Governments and organisations globally have been making announcements that just a few weeks prior would have been unprecedented. As more of our lives are moving online in an attempt to adapt to changes brought about by the Coronavirus pandemic, many are trying out services they were previously unfamiliar with, such as video conferencing or online grocery shopping. While others are finding themselves with more time to pursue online hobbies such as gaming.
The combined effect of information overload and a mass of people using unfamiliar software and services has created an environment ripe for exploitation by cybercriminals.
Netcraft has tracked Coronavirus-themed cybercrime since 16th March, shortly after it was declared a pandemic by the World Health Organisation. While Netcraft continues to see high volumes of Coronavirus-inspired fake shops, advance fee fraud, phishing and malware lures, this post covers some of the trends Netcraft has observed since our previous posts on the topic.
Recently observed Coronavirus-themed threats
Fake Government information sites and mobile malware
Many governments have set up dedicated websites offering advice and services to support their citizens through the pandemic. Cybercriminals are taking advantage of this by providing copy-cat sites with a malicious twist.
In one recent campaign, the cybercriminals deployed a site that poses as the UK Government and offers “credit card refunds” for “COVID-19 support”. The fraudulent site uses UK Government branding and collects the victim’s personal information – including their credit card number, date of birth and telephone number.
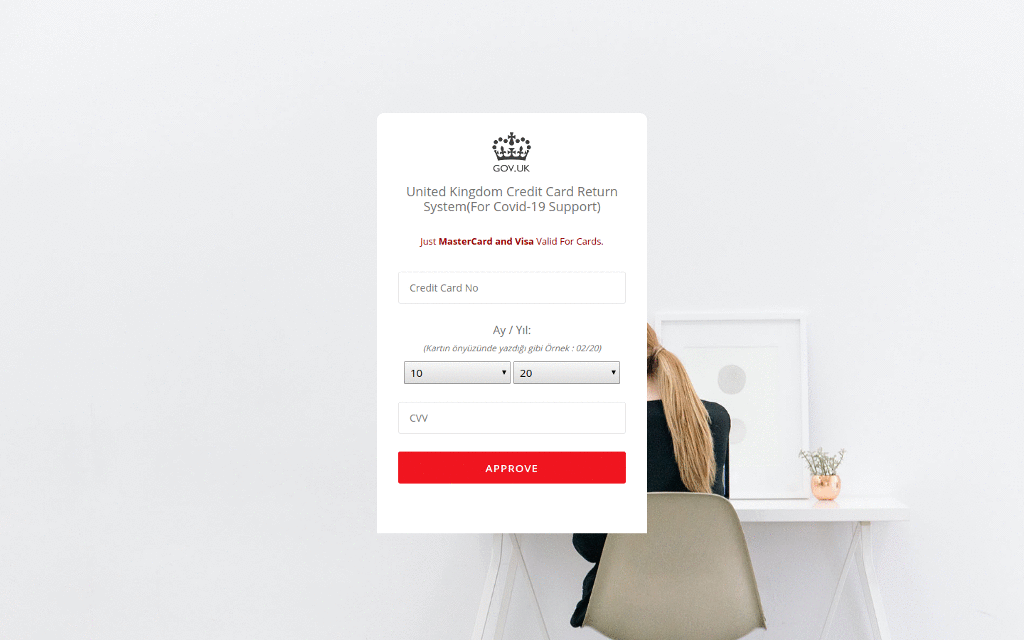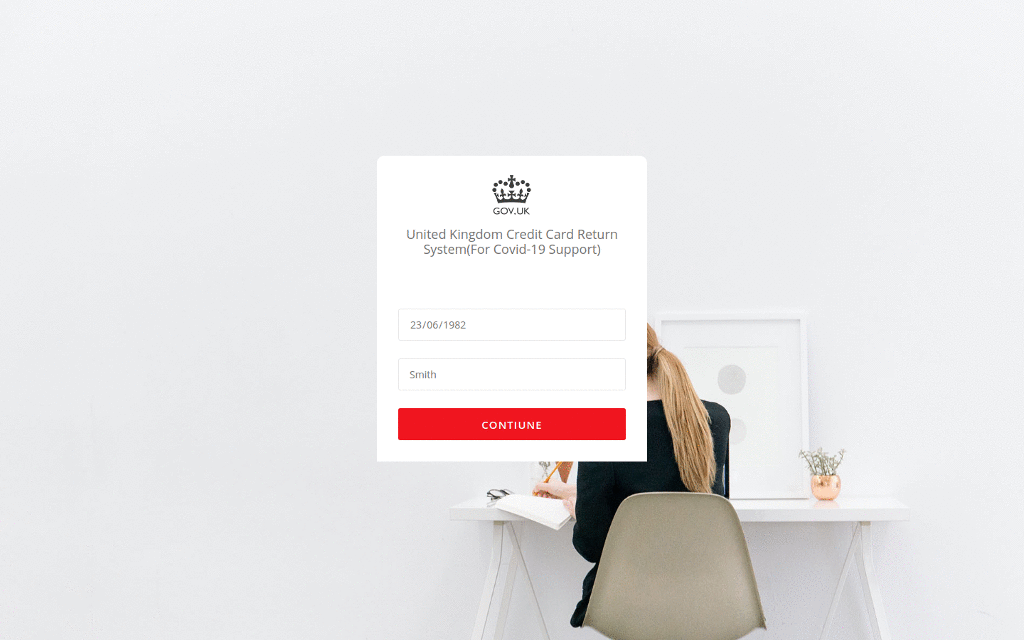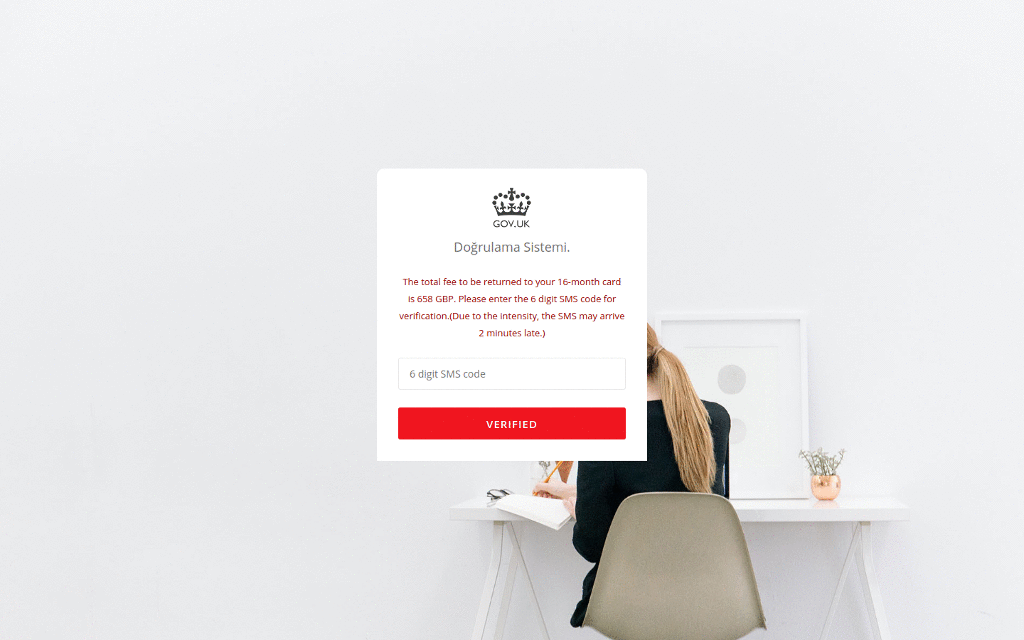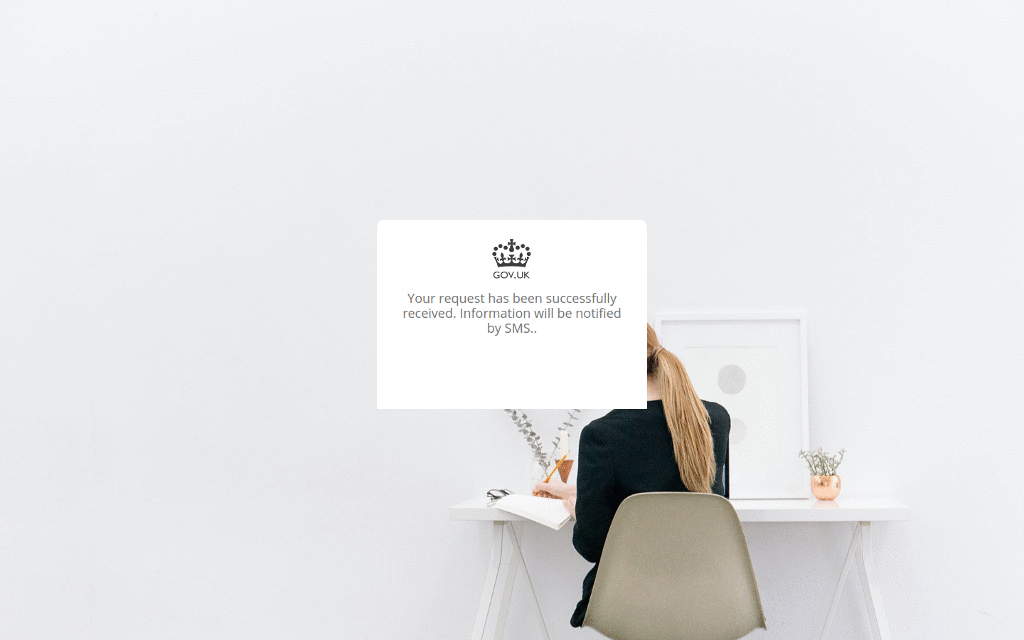
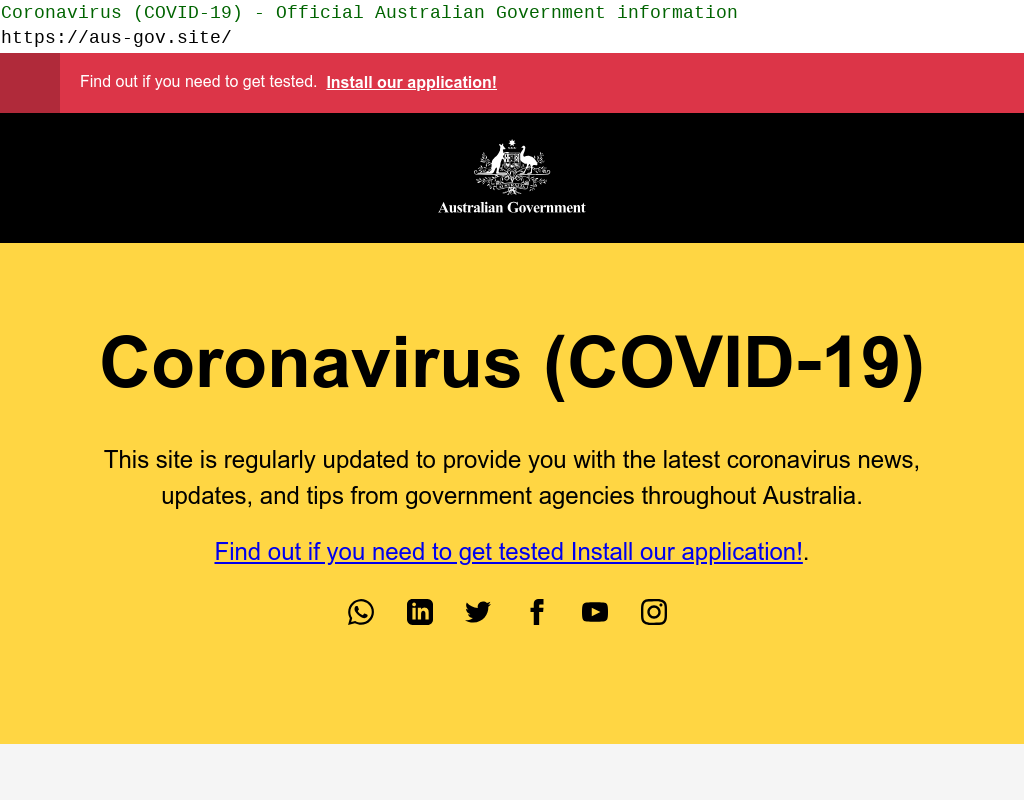
In another case, cybercriminals set up a fake site which looked identical to the Australian Government’s. But rather than providing the government’s latest Coronavirus advice, it included a link to an Android application which claimed to provide information on how to get tested. In reality, the mobile application deployed Cerberus, a popular Android banking trojan, which uses overlays to steal credentials.
Phishing targeting video conferencing platforms such as Zoom
As companies transition their employees to remote working, many are making increased use of video conferencing platforms such as Zoom. Netcraft has observed a number of phishing attacks targeting Zoom suggesting that cybercriminals have identified this as an opportunity.
A compromised zoom account can be used by a cybercriminal to launch further attacks such as: Posing as an employee by sending out meeting requests which appear to be from the company (a supermarket purchaser making an order with a supplier, for example); enumerating employee names and contact information using Zoom’s “Company directory” feature; gaining access to employee email accounts if the same password is used for their Zoom account; and downloading recordings of confidential meetings.
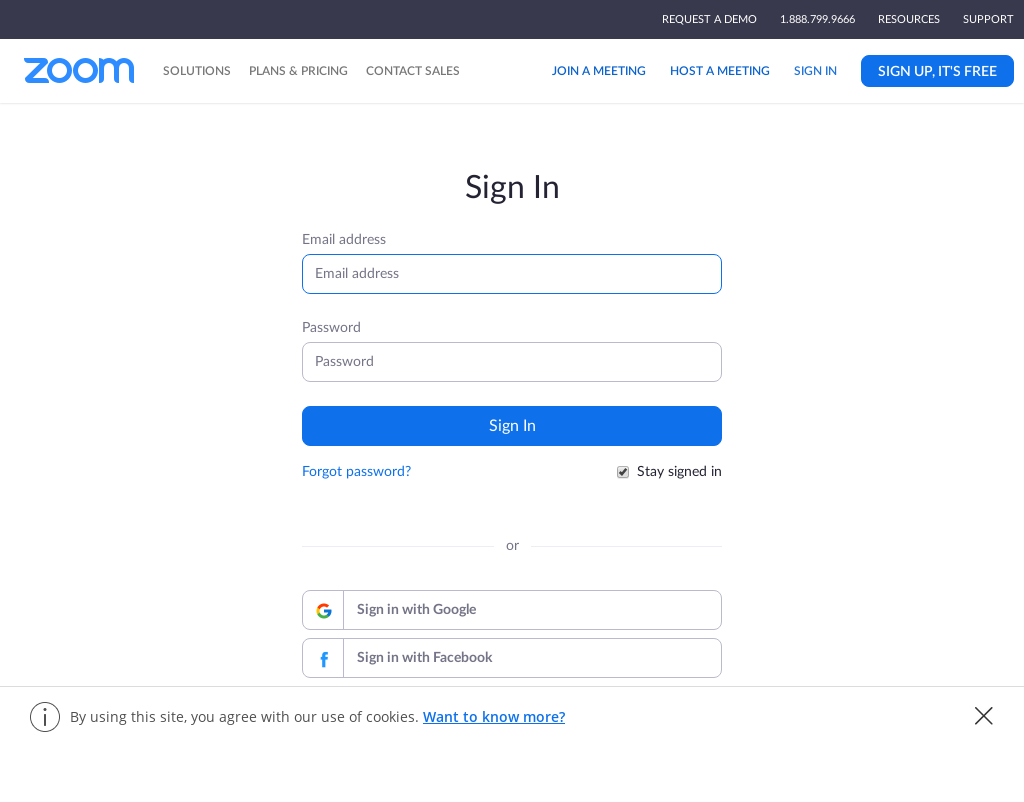
Example Zoom phishing site
Netcraft has also seen a Zoom-branded Active Directory Federation phish which may have been used in a targeted attack on Zoom employees.
Phishing sites impersonating financial institutions referencing Coronavirus
Many governments have announced unprecedented changes in legislation to help ease the financial burden caused by the Coronavirus pandemic. Netcraft has observed phishers taking advantage of the confusion by creating phishing sites targeting financial institutions and including in-page lures that claim to offer financial assistance in exchange for the victim’s personal information.
In a recent campaign, cybercriminals added a banner to a phishing site targeting Poste Italiane. The banner stated that new COVID-19 regulations required customers to hand over their personal information (including credentials, credit card and account balance) and failure to do so would result in their account being “blocked”. Anyone who takes a closer look at the message would soon realise that “article 190.4 paragraph 3” is in no way related to Coronavirus.
Cybercriminals that target Italian banks often include references to current events in their phishing sites. Previously we’ve seen references to the EU Directive for Payment Services (PSD2).
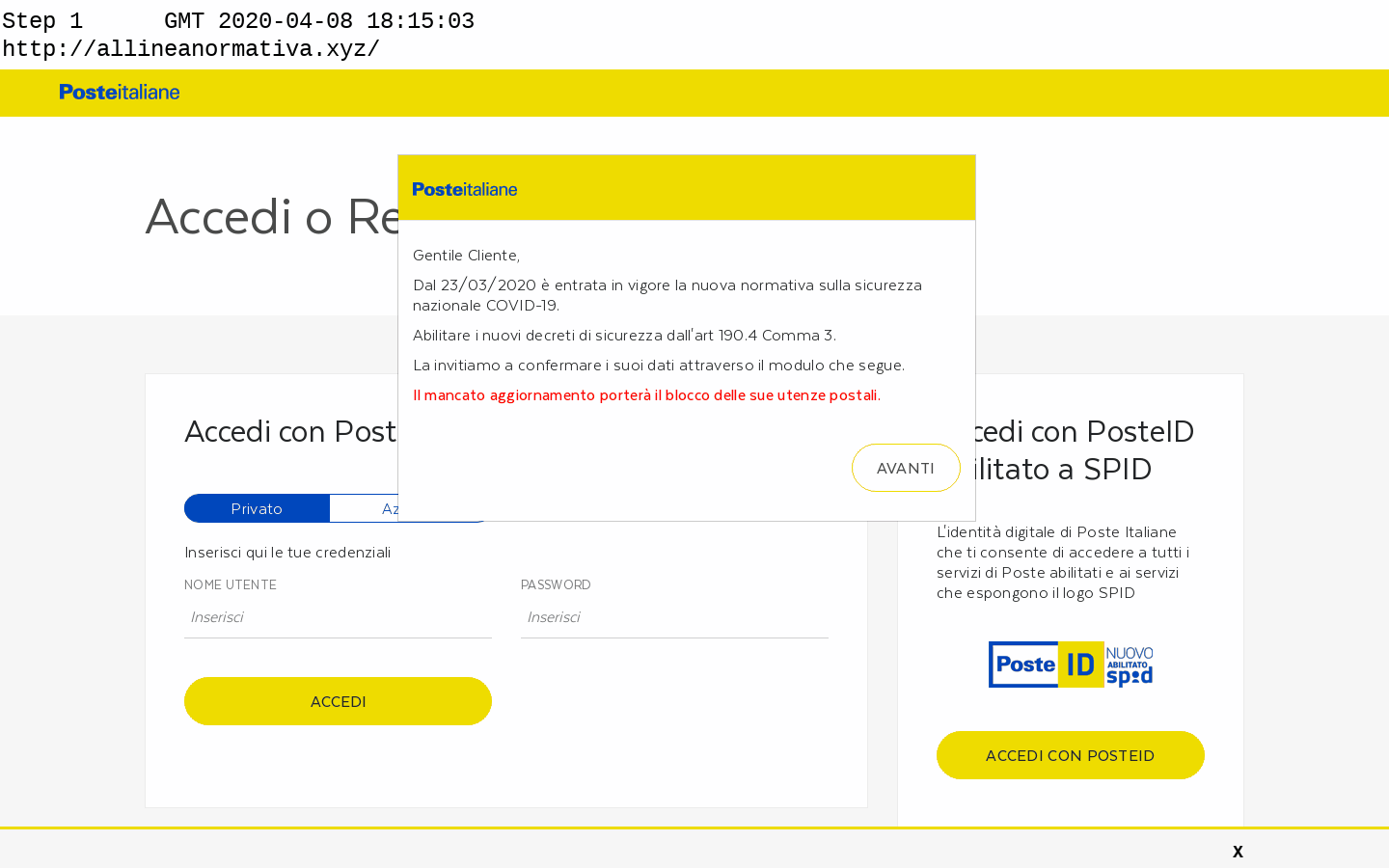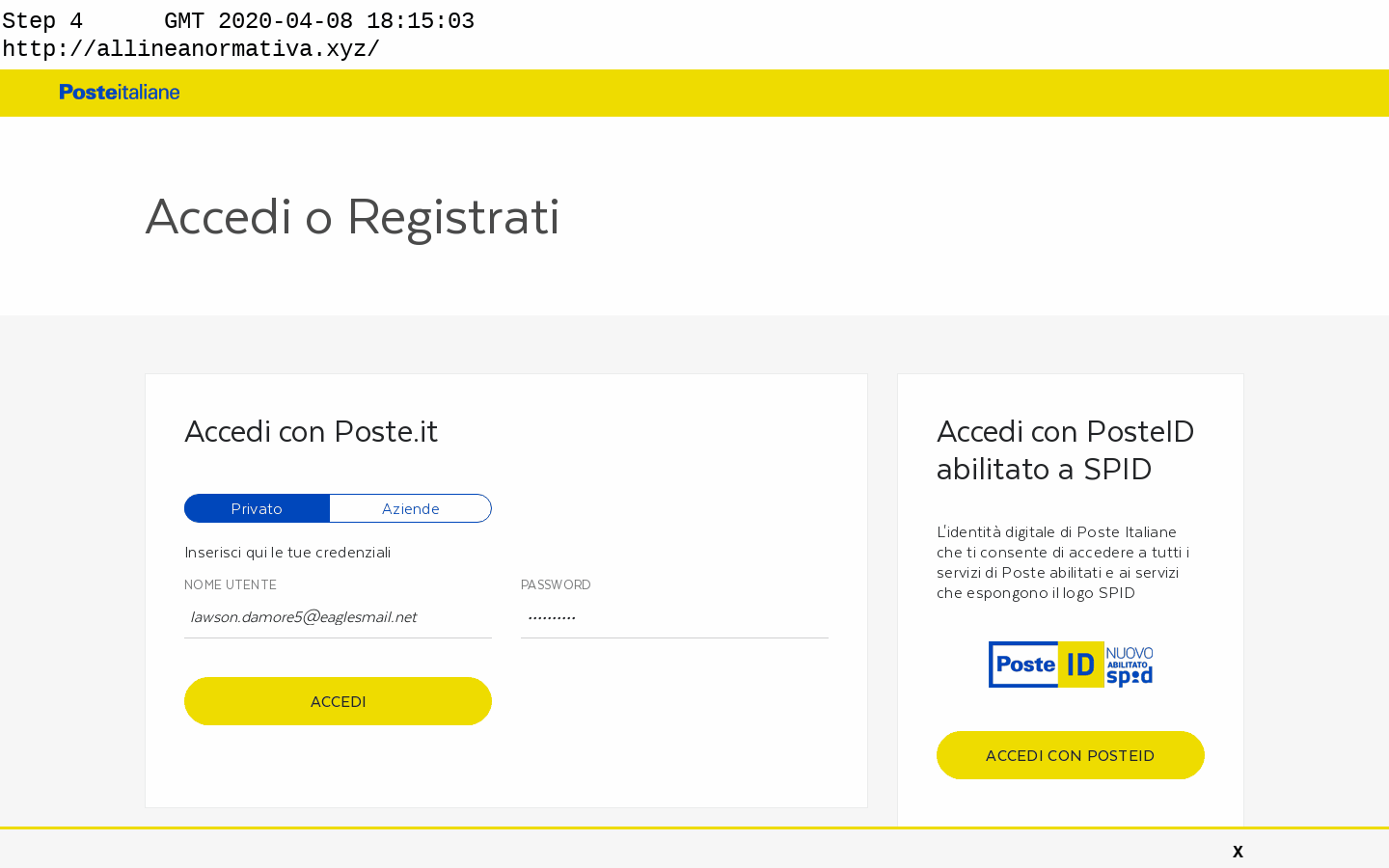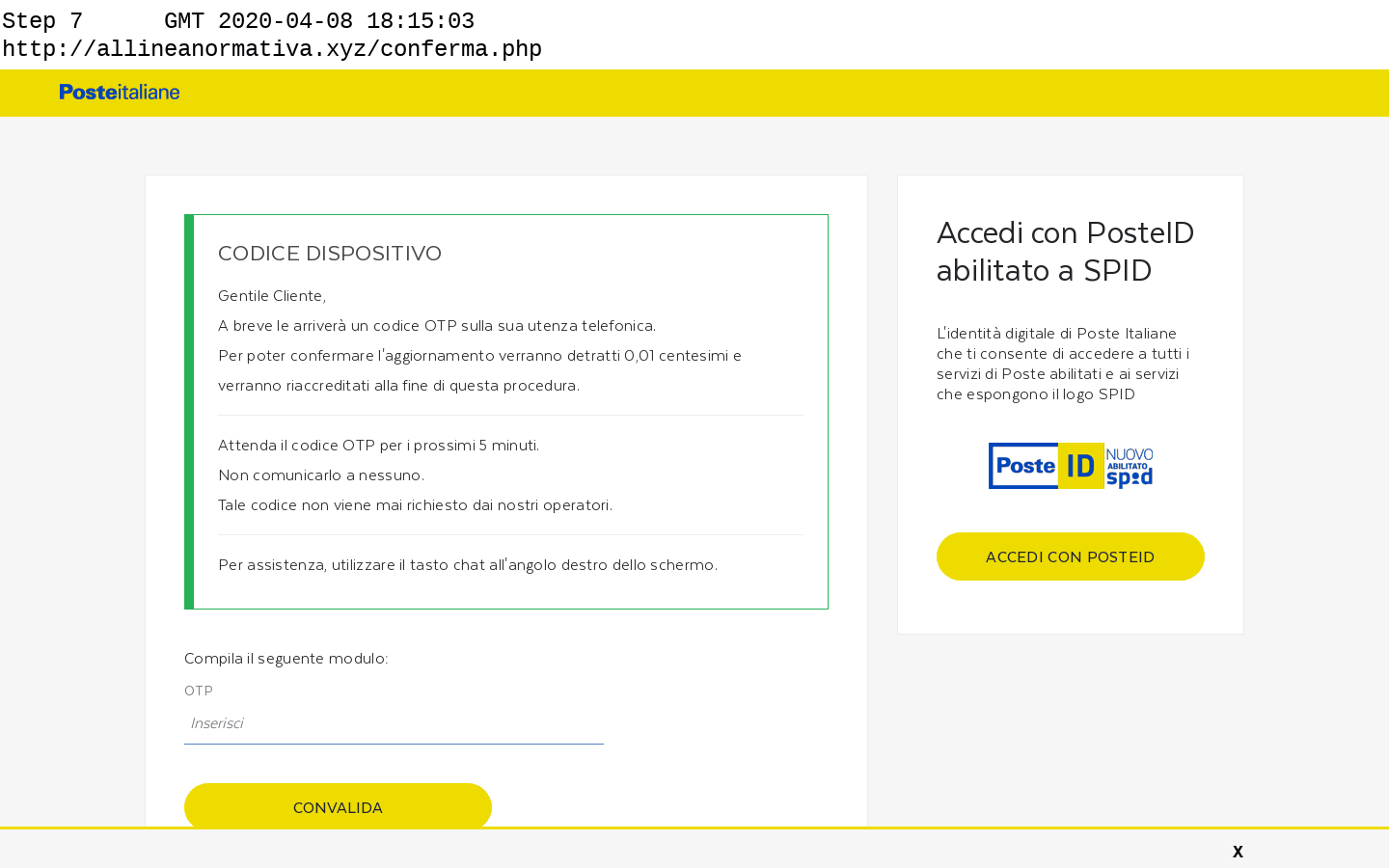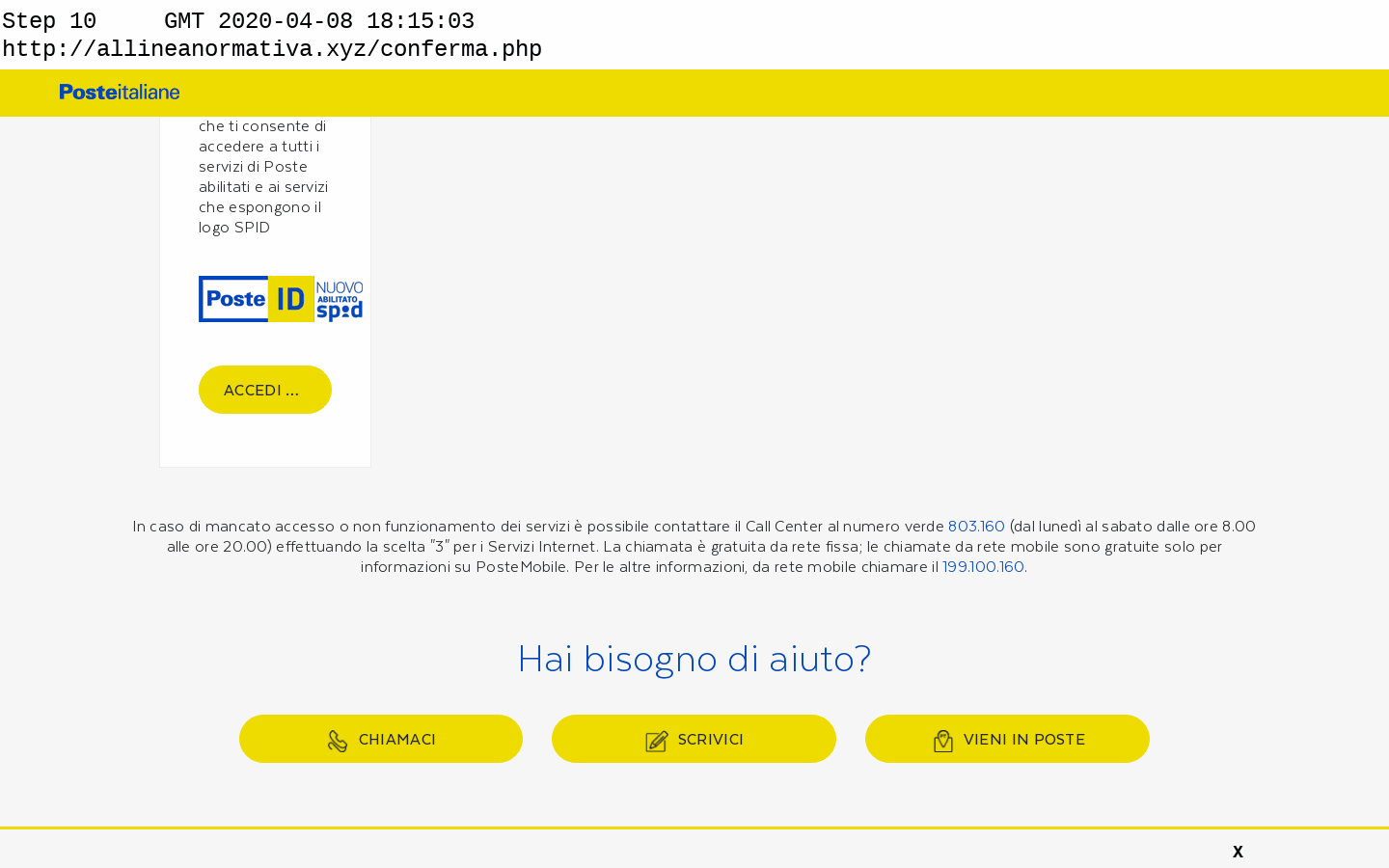
Poste Italiane phishing site with in-page COVID-19 lure
Coronavirus crooks target online gamers
Online gaming has seen a significant increase in usage with Verizon, one of the largest connectivity providers in the US, reporting a 102% increase in gaming traffic compared with a typical day.
Cybercriminals aware of this have been stepping up attacks on users of online gaming platforms using Coronavirus-themed phishing attacks perhaps hoping to take advantage of new players who are less familiar with how the games they’re playing are intended to behave.
In one incident cybercriminals created a fake blog for Dofus, a massively multiplayer online role-playing game developed by Ankama that has attracted over 40 million users. The fake blog, written in French, refers to “measures taken by the French government” and offers victim’s increasing numbers of game artefacts based on their experience. A user who falls victim to the scam is presented with a login box that steals their credentials.
Ankama claims to protect their players from phishing attacks with Ankama Shield, a feature that provides email-based two-factor authentication. However, this appears to be no obstacle for the cybercriminals. The phishing site makes a login request with the victim’s credentials which causes Ankama to send an authentication code to the victim’s email account. The phishing site brazenly requests the victim hand over the token to login. Once the cybercriminal has a valid session, we expect they immediately steal the victim’s game artefacts. In reference to “confinement”, the fraudsters even have the audacity to sign off with the ironic statement “we want to make this cold moment as pleasant as possible for you”.
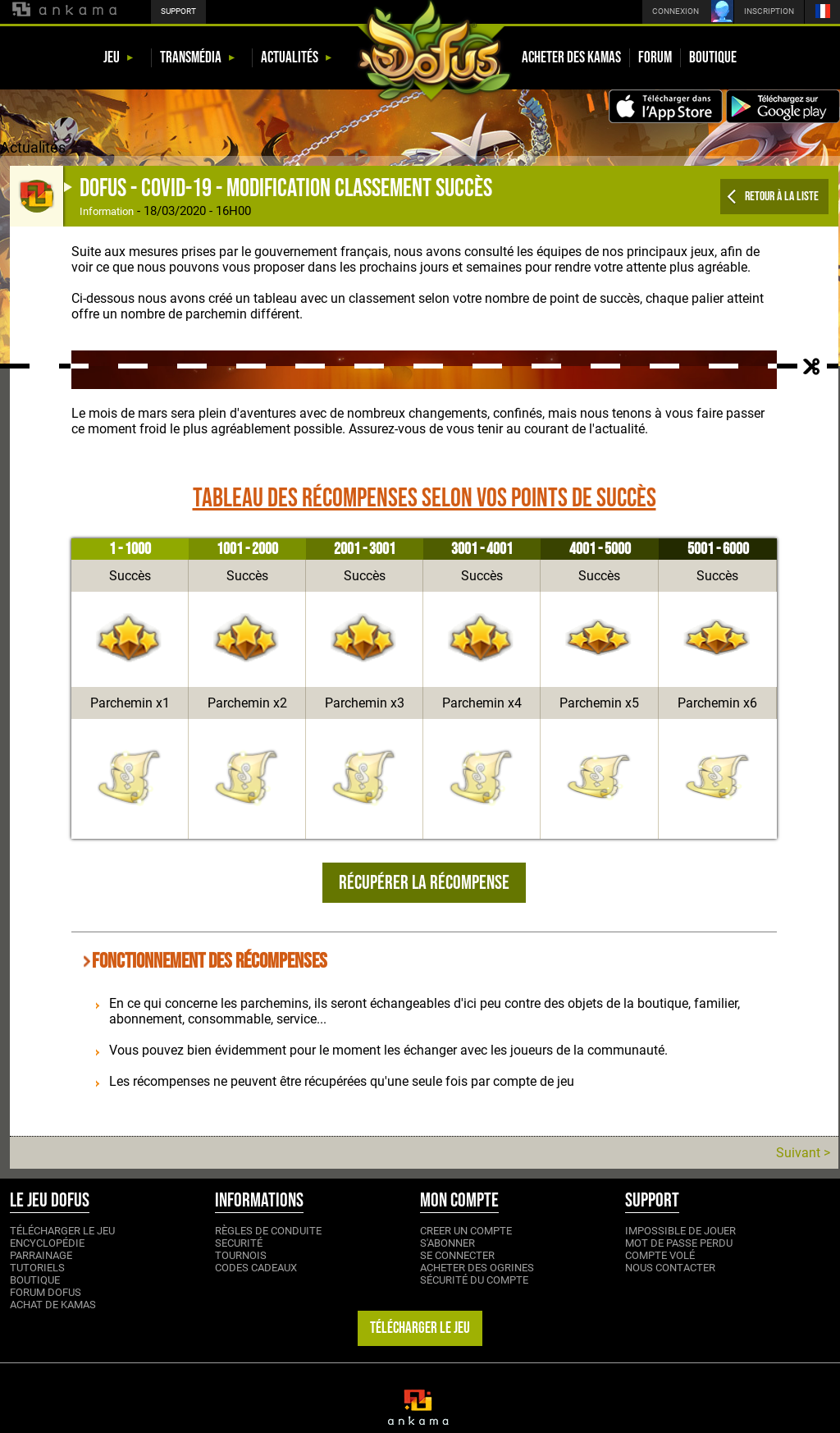
Fake blog posing as the real Ankama blog enticing victims to give away their credentials in exchange for a game bonus to use during the lockdown
Website defacements with Coronavirus messages
Criminals involved in a wide range of cybercrime activities are taking advantage of the attention surrounding Coronavirus. An ISIS-inspired web defacer plastered a series of German websites with the ISIS flag to inform visitors of the sites that “Germans will be destroyed by the Islamic State and the Corona Virus”.
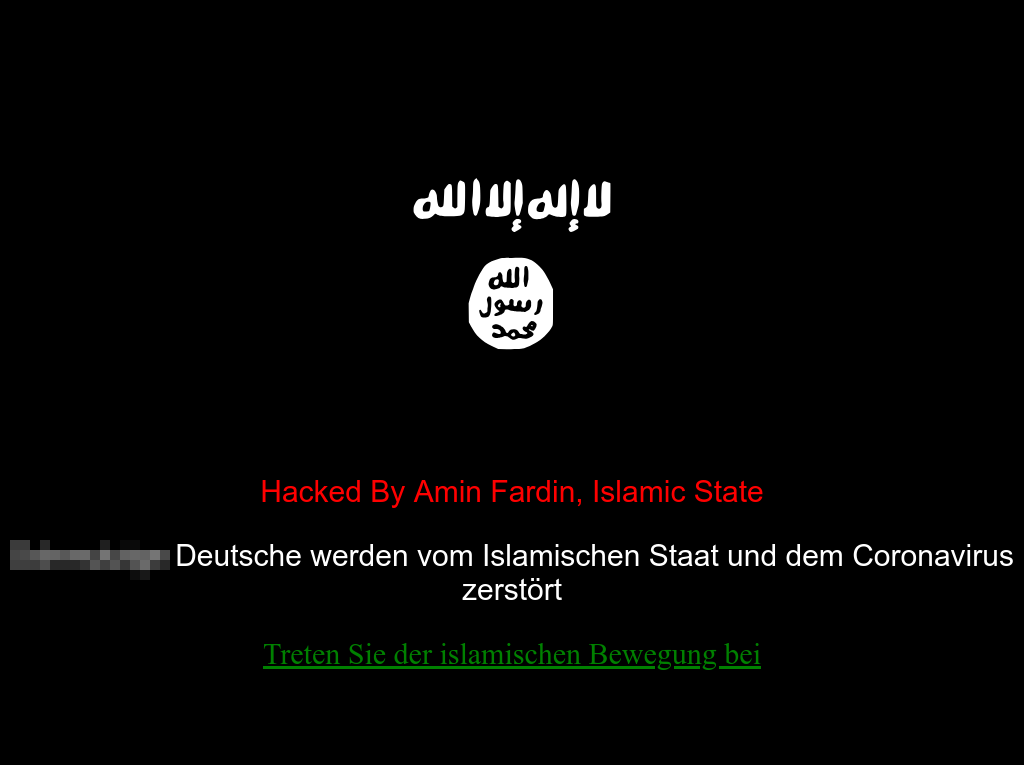
ISIS-inspired web defacement with a Coronavirus twist
Governments and industry respond
Governments have begun to respond with legislation to tackle Coronavirus-related cybercrime with Denmark taking some of the toughest action. Their new legislation introduces tougher penalties into the Danish criminal code: up to double the penalty if the crime exploits Coronavirus and quadruple if it involves a financial element as well. The legislation also adds provision for requiring Danish ISPs to block fraudulent Coronavirus-related websites at the DNS level.
Meanwhile EURid, the .eu registry, has added a requirement for all domain registrations which contain a Coronavirus or COVID-19 keywords to validate their registration information and submit a “good faith” statement within seven days.