Disclosures by groups including LulzSec, Anonymous and Wikileaks have highlighted that poor security is endemic throughout government websites. During July, Netcraft’s anti-phishing toolbar blocked 146 new phishing attacks hosted on government websites. Nearly half of these used the gob.pe secondary top-level domain, making the government of Peru the phishiest in the world.
Unusually, more than a third of these government-hosted phishing attacks targeted a single British financial institution, Lloyds Banking Group. Halifax and Lloyds TSB, which are subsidiaries of the group, were each targeted more times than any other organisation, including PayPal.
Phishing sites hosted on government domains (top 10)
(source: Netcraft Phish Feed)
| Government TLD |
Country | New phishing sites in July 2011 |
|---|---|---|
| gob.pe | Peru | 69 |
| gov.br | Brazil | 12 |
| go.th | Thailand | 11 |
| gob.mx | Mexico | 9 |
| gov.cn | China | 9 |
| gov.ar | Argentina | 6 |
| gov.za | South Africa | 6 |
| gov.pk | Pakistan | 3 |
| gov.ec | Ecuador | 3 |
| gov.tr | Turkey | 3 |
Some of these government-hosted phishing sites were even used to attack other governments. The website of the UK government, Directgov, was targeted in 14 of these phishing attacks. All of the phishing content used in these attacks was hosted on Peruvian government domains, but has since been removed.
Not all of the phishing sites blocked last month have been taken down. Near the beginning of July, Netcraft blocked an Amazon phishing site on a Polish government TLD, but the fraudulent content is still being served today, more than a month later. This was the only new phishing site to appear on a Polish government website in July, and was unusually served from a compromised FTP server. By supplying valid FTP credentials as part of the URL, a fraudster can make the site viewable in any modern web browser as if it were an ordinary website served over HTTP or HTTPS:
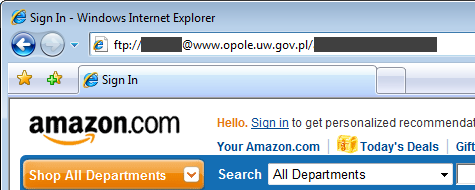
Phishing sites are regularly hosted on compromised servers. By using someone else’s web server, an attacker can create a phishing site without having to register any domain names or pay for hosting services. Certain TLDs may also be perceived as being more trustworthy than others, but this is not always a safe assumption.
For example, the .gov TLD is restricted for use by government entities in the United States, so content on these sites is often assumed to be legitimate without much thought. However, www.caldwelltx.gov was presumably compromised at some point, as it was seen serving a Halifax phishing site in July.
Netcraft also found several government websites that had been defaced by “Al3x 0wn5”. One Indonesian government site was still defaced at the time of publication, and displayed a mock root prompt on its homepage:
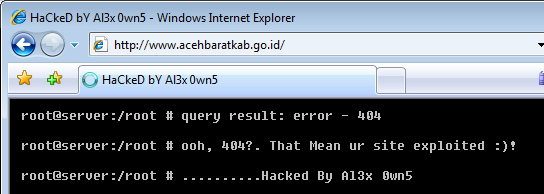
The demonstrably poor security of some government websites may have much wider implications for a country’s population. For example, if a remote attacker is able to deface a site or upload arbitrary phishing content, it may also be possible to gain unauthorised access to backend databases or divert any payment details transmitted through the site.