Fraudsters are stealing eBay usernames and passwords using phishing pages hosted on eBay’s own infrastructure. One of these pages, targeting German users, is shown below:
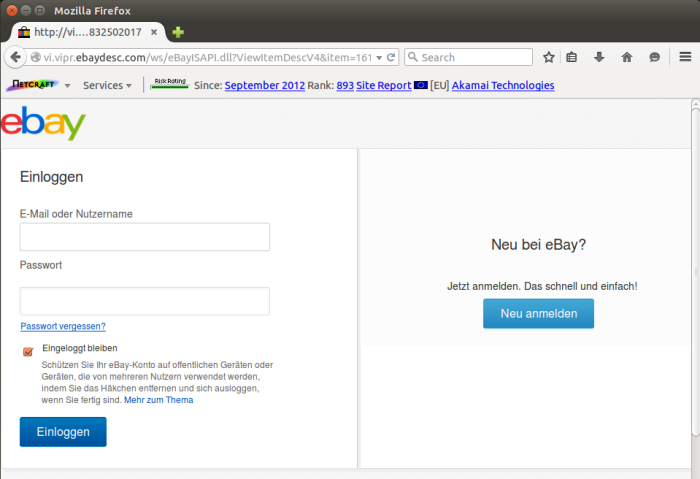 An eBay phishing form hosted on eBay’s own infrastructure. The form contents are submitted to an external domain in Russia.
An eBay phishing form hosted on eBay’s own infrastructure. The form contents are submitted to an external domain in Russia.
The convincing appearance of the spoof login form is bolstered by the fact that it is hosted on a genuine eBay domain, ebaydesc.com. This domain is ordinarily used to host descriptions for eBay listings which are displayed within iframes on eBay listing pages.
In this case, the corresponding eBay listing has already been deleted, although the phishing content within the listing’s description can still be viewed by browsing directly to the relevant URL on vi.vipr.ebaydesc.com. Consequently, the attack is still live and capable of stealing credentials from eBay users.
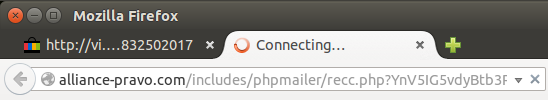 The URL of the credential-stealing script is only momentarily visible in the address bar before the victim is redirected to the genuine eBay site.
The URL of the credential-stealing script is only momentarily visible in the address bar before the victim is redirected to the genuine eBay site.
When a victim enters his username and password into the form, both values are submitted to a PHP script hosted on a server in Russia. After stealing the credentials, this script then redirects the victim to the genuine ebay.de login page, which reports that the username or password was incorrect.
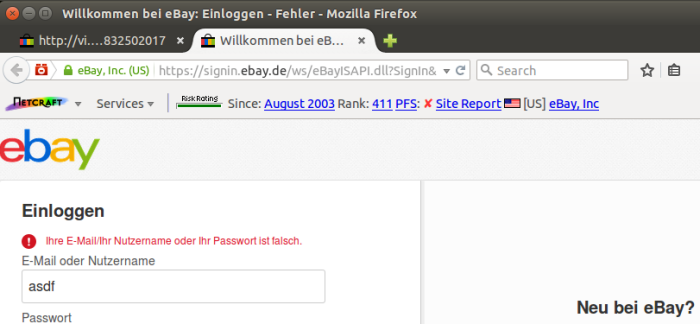 After the victim’s credentials are stolen, he is redirected to the real eBay login page. Note that the username field has been automatically populated with the username stolen by the fraudster.
After the victim’s credentials are stolen, he is redirected to the real eBay login page. Note that the username field has been automatically populated with the username stolen by the fraudster.
This error message might cause the victim to become suspicious enough to look at the browser’s address bar, to check he is on the right website; but it will already be too late at this point – his credentials will have already been stolen, and because his browser will now be showing ebay.de in the address bar, he may not even realise that his credentials have just been sent to a web server in Russia. There is consequently little chance of the victim reacting by changing his password, allowing the fraudster to take full advantage of the stolen credentials at his leisure.
The website involved in collecting the stolen credentials has also been used to host other phishing attacks targeting German-speaking consumers, including sites impersonating PayPal, Apple, and mobile.de.
In an attempt to evade detection by eBay and others, the fraudster has obfuscated the HTML source of his eBay phishing form. This makes it impossible to find such a listing by searching for any of the words that appear in the description, yet the rendered results appear as normal when viewed in a web browser.
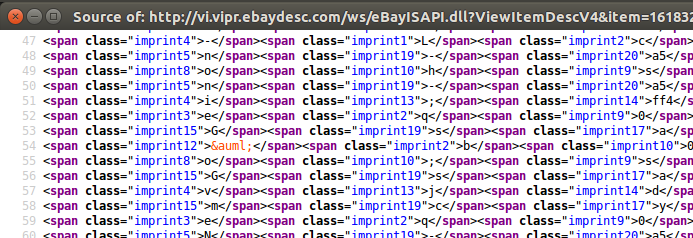 The obfuscated HTML source used by the phishing content hosted by eBay.
The obfuscated HTML source used by the phishing content hosted by eBay.
Allowing anyone to insert arbitrary HTML and malicious scripts into a listing’s description gives plentiful opportunities to would-be fraudsters, particularly as this weakness has been exploited to carry out similar attacks against eBay users in the past. Last year, Netcraft reported on fraudsters injecting malicious JavaScript into eBay listings to set up man-in-the-middle attacks against car buyers, and similar JavaScript redirection techniques have continued to be exploited throughout 2015.
These phishing methods can be much more successful than traditional phishing attacks (where content is hosted solely on an unrelated domain). The techniques employed in these latest attacks are not permitted under eBay’s HTML and JavaScript policy; however, a fraudster intent on stealing passwords is not going to be deterred by words alone.