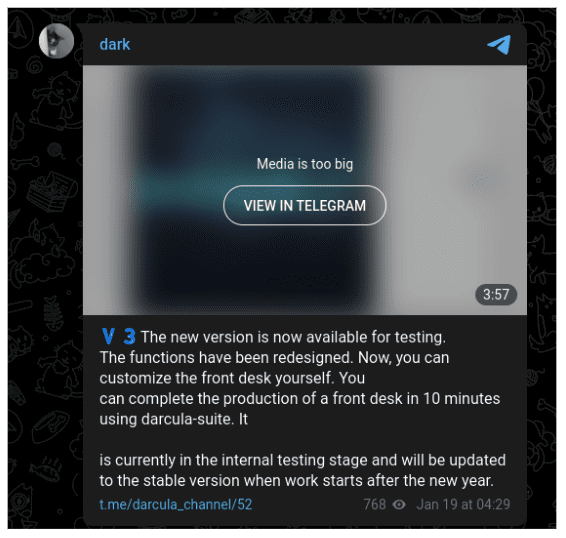
Figure 1 – Telegram announcement of darcula V3, translated from Chinese into English
First revealed on Telegram, the darcula team is promoting a new DIY approach to creating new phishing kits for any brand quickly and easily.
Phishing Kit Generation — to Target Any Brand
From our analysis, the biggest innovation baked into the darcula-suite is the ability for any user to generate a phishing kit for any brand, regardless of technical ability or prior resources. These on-demand, DIY phishing kits represent a massive risk to brands that were not previously included in darcula V2’s library. Now, any brand is vulnerable to attacks at the hands of the darcula threat actor ecosystem.
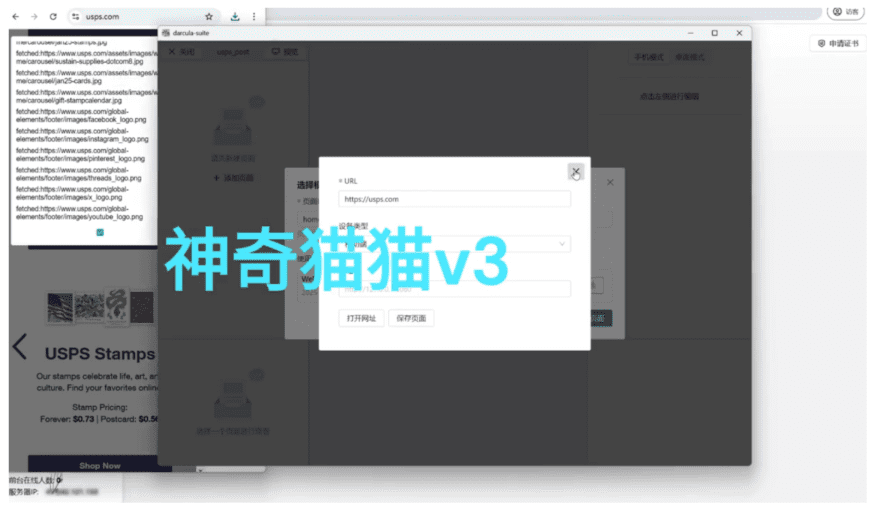
Figure 2 – darcula-suite orchestrating a browser to visit any provided URL and extract the assets
Shown above is a look at the interface that allows a fraudster to insert any URL, allowing them to automatically generate a phishing kit for any brand. How easy is it? Let’s take a look.
Steps to build a darcula-suite phishing kit:
- Insert the URL for the impersonated brand.
- The platform uses a browser automation tool, like Puppeteer, to export the HTML and all required assets.
- Simply select the HTML element to replace and inject the phishing content.
- Choose a new form from a selection of scam templates, e.g. asking for payment details or sensitive information.
- Restyle the phishing form to match the look and feel of the branded landing page.
- Trigger the generation of separate pages for the initial lure page, address input, card details, and two-factor authentication code.
- Export the phishing kit as a “.cat-page” bundle.
- Upload the “.cat-page” bundle to a darcula admin panel.
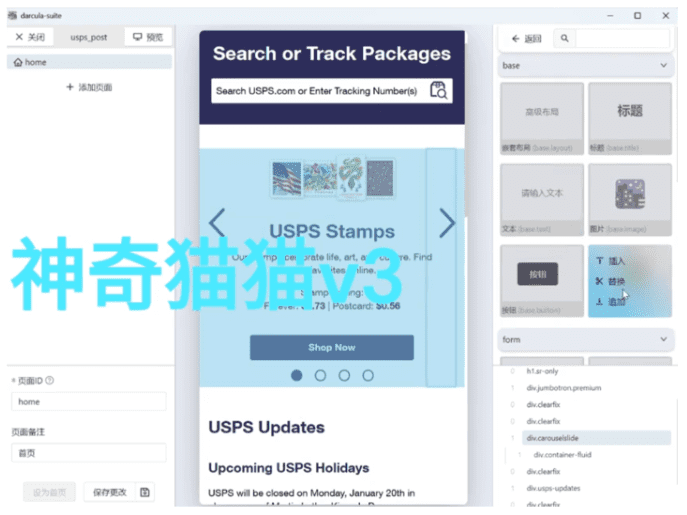
Figure 3 – Sample mobile landing page generated by darcula-suite
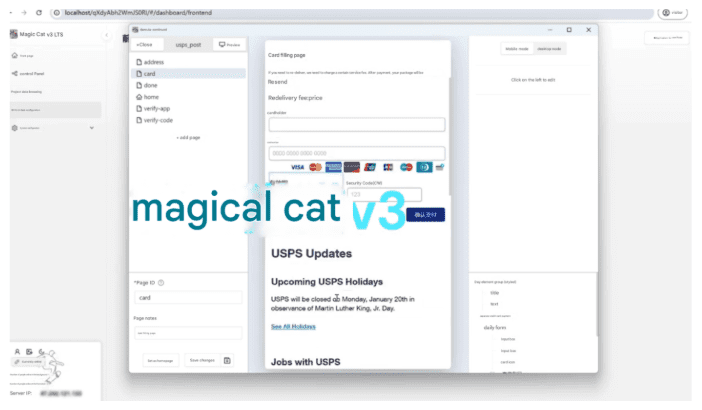
Figure 4 – An injected credit card form. The text in this frame has been machine-translated into English
As you can see, darcula-suite’s process makes the creation of everything a fraudster needs to deploy a phishing campaign all too easy.
Improved Admin Dashboards Makes It Even Easier for Bad Actors
Like any Software-as-a-Service product, the darcula-suite PhaaS platform provides admin dashboards that make it simple for fraudsters to manage their various campaigns. Here’s a look inside the admin dashboards.
Figure 5 – The darcula-suite admin panel login page
Letting the Cat Out of the Bag: darcula’s Admin Panel
Previous versions of darcula and its Telegram channels have become synonymous with the criminal organization’s use of cat imagery and naming. That trend continues in this iteration with phishing kits generated to .cat-page destinations.
Once generated, these kits are uploaded to another platform where criminals can manage their active campaigns, find extracted data, and monitor their deployed phishing campaigns.
To install the admin panel, a threat actor runs a script at v3[.]magic-cat[.]world/install.sh, which runs Docker images from darcula’s own Docker registry: registry[.]magic-cat[.]world/v3/web and registry[.]magic-cat[.]world/v3/api.
Once inside the admin panel, Netcraft investigators were able to explore how these kits are made, the advanced deception techniques used, and what can make them vulnerable to detection. These include:
| Deception Technique | Disruption Method |
|---|---|
| Unique deployment path for each campaign to hide deployments from hostname scanning | While Certificate Transparency logs and Passive DNS data can be used to find and identify hostname-level threats, darcula v3 hides beneath a randomly-generated path, preventing hostname-level analysis. To detect these unique deployment paths, organizations must have access to the distribution point of malicious URLs. |
| Risky IP filtering allows fraudsters to block IPs from accessing content | Requires a global proxy network to fetch fraudulent content in certain geographies and from unknown IPs |
| Crawl filtering stops site from being discovered by web crawlers | Non-crawling techniques such as abuse box monitoring, reporting communities, and other forms of insight can expose criminal efforts |
| Unallowed device types is often used to block non-mobile devices (commonly used for automated detection) | In connection with a global proxy network on varying device types used to fetch content, bypassing this deception |
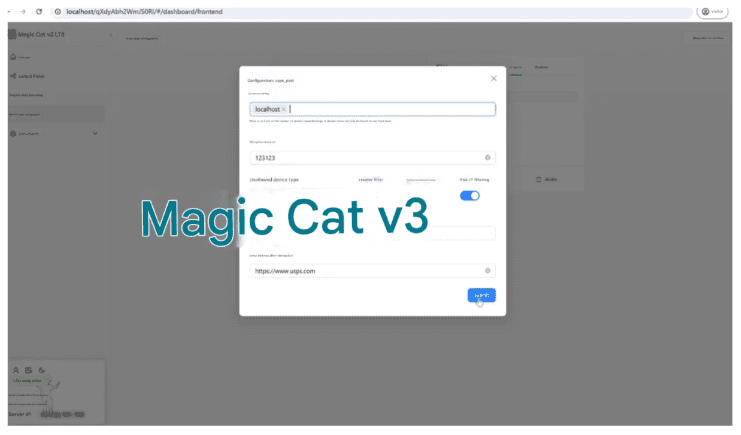
Figure 6 – darcula-suite admin panel showing the interface for configuring IP address, crawler and device type blocking
The new admin panel also provides fraudsters a simplified user interface for managing credit cards, stolen credentials, active campaigns, and other details. These dashboards are not a crudely developed PHP script either — they are built on enterprise-grade systems including Docker, Node, React, SQLite, and various third-party NPM libraries. This attention to detail isn’t necessarily an effort to legitimize darcula but rather, make the experience easier and more accessible, just like any other SaaS platform.
Putting Stolen Cards to Work
Once details from stolen cards are pulled from phishing campaigns, darcula-suite takes it a step further by providing the user with the ability to generate an image of the victim’s card which can be used to scan and add it to a digital wallet. These cards are often loaded to burner phones and then sold by darcula criminals.
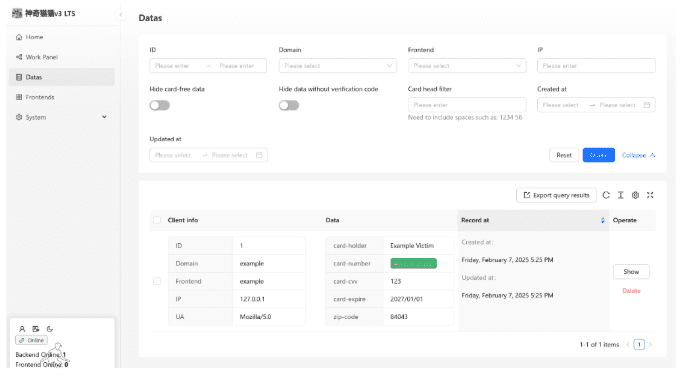
Figure 7 – Platform card generation
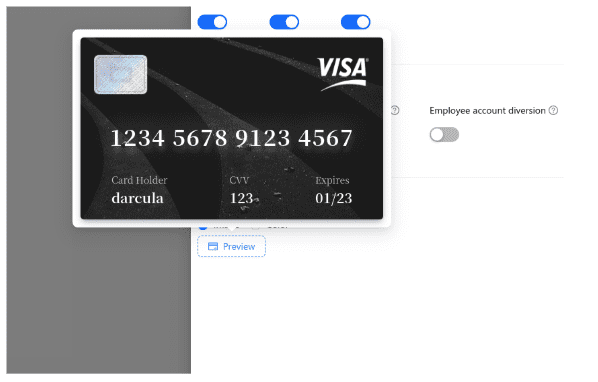
Figure 8 – Example of a virtually-generated card from stolen card details
This behavior has been confirmed by fraudsters who publicize burner phones pre-loaded with up to 20 stolen cards per device via a Telegram chat adjacent to darcula.
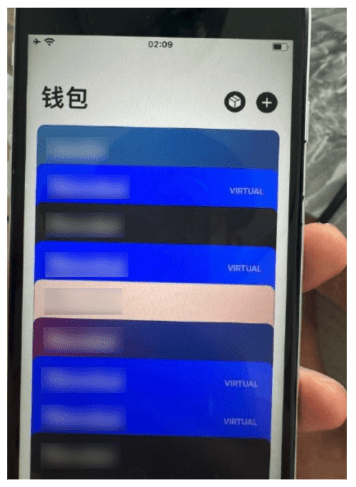
Figure 9 – Burner phone publicized on a darcula related Telegram channel with 20+ loaded cards at hXXps://t[.]me/xxhcvv/1680
Performance Dashboards and Notifications
darcula-suite features a full dashboard of aggregated performance statistics to show criminals the success of their campaigns.
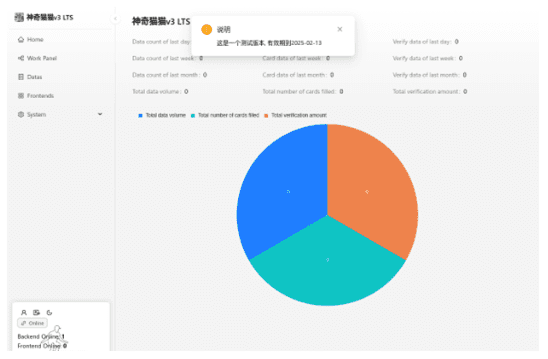
Figure 10 – darcula-suite performance dashboard
Additionally, like we saw in the Doggo (Xiū Gǒu) PhaaS, criminals can receive notifications via a Telegram integration after a scam recipient falls victim.
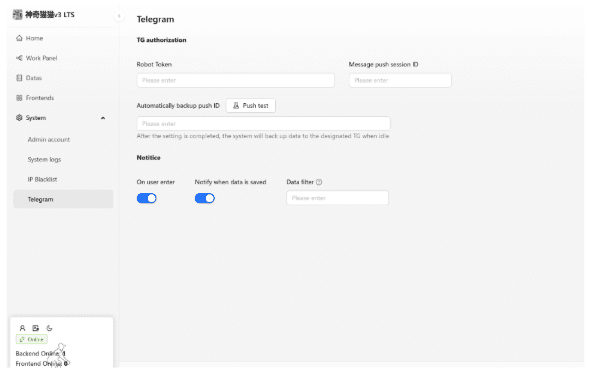
Figure 11 – Telegram notification integrations
Darcula 2.0: A Major Innovation and the “Suite” Foundation
The full-service phishing kits supported with darcula version 2 significantly reduced the barrier to entry for less technical criminals. They also use sophisticated defenses to enable criminals to avoid detection, including:
- Each deployment of darcula can hide behind a unique subdirectory
- IP blocking measures to limit access from cybersecurity companies
- User agent blocking used to stop automated scrapers, such as Google’s crawlers and other naïve monitoring efforts
- Client-side page rendering with React, which needs JavaScript to load, requires monitoring with a headless browser — an advanced detection capability that prevents detection by some tools and providers
- Users are encouraged by darcula to hide the origin server via CDN providers such as Cloudflare
Despite these advanced protections, phishing sites created using darcula 2.0 are not invincible. By leveraging advanced worldwide proxy networks, novel classification methodologies, and various other tactics, Netcraft’s technology and researchers have successfully bypassed these defenses. In the last 10 months, Netcraft’s team has found hundreds of thousands of threats and deployed successful countermeasures, including:
- 30.9K blocked IP addresses
- 96.6K blocked domains
- 20.2K phishing sites taken down for Netcraft clients

Figure 12 – darcula V2 phishing templates or phishing kit library (machine translated from Chinese
While darcula V2 was powerful, the phishing kits offered were pre-built with specific brands in mind, including more than 200 templates covering brands in over 100 countries. Version 3, called the darcula-suite, takes a new approach to effortlessly retheme a phishing attack to target any brand.
What’s Next: Darcula-suite Launch Timing and Downloads
Netcraft expects the new suite to launch in mid-February 2025, with user testing in progress today. The test version that Netcraft investigators have used for this analysis will likely be replaced in the coming weeks or days with the final launched version.
And, criminals are already testing this new platform in advance of its launch. Because the container images used to run the admin panel are publicly available at registry[.]magic-cat[.]world, Netcraft was able to get a rough estimate of the number of individuals already exploring this test suite. The pull count of the API image has increased by more than 100% and the web image by more than 50% from February 5 to February 10.
Protecting Yourself – and Your Organization – from darcula
As in all scam and fraud cases, consumers can protect themselves by being wary of messages and links sent from unrecognized senders. While the fraud hallmarks of bad grammar and spelling errors continue to decline as generative AI becomes more prevalent among bad actors, offers and messages that are “too good to be true” or require urgent action should continue to be treated with significant skepticism. Android and iOS users can further protect themselves by using Netcraft’s apps, which block phishing pages and other malicious sites.
Organizations can protect themselves by taking note of the deception techniques and disruption methods outlined above. In addition, Netcraft protects brands in 100+ countries and performs takedowns for many of the largest brands in the world.
To find out how Netcraft can protect your organization from the threat of darcula-suite and other phishing cyber attacks, you can request a demo by visiting https://www.netcraft.com/book-a-demo/, or find out more by visiting https://www.netcraft.com/platform/.