An EA Games server has been compromised by hackers and is now hosting a phishing site which targets Apple ID account holders.
The compromised server is used by two websites in the ea.com domain, and is ordinarily used to host a calendar based on WebCalendar 1.2.0. This version was released in September 2008 and contains several security vulnerabilities which have been addressed in subsequent releases. For example, CVE-2012-5385 details a vulnerability which allows an unauthenticated attacker to modify settings and possibly execute arbitrary code. It is likely that one of these vulnerabilities was used to compromise the server, as the phishing content is located in the same directory as the WebCalendar application.
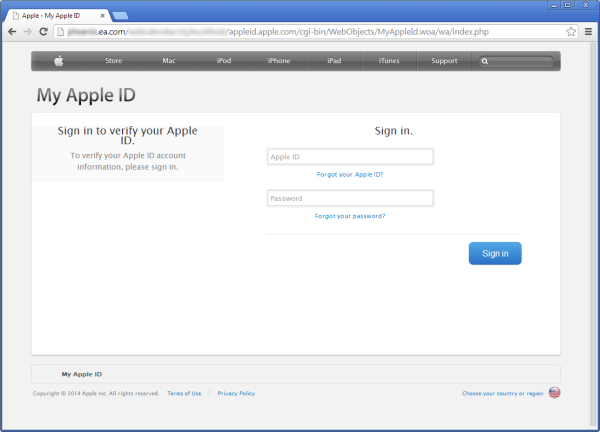
The phishing site attempts to trick a victim into submitting his Apple ID and password. It then presents a second form which asks the victim to verify his full name, card number, expiration date, verification code, date of birth, phone number, mother’s maiden name, plus other details that would be useful to a fraudster. After submitting these details, the victim is redirected to the legitimate Apple ID website at https://appleid.apple.com/cgi-bin/WebObjects/MyAppleId.woa/
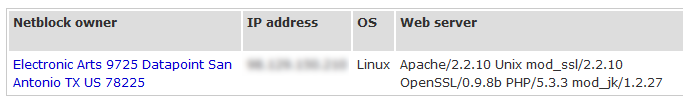
The compromised server is hosted within EA’s own network. Compromised internet-visible servers are often used as “stepping stones” to attack internal servers and access data which would otherwise be invisible to the internet, although there is no obvious outward facing evidence to suggest that this has happened.
In this case, the hacker has managed to install and execute arbitrary PHP scripts on the EA server, so it is likely that he can at least also view the contents of the calendar and some of the source code and other data present on the server. The mere presence of old software can often provide sufficient incentive for a hacker to target one system over another, and to spend more time looking for additional vulnerabilities or trying to probe deeper into the internal network.
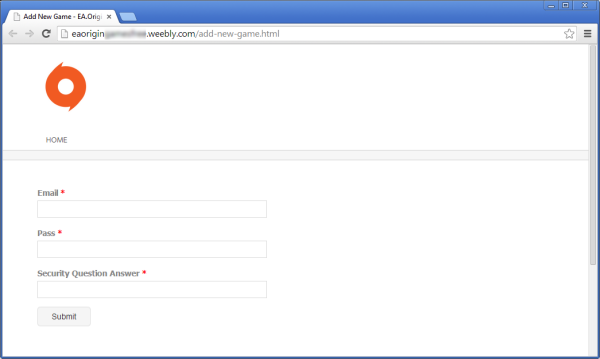
As well as hosting phishing sites, EA Games is also the target of phishing attacks which try to steal credentials from users of its Origin digital distribution platform. For example, the following site — which has been online for more than a week — is attempting to steal email addresses, passwords and security question answers.
EA’s Origin servers also came under attack earlier this year, causing connectivity and login problems in various EA games. A tweet by @DerpTrolling appeared to claim responsibility for the outages, while also suggesting that it was a distributed denial of service attack which caused the problems.
We’ve directed the Gaben Laser Beam™ @ the EA login servers. Origin #offline
— DERP (@DerpTrolling) January 3, 2014
(“Gaben” is a reference to Gabe Newell, managing director of Valve Corporation, which owns the competing Steam digital distribution platform)
Netcraft has blocked access to all phishing sites mentioned in this article, and informed EA yesterday that their server has been compromised. However, the vulnerable server — and the phishing content — is still online at the time of publication.
The Audited by Netcraft service provides a means of regularly testing internet infrastructure for old and vulnerable software, faulty configurations, weak encryption and other issues which would fail to meet the PCI DSS standard. These automated scans can be run as frequently as every day, and can be augmented by Netcraft’s Web Application Security Testing service, which provides a much deeper manual analysis of a web application by an experienced security professional.