An extremely convincing phishing attack is using a cross-site scripting vulnerability on an Italian Bank’s own website to attempt to steal customers’ bank account details. Fraudsters are currently sending phishing mails which use a specially-crafted URL to inject a modified login form onto the bank’s login page.
The vulnerable page is served over SSL with a bona fide SSL certificate issued to Banca Fideuram S.p.A. in Italy. Nonetheless, the fraudsters have been able to inject an IFRAME onto the login page which loads a modified login form from a web server hosted in Taiwan.
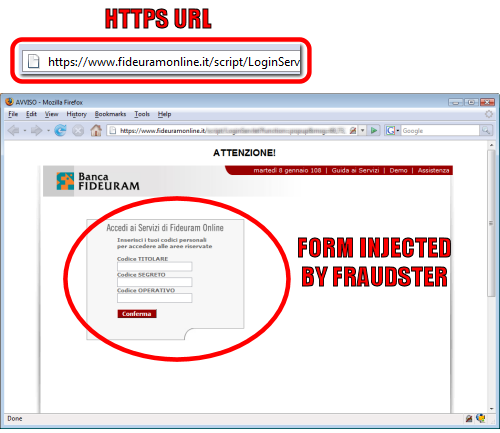
The fraudsters’ login form presented inside the bank’s SSL page.
This attack highlights the seriousness of cross-site scripting vulnerabilities on banking websites. It shows that security cannot be guaranteed just by the presence of “https” at the start of a URL, or checking that the browser address bar contains the correct domain name.
Cross-site scripting vulnerabilities on SSL sites also undermine the purpose of SSL certificates – while the attack detailed here injects external content via an IFRAME, it is important to note that a malicious payload could also be delivered solely via the vulnerable GET parameter. In the latter case, any SSL certificate associated with the site – included Extended Validation certificates – would display a padlock icon and apparently assure the user that the injected login form is genuine.
This particular attack is made all the more convincing by the vector used by the fraudsters: the URL employed by the attack injects a series of numbers directly into a JavaScript function call that already exists on the bank’s LoginServlet page. This makes it difficult even for an experienced user to identify this as a cross-site scripting attack, as the URL does not look readily suspicious, with the injected content consisting only of numbers and commas.
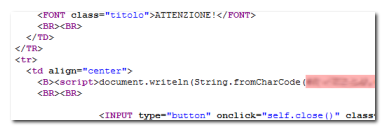
The vulnerable page, decoding arbitrary GET parameters.
In a possible attempt to bypass automated security filters, the injected content from Taiwan also contains encoded JavaScript which is used to display the text “Inserisci i tuoi codici personali” (“Insert your personal codes”) and “per accedere alle aree riservate” (“To access all reserved areas”). When the modified form is submitted, the contents are transmitted to the Taiwanese server before the user is redirected to the bank’s genuine, unaltered homepage.
Netcraft has contacted the bank affected by this attack and blocked the phishing site for all users of the Netcraft Toolbar, and propagated the block to the companies which licence the Netcraft PhishFeed.