Fraudsters are still exploiting eBay’s persistent cross-site scripting vulnerabilities to steal account credentials, years after a series of similar attacks took place. Worse still, many of the listings that exploited these vulnerabilities remained on eBay’s website for more than a month before they were eventually removed.
All of the attacks stem from the fact that eBay allowed fraudsters to include malicious JavaScript in auction descriptions. Previous attacks exploited this vulnerability to place malicious redirect code on high-value vehicle listings, with the intention of stealing login credentials from other eBay members, whose accounts could then be used to list even more fraudulent vehicle listings.
But fraudsters are now using malicious scripts on a wide variety of lower-value items, including legitimate listings that had already been posted from reputable eBay accounts. Fraudsters have seemingly compromised these accounts and appended additional information to many of the members’ existing listings – and this is where the malicious JavaScript is placed.
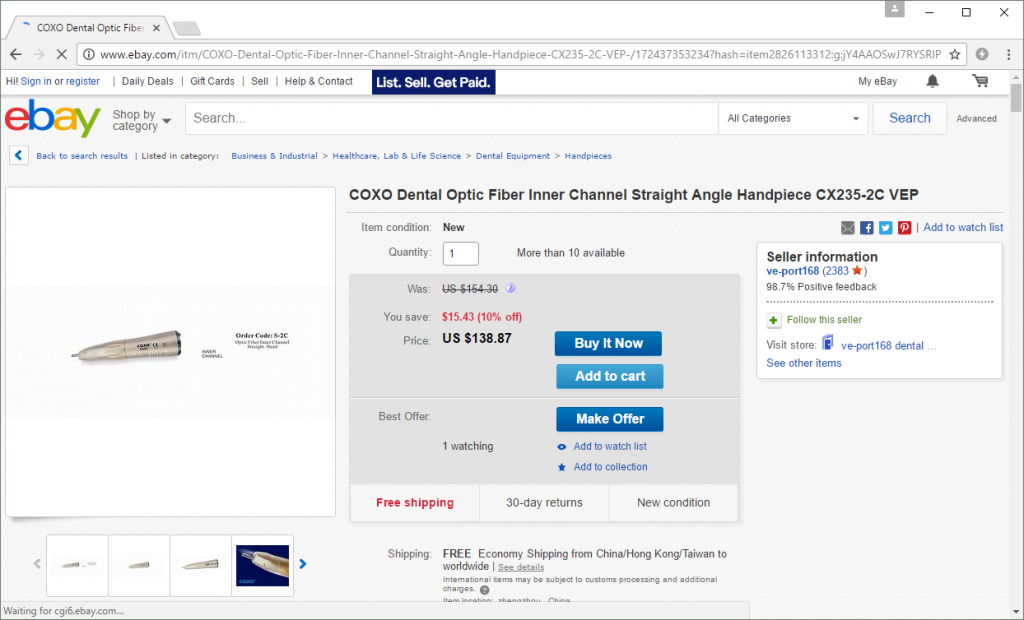
As can be seen below, the cybercriminals even used listings of dental tools to extract credentials from their victims, bypassing eBay’s toothless listing policies in a similar way to the attacks that took place a few years ago.
 A compromised listing for a dental tool from a Chinese seller as it appeared in eBay search results.
A compromised listing for a dental tool from a Chinese seller as it appeared in eBay search results.
Clicking on the above listing took the user to the following page, which included malicious JavaScript that had been injected by the fraudster:
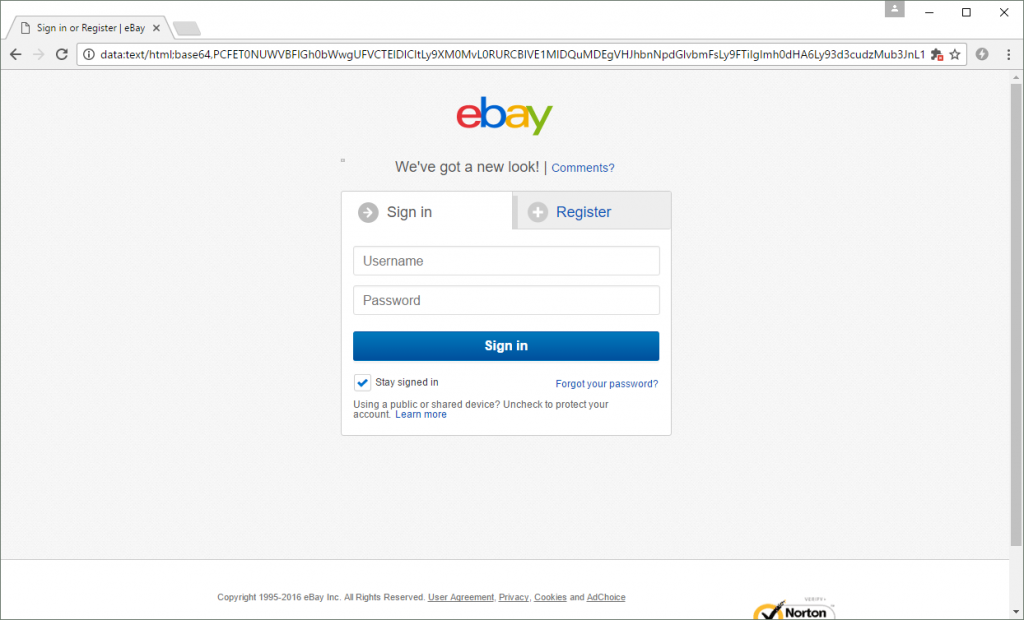
But the malicious code in this listing executes as soon as the page has loaded, which causes it to be displayed for only a split second. In the blink of an eye — and without any further interaction — the victim is redirected to a spoofed login form:
Victims are unlikely to expect a phishing form to appear as a result of clicking on an eBay search result, and so the efficacy of these attacks is likely to be far greater than the average phishing scam. Allowing listings to include arbitrary JavaScript not only facilitates this type of fraud, but also allows fraudsters to capitalize on the trust instilled by the eBay website.
In this particular example, the malicious code injected by the attacker was obfuscated to make its purpose less apparent – possibly to get around any text-based content filters implemented by eBay. The obfuscated script is used to load a much larger JavaScript payload from an external location at user54631.vs.easily.co.uk/v.js (this script, which was hosted by Easily, has since been removed).
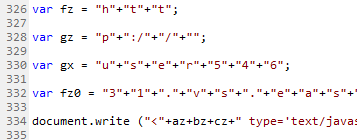 Lightly-obfuscated malicious JavaScript as it appeared in an eBay listing
Lightly-obfuscated malicious JavaScript as it appeared in an eBay listing
The externally-hosted script redirected victims to a data URI, which is another trick sometimes used by cybercriminals: The Base64-encoded address makes it difficult for victims to report such attacks, as by this point, the page is ostensibly not hosted anywhere.
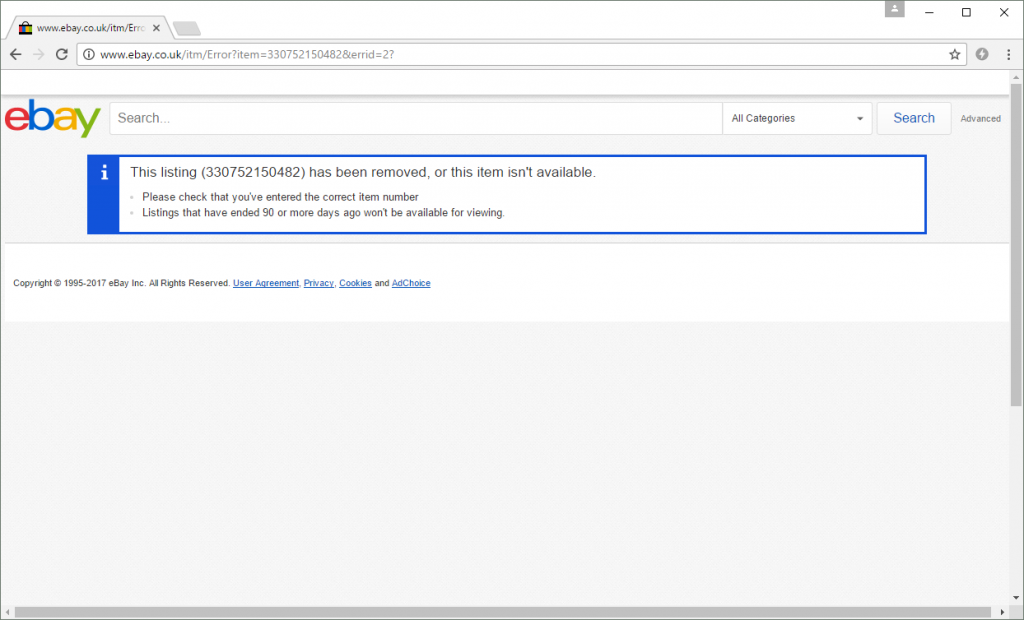
When the victim submits his username and password, the credentials are transmitted to a script at daviddouglas.co.uk/session.php?/ws/eBayISAPI.dll?co_partnerId=2&siteid=3&UsingSSL=1 (which has also since been taken down). This PHP script receives the victim’s credentials and then immediately redirects the victim to a page on the genuine eBay website, giving the impression that the listing that the victim originally attempted to visit is no longer available:
The victim may not realise it — as his browser never showed the address of any externally hosted websites — but at this point, his credentials will have already been stolen by the fraudster’s PHP script.
The fraudsters behind these attacks can attempt to monetize these stolen credentials by selling them to other fraudsters, or use them to propagate malicious code into even more listings. In the dental tool example, malicious JavaScript was added to the listing on 8 December 2016, and remained there until late January 2017, giving the fraudster more than a month and a half to exploit the vulnerability.
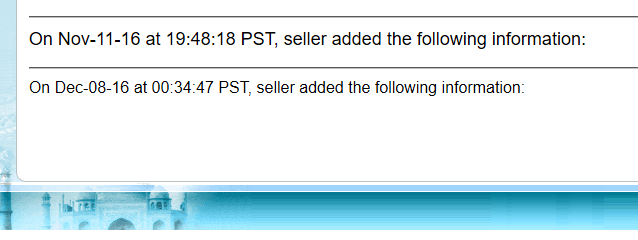 The malicious script (not visible) was added on 8 December 2016, and eBay continued to serve it for a month and a half.
The malicious script (not visible) was added on 8 December 2016, and eBay continued to serve it for a month and a half.
The compromised seller account involved in the above attack had over a thousand of its listings infected with malicious JavaScript, many of which flew under eBay’s radar for more than a month, despite having obvious malicious intentions. The only deterrent is eBay’s JavaScript policy, which disallows the use of JavaScript redirects – but this is evidently not entirely effective, as it failed to prevent it being exploited for extended periods, and fraudsters will obviously not care about breaking policies that are not proactively enforced.
These latest listings were reported to Netcraft by “Jaco Bustero”. Although this pseudonym is very similar to “Buster Jack” — who discovered a series of related scams in 2014 — they are, in fact, different people in the UK. Both hide behind pseudonyms because of valid concerns about their own safety – for instance, Buster Jack’s efforts to combat vehicle fraud have earned him several death threats from the perpetrators of these crimes.
But fortunately, the end of script-based attacks may soon be in sight on eBay. In an effort to make its listings mobile-friendly, eBay plans to limit the use of active content (such as JavaScript) at some point in 2017, before eventually blocking it altogether. If this is implemented as a technical control (for example, by using iframes with Content Security Policy and sandbox restrictions), then such attacks should become impossible to carry out against modern browsers.
The most recent attacks have taken place over the past 12 months, after eBay had responded to ‘previous reports‘ of JavaScript-based attacks, when it claimed not to have found any fraudulent activity stemming from these cross-site scripting vulnerabilities.
In some cases, it could be that eBay is simply unaware of the fraud it is facilitating. When one customer phoned eBay Trust & Safety to report these redirect attacks, the eBay handler was unable to see the redirection due to security settings on their internal systems. Consequently, reporting such vulnerabilities to eBay can prove frustrating, as well as fruitless: When Jaco posted a similar warning to the eBay Motors community forum, he claims his message was quickly deleted.
A year ago, we predicted that it would be difficult to prevent this type of fraud when listings are still able to include arbitrary JavaScript. With these recent attacks proving eBay’s interim measures are still insufficient to prevent abuse, only technically-enforced controls on the execution of JavaScript will finally put a stop to this fraud.