Fraudsters are exploiting loopholes in the presentation of ads by major search engines in order to lure victims to phishing sites. Searching for “blockchain”, the name of a popular Bitcoin wallet provider, caused deceptive ads to be displayed at the top of search results pages from Google, Bing, Yahoo, and DuckDuckGo. In contrast to the traditional approach of sending emails indiscriminately, links to phishing sites in search engine ads may be much more convincing, especially when the domain they are impersonating is displayed as the destination.
With more than 1.7 million wallets, Blockchain.info is the most popular online Bitcoin wallet. Blockchain’s My Wallet service allows users to send and receive payments in Bitcoins. When signing up, users are reminded that they must remember their passwords, as forgotten passwords cannot be recovered and will result in the loss of all Bitcoins stored in the wallet. These passwords are exactly what the fraudsters are after.
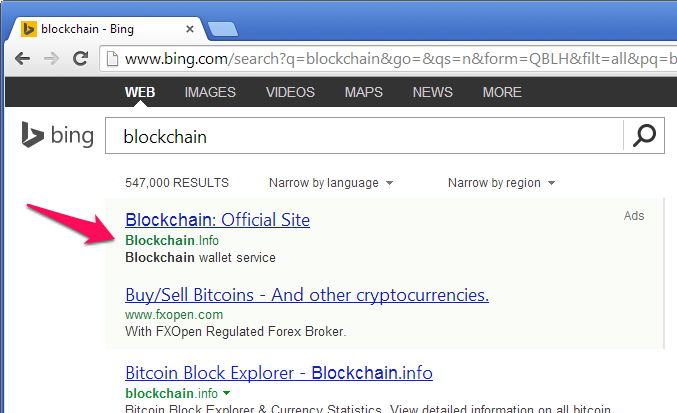
The above screenshot shows the results of searching for “blockchain” on Bing. The first link on the page is an ad, supposedly for the official Blockchain wallet service at Blockchain.info. However, clicking on this link actually takes victims to a phishing site under blockchaino.info (note the additional ‘o’ character).
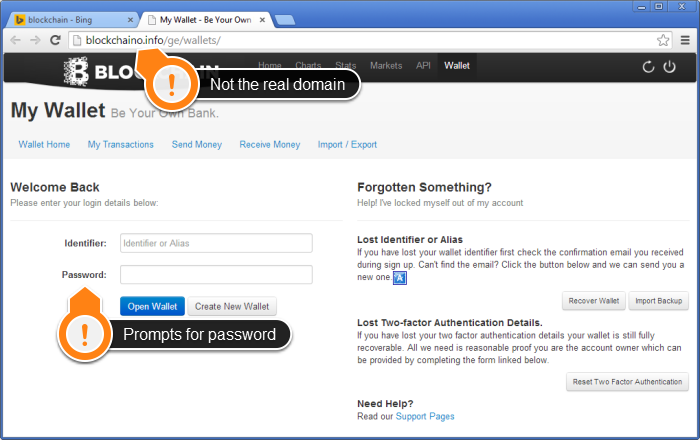
The phishing site at blockchaino.info immediately prompts a victim to enter his identifier and password, whereas the real Blockchain website only prompts for the user’s identifier. Blockchain’s security recommendations make it clear that the real Blockchain.info will never ask you for your password: “We NEVER need it and we NEVER want it”. As soon as the fraudster has tricked the victim into giving up the required information, they “sweep the funds away“.
This type of attack is likely to be extremely effective, as the ad displays the same domain name as the site it is targeting, and it is the first link to appear in the search engine results page. Some users may not realise that it is an ad, and instead believe that it is the top organic result. Showing the wrong display URL (green text) is forbidden by most ad networks’ policies; however, the fraudsters have evidently managed to bypass these restrictions. Without strict enforcement, the ability to specify the displayed destination leaves such advertising open to fraud.
However, strict enforcement of destination URLs may alienate a search engine’s customers — advertisers may use third-party services to manage their advertising and track clicks. These customers will rely on being able to display the final URL despite redirecting via a third-party service before reaching the target site. The use of redirects makes enforcement of any display policy difficult, as there is no guarantee that the target of the redirect will remain constant after the ad has been approved, or that the redirects presented to the search engine are the same as those presented to end users.
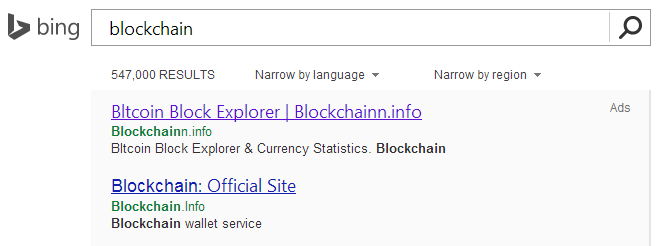
Other Bing ads directed victims to different Blockchain phishing sites, all of which used deceptive hostnames such as blockchain-info.itconflux.com, blockchain.info.pl and bllockchain.info.pl, but did not use the display domain of the site they were impersonating, blockchain.info.
It’s not just Bing’s search engine that has been affected by this phishing campaign. The search ads displayed at the top of Bing search results can appear anywhere on the Yahoo Bing Network. This means that the same fraudulent ads also appear when a victim searches for Blockchain on Yahoo.com. Similar phishing ads are also displayed on the DuckDuckGo search engine, which syndicates its sponsored links from the same network.
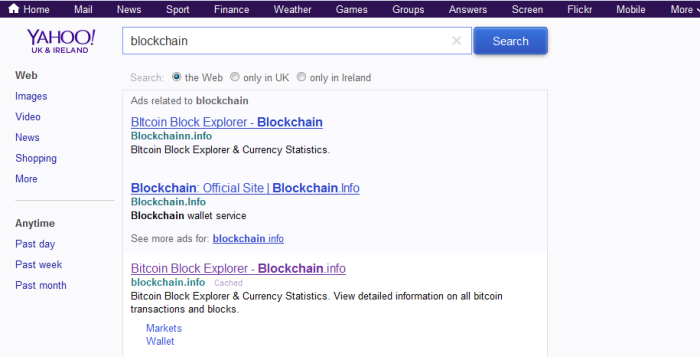
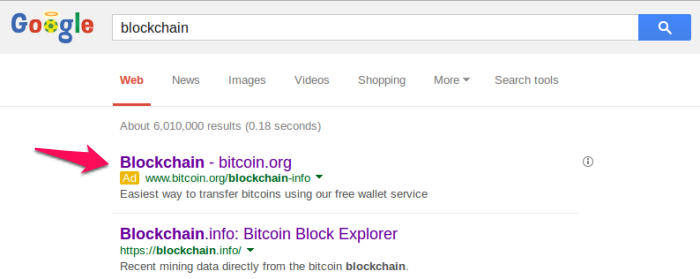
And it is not just the Yahoo Bing ad network which is being exploited by phishers — search giant Google displayed the following phishing ad on its search results pages:
However, it’s not necessarily game over if a victim’s password has been stolen. If a Blockchain user has chosen to enable two-factor authentication via SMS, Yubikey or Google Authenticator, the fraudster will be unable to access the wallet at a later date unless he also has access to the victim’s physical two factor authentication device (e.g. phone or Yubikey).
All of the sites involved in these attacks against Blockchain were blocked in Netcraft’s phishing site feed, which allows third-party developers to integrate anti-phishing services into their products. Some of the domain names used in these attacks were very similar to the real blockchain.info domain. Netcraft’s Fraud Detection service helps brand owners pre-emptively identify these types of fraudulent domain registrations, giving an opportunity to take action against the registrants, possibly before the attacks have even started.