Network Solutions allowed a fraudster to register a deceptive domain name earlier this week: secure-chaseonline.com. Network Solutions also issued a valid SSL certificate for the domain, which was used for a phishing attack which targeted customers of Chase Bank.
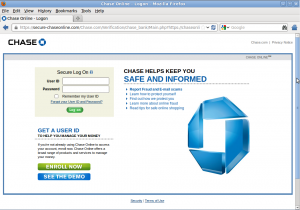
Phishing attack targeting Chase bank on secure-chaseonline.com
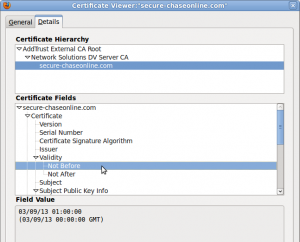
The phishing site added further credibility to the attack by using an encrypted HTTPS connection. The fraudster obtained a domain-validated SSL certificate from Network Solutions, and, as with the domain, it was valid for one year from 3rd September 2013.
The SSL certificate used on secure-chaseonline.com
Although opportunities were missed to prevent the suspicious domain name being registered and the corresponding SSL certificate being issued, the certificate used by the site does at least support OCSP, which can allow the issuer to instantly revoke the certificate. However, the efficacy of this mechanism largely depends on which browser the victim is using, and how it has been configured. For example, Firefox — which does performs OCSP checks by default — will only display content from https://secure-chaseonline.com if the certificate has not been revoked. Google Chrome, on the other hand, does not perform such checks by default (for non-EV certificates).
However, as Network Solutions was also the registrar of the domain, it would have been more effective to simply suspend the domain, which is what appears to have happened yesterday:
No match for "SECURE-CHASEONLINE.COM". >>> Last update of whois database: Thu, 05 Sep 2013 12:56:58 UTC <<<
The fraudulent SSL certificate was later revoked — the certificate’s serial number can be found on Network Solutions’ certificate revocation list.
The CA/Browser Forum’s Baseline Requirements for the Issuance and Management of Publicly-Trusted Certificates [PDF] says that certificate authorities SHALL subject high risk requests — which includes names at high risk of being used in a phishing attack — to further scrutiny prior to issuance. Netcraft’s Domain Registration Risk service is ideal for both domain registrars and certificate authorities, as it judges the likelihood of a new domain being used for fraudulent activities. It identifies domains which are deceptively similar to legitimate websites run by banks and other institutions that are commonly targeted by phishing attackers.
While some phishing attacks can be identified prior to domain registration or SSL certificate issuance (such as the one described above), a significant proportion of phishing attacks make use of compromised web sites (often exploiting vulnerabilities in commonly deployed software platforms, such as WordPress). Netcraft can alert registries, SSL certificate authorities, or registrars and hosting companies of phishing sites discovered using their infrastructure to conduct a phishing attack.
Please get in touch (sales@netcraft.com) if you would like to try out this service or for subscription information.