In June 2015, Trustwave issued an organisation-validated certificate for paypal-office.com, myaccount-paypal.com and paypal-sign.com that was used on a PayPal phishing site. The certificate was issued to an individual in India, Asha Shaikh, who may be the fraudster behind the phishing site, or perhaps one of the fraudster’s victims. The phishing attack is now offline, but the certificate has yet to be revoked by Trustwave at the time of writing.
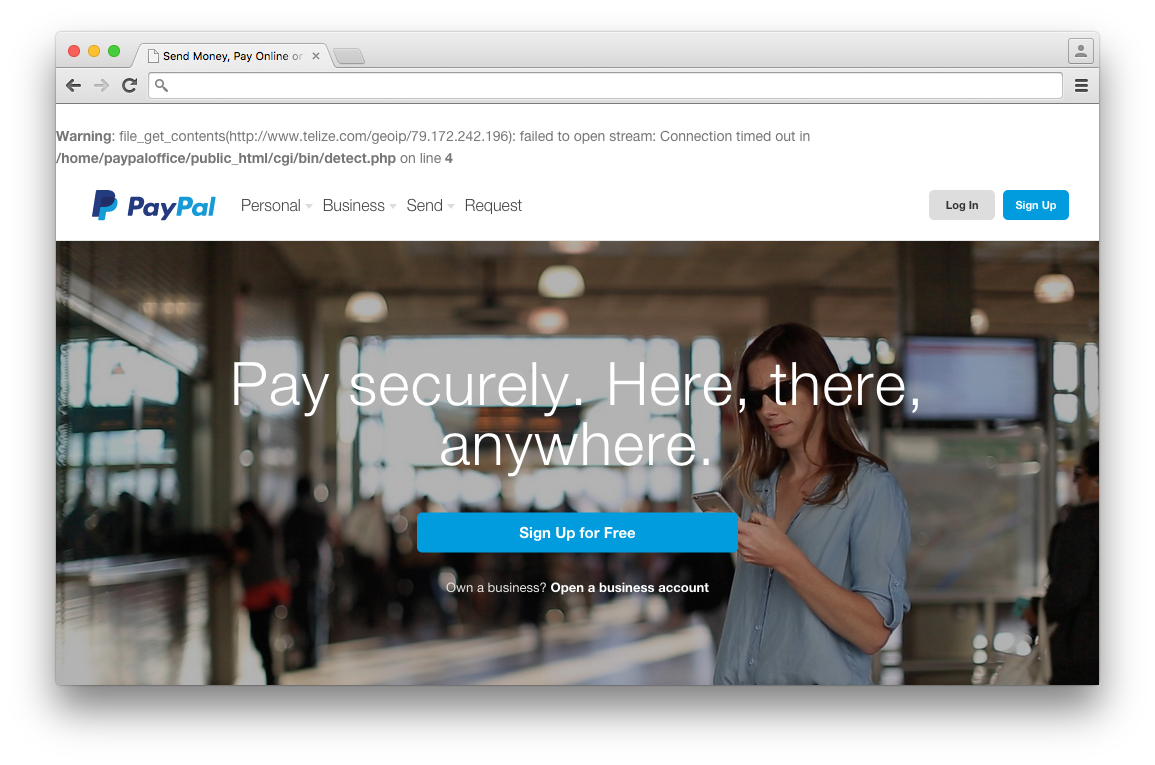
Rendered contents of phishing site found on www.paypal-office.com. The error message visible at the top of the page is a giveaway: the geo-location of the visitor’s IP address failed, and it reveals the location of the files used to power the phishing site.
Certificate authorities typically sell certificates in three broad categories of assurance: domain-validated certificates simply validate control over a domain name; organisation-validated certificates include the identity of the organisation; and Extended Validation certificates increase the level of identity checking done to meet a recognised industry standard.
The difference between DV, OV, and EV certificates is sometimes subtle — many sources of consumer advice do not make the distinction between certificates that provide further identity information and those that only validate domain name ownership. For example, Google Chrome’s help page states: "You can tell if a site is real if it has a valid TLS/SSL certificate".
Most certificates with deceptive domain names are domain-validated, though some appear to be organisation-validated. Many of the SSL certificates associated with CloudFlare’s "Universal SSL" programme are ostensibly organisation-validated; however, the organisation being validated in this case is CloudFlare itself and not each individual customer.
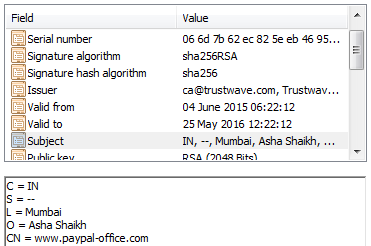 An organisation-validated certificate for paypal-office.com shown in the Windows certificate viewer.
An organisation-validated certificate for paypal-office.com shown in the Windows certificate viewer.
Rather than be processed automatically, as is possible with domain-validated certificates, most higher-assurance certificate requests will be reviewed by a human prior to issuance. This additional level of validation makes it all the more surprising that a request for a certificate containing "paypal" wasn’t considered a high risk request, and consequently rejected after being subjected to increased scrutiny.
Trustwave offers a Relying Party warranty with its certificates, covering fraudulent credit card charges made by a Trustwave certificate holder. However, the warranty does not cover other types of fraud, meaning phishing for credentials or fraudulent payments using other payment methods are not covered. As a result, victims of this phishing attack will not be able to claim on this warranty, despite having their PayPal credentials stolen by a fraudster using a Trustwave certificate.