Fraudsters are abusing Facebook’s app platform to carry out some remarkably convincing phishing attacks against Facebook users.
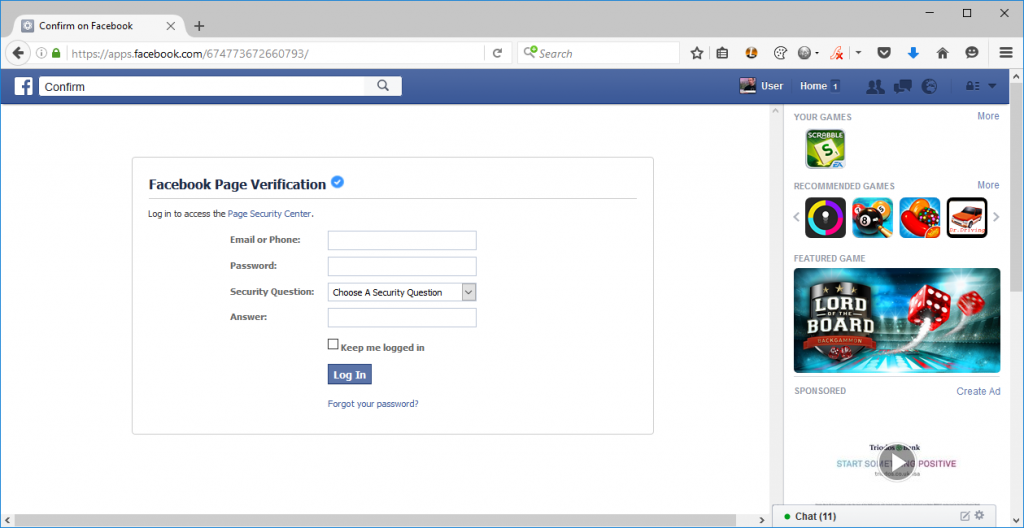
Masquerading as a Facebook Page Verification form, this phishing attack leverages Facebook’s own trusted TLS certificate that is valid for all facebook.com subdomains. This makes the page appear legitimate, even to many seasoned internet users; however, the verification form is actually served via an iframe from an external site hosted by HostGator. The external website also uses HTTPS to serve the fraudulent content, so no warnings are displayed by the browser.
This phishing attack works regardless of whether the victim is already logged in, so there is little chance of a victim being suspicious of being asked to log in twice in immediate succession.
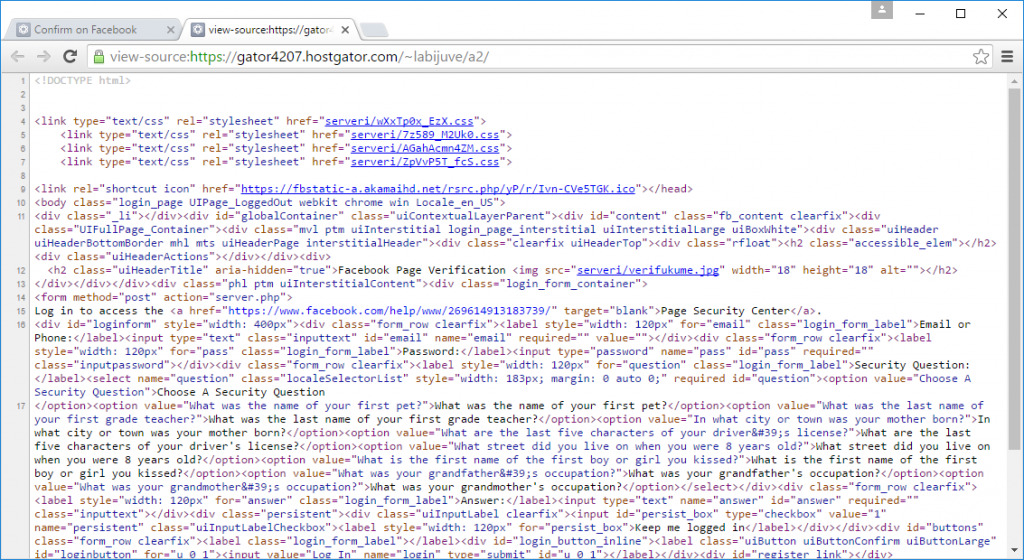 The source code of the phishing content reveals that it sends the stolen credentials directly to the fraudster’s website.
The source code of the phishing content reveals that it sends the stolen credentials directly to the fraudster’s website.
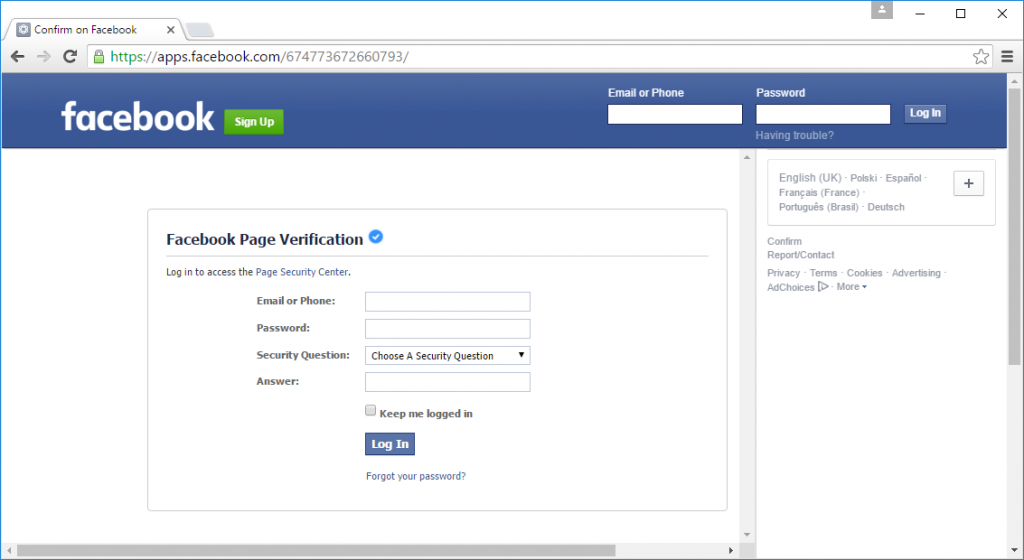
To win over anyone who remains slightly suspicious, the phishing site always pretends that the first set of submitted credentials were incorrect. A suspicious user might deliberately submit an incorrect username and password in order to test whether the form is legitimate, and the following error message could make them believe that the credentials really are being checked by Facebook.
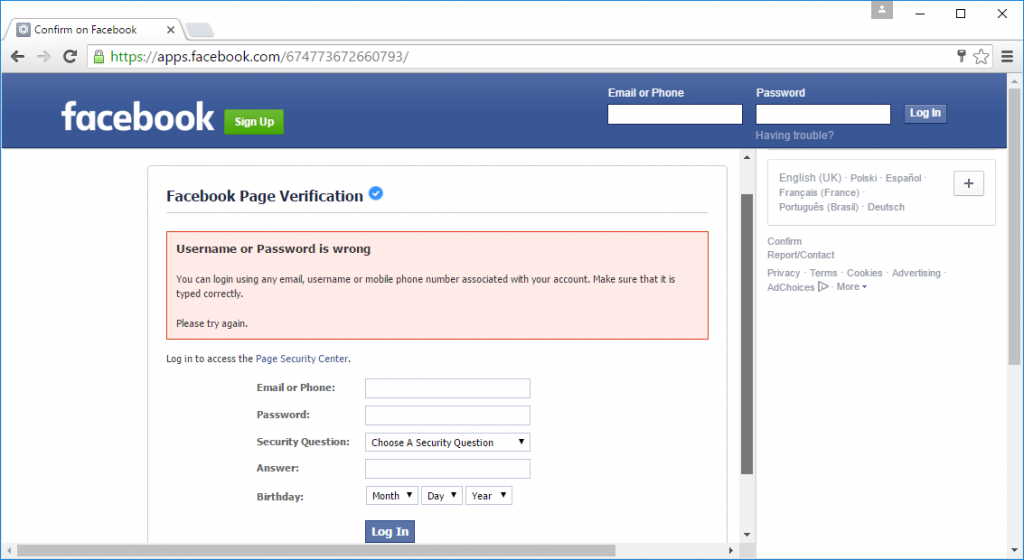 The phishing site always pretends the first submitted credentials are incorrect. Note that it now also asks for the victim’s date of birth.
The phishing site always pretends the first submitted credentials are incorrect. Note that it now also asks for the victim’s date of birth.
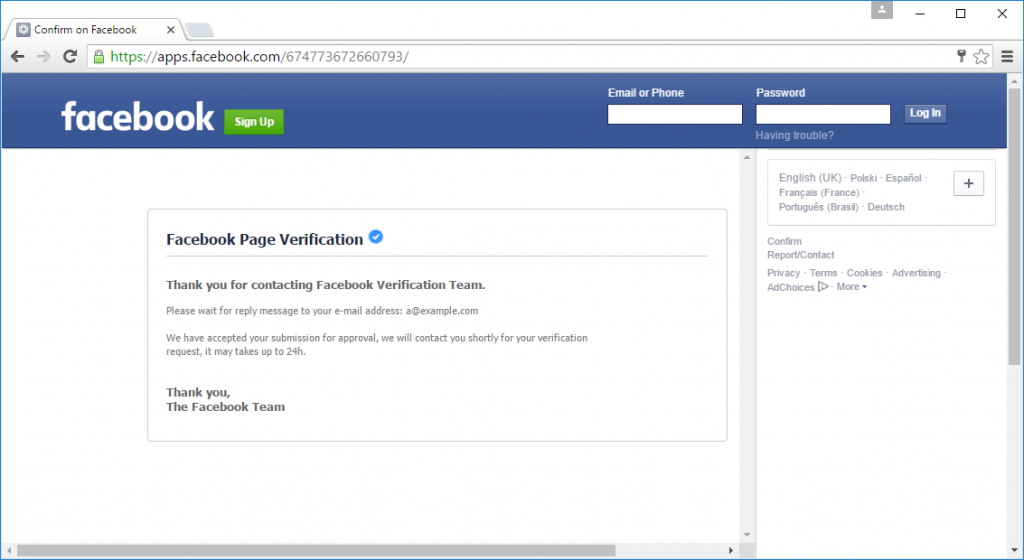
Those who were slightly suspicious might then believe it is safe to enter their real username and password. Anyone else who had already entered the correct credentials would probably just think they had made a mistake and try again. After the second attempt, the phishing site will act as if the correct credentials had been submitted:
The final response indicates that the victim will have to wait up to 24 hours for their submission to be approved. Without instant access to the content they were trying to view, the victim will probably carry on doing something else until they receive the promised email notification.
But of course, this email will never arrive. By this point, the fraudster already has the victim’s credentials and is just using this tactic to buy himself some time. He can either use the stolen Facebook credentials himself, or sell them to others who might monetize them by posting spam or trying to trick victims’ friends into helping them out of trouble by transferring money. If more victims are required, then the compromised accounts could also be used to propagate the attack to thousands of other Facebook users.
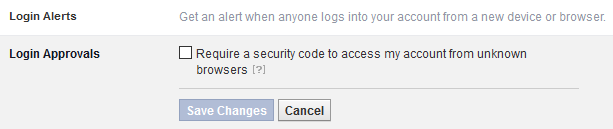 Some of Facebook’s security settings.
Some of Facebook’s security settings.
However, Facebook does provide some features that could make these attacks harder to pull off. For example, if login alerts are enabled, the victim will be notified that their account has been logged into from a different location – this might at least make the victim aware that something untoward is going on. Although not enabled by default, users can completely thwart this particular attack by activating Facebook’s login approvals feature, which requires a security code to be entered when logging in from unknown browsers. Only the victim will know this code, and so the fraudster will not be able to log in.