Cybercriminals always seek to cash in on current affairs to lend credibility to their attacks, and the conflict in Gaza is no exception. Netcraft has detected over $1.6M in cryptocurrency being transferred to accounts associated with this fraud.
In donation fraud, cybercriminals trick users into donating to what appears to be a legitimate cause using numerous tactics. This includes referencing current events, encouraging readers to act urgently, and by using emotive language (or situations). The criminal’s goal is to pressure the victim into acting impulsively and sending funds without due diligence.
This blog post takes a detailed look at how opportunistic cybercriminals have made use of the conflict to carry out donation fraud within days of its start. In nearly all cases we have seen, these campaigns solicit “donations” via cryptocurrency. Many even go one step further and drain the entire crypto wallet of their victims through the use of crypto drainers.
The criminal exploitation of the situation is turbulent, with campaigns starting and stopping and site contents changing constantly. Some sites have had their fraudulent content completely replaced less than a week after they were initially observed by Netcraft.
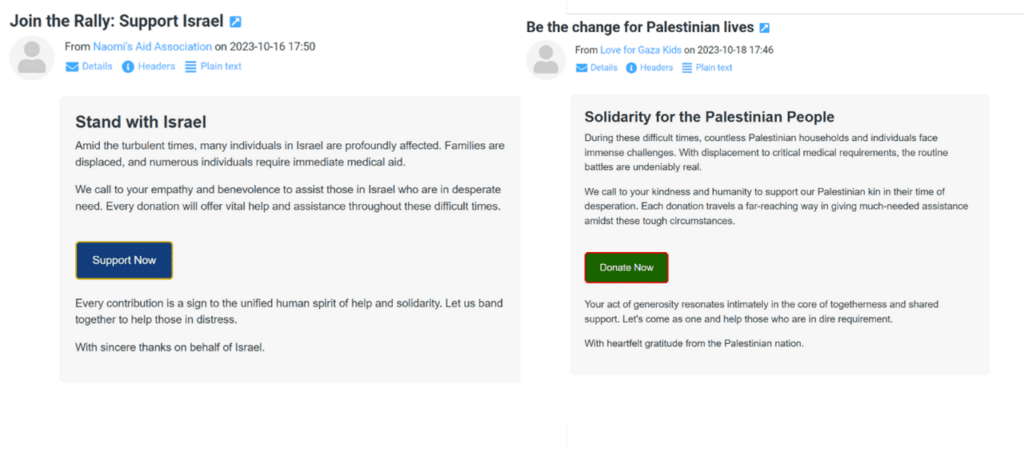
Two Donation Fraud emails taking advantage of the conflict, soliciting donations for Israel and Palestine respectively. Both destination sites send funds to the same cryptocurrency wallet, suggesting indiscriminate targeting by the threat actor.
Rise of the crypto drainers
Opportunistic donation fraud often requests “donations” to be made in cryptocurrency. At the start of the Ukraine war, several large-scale email campaigns impersonated targets such as President of Ukraine Volodymyr Zelenskyy, the British Red Cross, and the UK Prime Minister’s Office. Regardless of the impersonated party, the emails asked for donations to be made to one or more cryptocurrency addresses listed directly in the text. This form of donation fraud relies on the victim having the knowhow and willingness to send the cryptocurrency to the listed address. There is some precedent for legitimate donations to be made this way: on 26th February 2022 Ukraine solicited donations in cryptocurrency on X (formerly Twitter).
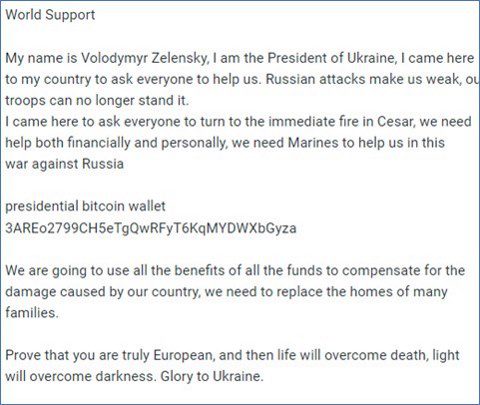
Donation fraud email impersonating Volodymyr Zelenskyy, asking for donations to be sent to a listed Bitcoin address
More recently, Netcraft analysis shows criminals make use of crypto drainers as part of the donation fraud. Cryptocurrency drainer scams, or crypto drainers, are a type of website-based attack that attempts to trick users into sending the contents of their cryptocurrency wallet to a fraudster. Crypto drainers take advantage of victims who have connected their cryptocurrency wallet to their browser to interact with Web3 applications. The convenience of connecting your wallet to the browser is double-edged: it reduces friction in authorizing all transactions, including unwanted ones generated by crypto drainers. The scam usually results in the victim’s wallet being completely emptied (or ‘drained’) if they authorize the transaction.
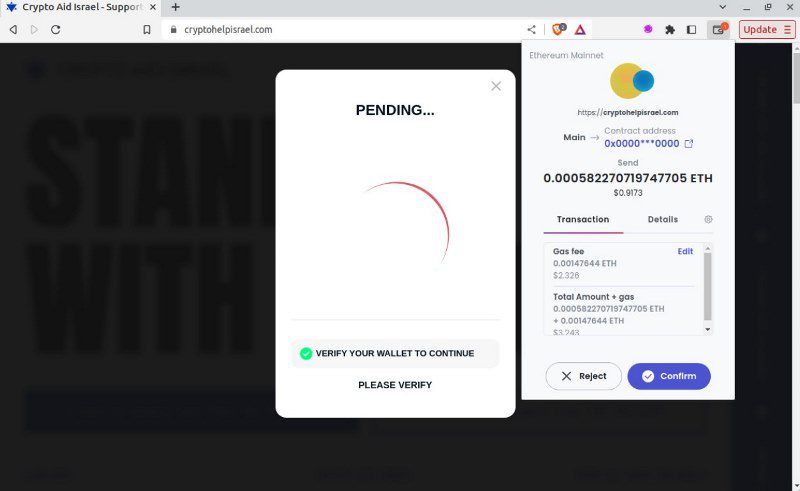
Example of a crypto drainer where victims trying to donate are told to “Verify your wallet to continue” – in reality, victims are agreeing to send the entire contents of their cryptocurrency wallet to the criminal.
Our research has found that criminals who operate crypto drainers tend to be opportunistic. Back in March 2023, Netcraft reported on crypto-draining attacks in a blog that described how criminals were capitalizing on Silicon Valley Bank’s demise.
Both approaches to soliciting cryptocurrency “donations” are used in campaigns exploiting the Gaza conflict. This includes several hundred donation fraud emails directing victims to purpose-registered websites hosting crypto drainers, and several hundred more which instead encourage donations to be sent directly to cryptocurrency addresses included in the text.
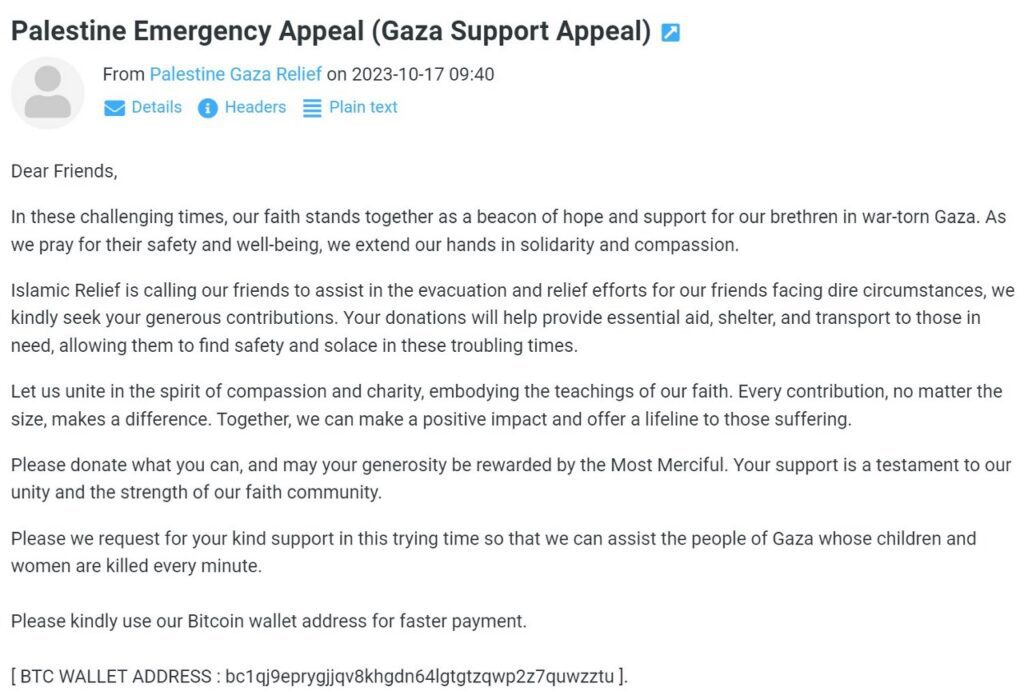
Donation fraud email requesting for donations to be sent to a listed cryptocurrency address
Israel and Palestine-themed spoofs
The malicious websites detected since the start of the conflict demonstrate how established cybercriminals will simply change the lure used to attract potential victims. Based on Netcraft analysis for one actor, they have used various domains that claim to be helping each different party involved in the conflict. This includes mission-israel[.]com, help-palestine[.]online, lebanonneedhelp[.]online, and egypthelp[.]online.
We believe it’s a single threat actor because:
- Very similar email campaigns are used to distribute links to multiple sites
- 3/4 of the sites observed had nearly identical designs
- Sites are on the same IP address (113.30.189.220)
- Sites were registered within days of each other, using the same registrar (Hostinger)
- Sites request that donations are sent to the same cryptocurrency addresses
- Sites load the same crypto drainer script from the same external domain (dappbackend[.]homes)
This showcases a common tactic leveraged by scammers to attack themes and social vulnerabilities for as long as they are effective.
Scam emails used to distribute links
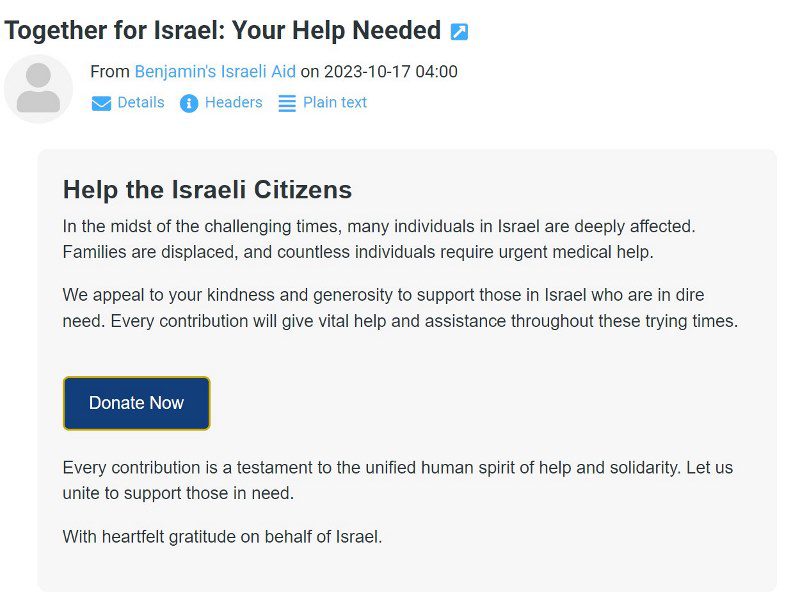
Donation fraud email used to direct victims to mission-israel[.]com
Netcraft systems detected hundreds of donation fraud emails linking to mission-israel[.]com. These make use of subjects with calls to action such as “Together We Can Support Israel”, “Your Chance to Support Israel”, “United for Israel – Join the Cause”, “Strengthen Israel – Your Support Matters”, “Support the Heart of Israel – Donate Now”.
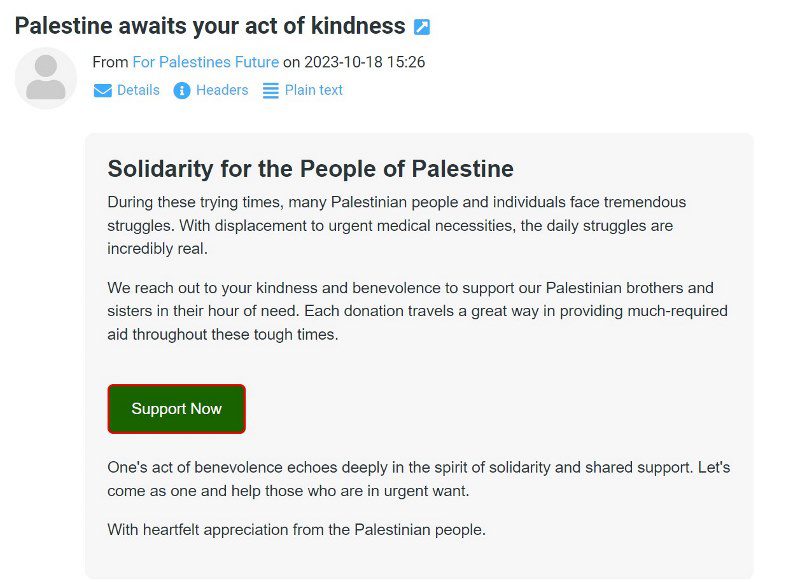
Donation fraud email used to direct victims to help-palestine[.]online
In addition, we have identified a smaller number of very similar donation fraud emails that direct to help-palestine[.]online. These emails have an almost identical layout and text, differing only in colours and the exact phrasing used. Subject lines used are also similarly emotive calls to action, such as “Gaza children appeal for your support”, “Gaza needs you, lend your support”, “Your help can change lives in Palestine”, “Bring hope to Palestinian families”.
Each of these emails use similar, but not identical, text in the email content. While the meaning is retained in each sentence, each line is slightly rephrased, for example “We appeal to your empathy and generosity”, “We reach out to your compassion and generosity”, “We call to your empathy and generosity”. Combined with sending these from different email addresses, this makes it more difficult for spam filters to detect and block these emails.
Link-level tactics: breaking down bad actors
mission-israel[.]com
The website mission-israel[.]com asked for donations to “support victims in Israel”, with donations being solicited to various crypto wallet addresses. Addresses are provided for victims to “donate” via Ethereum, Bitcoin, Litecoin, and Tether.
A crypto drainer was also present on the site, which was initiated if the victim chose to “Pay with Wallet”. If a user chose to connect their wallet and agreed to subsequent pop-ups, 95% of its contents would be sent to the threat actor.
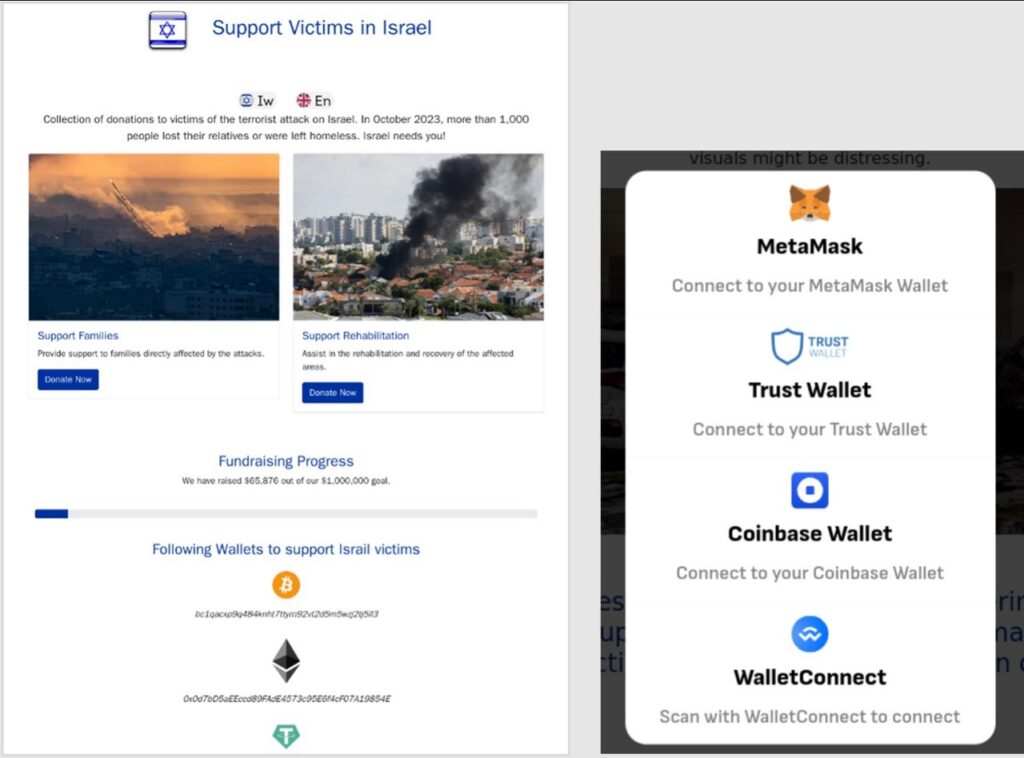
Screenshots from mission-israel[.]com
The site impersonates for MDA Israel (a legitimate Israeli non-profit organization) by listing their contact details in the footer
help-palestine[.]online, egypthelp[.]online, lebanonneedhelp[.]online
These websites had very similar designs but different text depending on the party for whom they were purportedly soliciting donations:
- Help-palestine[.]online “Palestine needs your help! By donating even the smallest amount, you may be able to save hundreds of lives. Don’t remain indifferent, the people of Palestine need your support!”
- Lebanonneedhelp[.]online “Lebanon needs your help! By donating even the smallest amount, you may be able to save hundreds of lives. Don’t remain indifferent, the people of Lebanon need your support!”
- Egypthelp[.]online “Palestinians and Egypt needs your help! Every cent of your support helps Egypt take in and settle Palestinian refugees! Let’s fight Israeli terrorism together!”
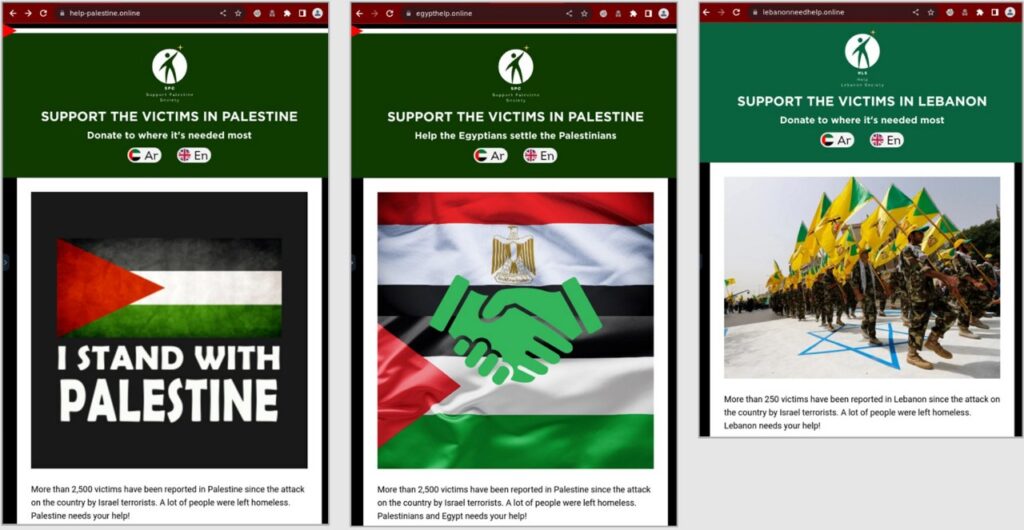
From left to right, screenshots from help-palestine[.]online, egypthelp[.]online, lebanonneedhelp[.]online
All three pages solicit donations to the same cryptocurrency addresses as mission-israel[.]com discussed earlier. All three also have a Donate by wallet option, which loads the same crypto drainer script as mission-israel[.]com.
These sites also included a Pay by credit card option. The page claims that it is ‘on the platform Stripe’; however, it does not use the Stripe platform for payment. Instead, the collected details are simply submitted to an endpoint on the same site named update_payment.php.
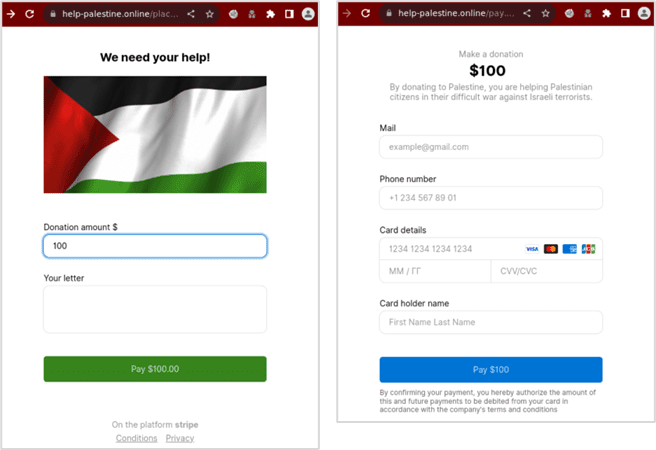
help-palestine[.]online, egypthelp[.]online, lebanonneedhelp[.]online include a Pay by credit card option.
cryptohelpisrael[.]com
cryptohelpisrael[.]com is another crypto-draining website, this time impersonating a legitimate website https://cryptoaidisrael.com/. The real Crypto Aid Israel was registered in October 2023 for ‘Web3 friends of Israel gathering together to raise funds for victims’. Both the URL and the design of the website are attempts to trick the user into believing that they are interacting with the genuine organisation.

The genuine site cryptoaidisrael.com (left), and the crypto-draining site cryptohelpisrael[.]com (right)
If a user chooses to donate on cryptohelpisrael[.]com, they are instructed to connect their wallet. Victims are told to ‘Verify your wallet to continue’. In reality, they are agreeing to send the contents of their wallet to the fraudster.
We found that the stolen funds are sent to multiple wallet addresses, across which the criminals had received over $1.6M in ETH since 14th October. Note that this revenue is not necessarily generated solely from cryptohelpisrael[.]com: the same criminal could be running other fraud campaigns using the same set of addresses.
plakaliklar[.]com/pcrf/
The website plakaliklar[.]com/pcrf/ was a phishing page impersonating the legitimate Palestine Children’s Relief Fund (PCRF) website https://www.pcrf.net/. This legitimate website is currently displaying an overlay asking for donations on their website, which was duplicated exactly by the malicious website.
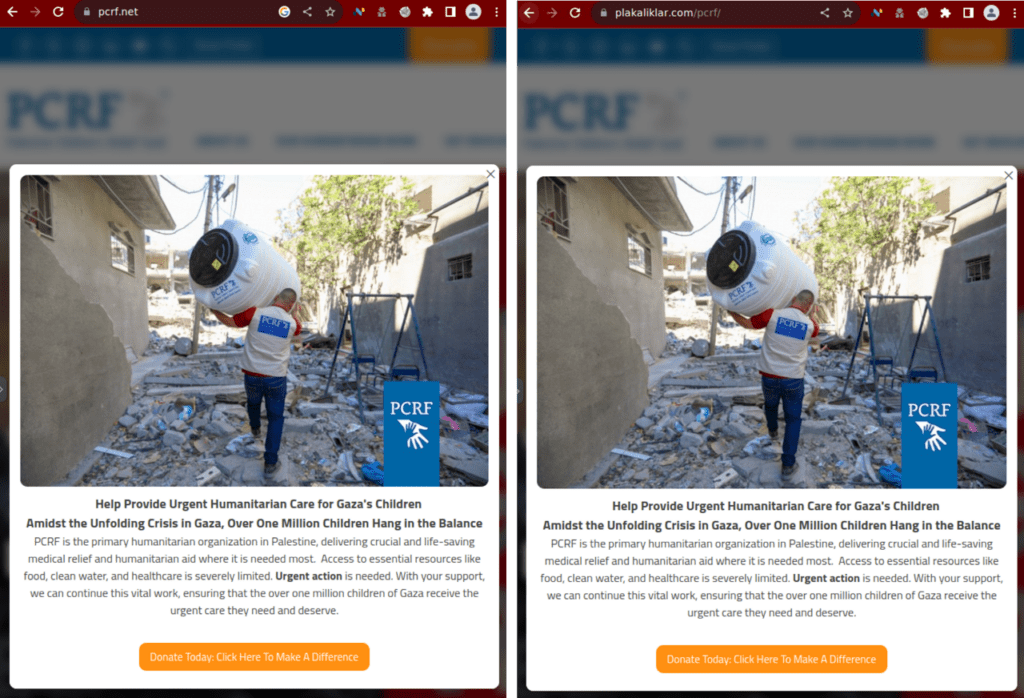
The genuine site pcrf.net (left), and the scam page impersonating it plakaliklar[.]com/pcrf/ (right)
Clicking on the Donate Today link on the malicious website directed the victim to a “Payment Form” containing a Bitcoin wallet address to which to send funds. Victims were told to “send your donation within 24 hours to ensure proper processing”. After submitting the form, the page simply displayed “Thank you for your donation!”, without verifying that funds had been sent.
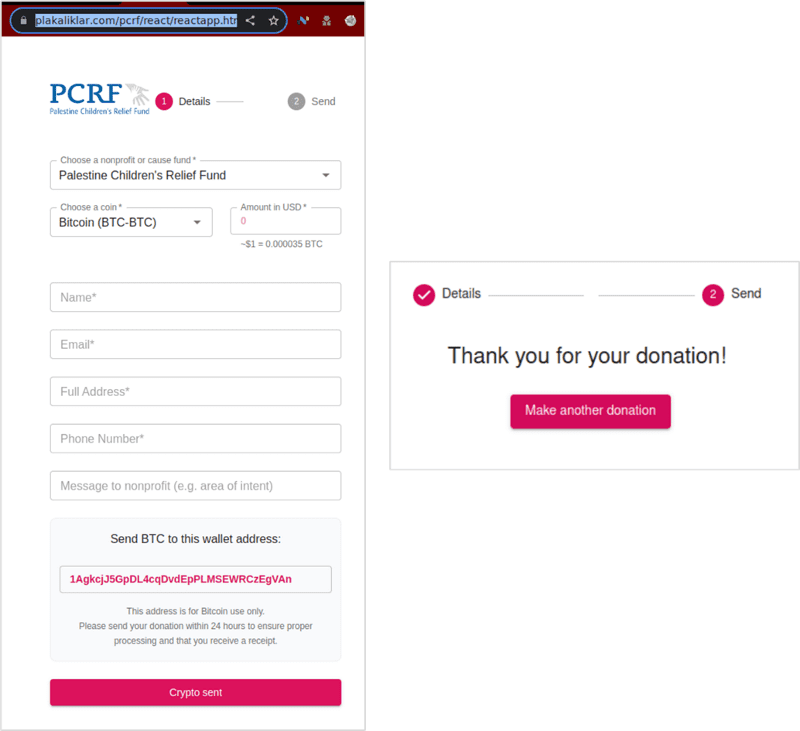
Payment form on plakaliklar[.]com/pcrf/ and “Thank you” message displayed
How can Netcraft help?
Netcraft provides cybercrime detection, disruption and takedown services to organizations worldwide, including 12 of the top 50 global banks and the biggest cryptocurrency exchange ranked by volume. We perform takedowns for around one-third of the world’s phishing attacks and take down 90+ attack types at a rate of 1 attack every 15 seconds—defending your organization against cryptocurrency scams that leverage your brand’s identity.
Netcraft is the world leader in cybercrime detection, disruption, and takedown, and has been protecting companies online since 1996. Our systems analyze millions of suspected malicious sites each day, typically blocking an attack within minutes of discovery.