An ongoing phishing attack against UK taxpayers is being given additional credibility by using a gov.uk domain. Sefton Council is hosting the phishing content on its Novel GroupWise 7.0 site at web11.sefton.gov.uk.
The phish follows one of the typical ploys commonly seen in HMRC and IRS phishing attacks: The victim is led to believe that they can receive a tax refund by submitting their full credit card details, but these details are instead sent directly to the fraudster behind the attack.
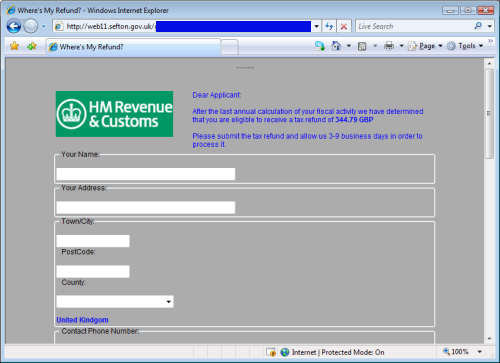
The fraudulent form submits the victim’s details to a PHP script hosted at www.zamoh.biz.
The UK’s Central Office of Information is responsible for deciding who can register gov.uk domains. Eligibility is strictly limited, which helps to preserve the integrity of the gov.uk namespace; however, this obviously has an undesirable effect when this integrity is leveraged by fraudulent content on compromised servers. Netcraft has informed Sefton Council about this phishing attack.
Netcraft provides an Automated Vulnerability Scanning service which regularly tests your internet infrastructure, supplies the information you need to maintain your security and eliminate vulnerabilities, and audits that it has found no serious vulnerabilities using a dynamically generated seal.