MasterCard.com has been taken down after a second distributed denial of service attack by Anonymous. The first attack occurred 3 days ago, after which Visa and PayPal were also successfully attacked.
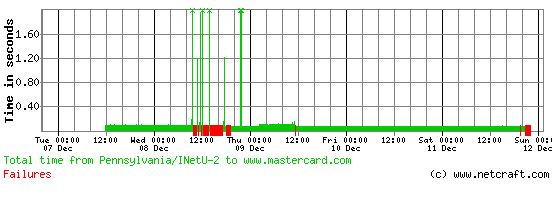
MasterCard’s payment processing systems were affected during the first DDoS attack on Wednesday, with many consumers reporting that they were unable to pay for goods online. Businesses reported a corresponding drop in trade during that first attack.
Anonymous struck out against MasterCard after the credit card giant announced a move to ensure that WikiLeaks would not be able to accept payments using MasterCard-branded products. Anonymous also tried to attack Amazon.com in retaliation for terminating WikiLeaks’ EC2 web hosting services, but the first attempt did not succeed.
This second attack against MasterCard was announced in IRC channels, on Twitter and on http://anonops.eu. The group’s previous website was suspended on Wednesday. The new site is hosted at OVH in France, where wikileaks.ch is also hosted.
IRC remains an important component in the group’s command and control structure. Thousands of volunteers have installed the LOIC attack software, which receives its next attack instructions from the group’s IRC network.
The total number of computers involved in these attacks is unclear, as some volunteers have been experiencing difficulties connecting to the IRC network and so have been running the software manually. Additional volunteers have also been using a browser-based version of the attack tool, which can be run without having to install any software. Some of the previous attacks have involved at least 2,000 computers.
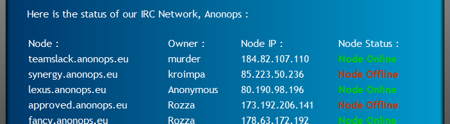
The group’s IRC network has continued to grow and is now spread across 18 servers. Not only does this allow more users to connect, but it also makes the IRC network more resilient to attacks and other outages.
This latest attack against MasterCard was initially directed towards www.mastercard.com. A few hours later, the target was changed to mastercard.com, which was served from a different IP address. When www.mastercard.com became accessible again, the homepage contained the following statement …
“MasterCard has made significant progress in restoring full-service to its corporate website. Our core processing capabilities have not been compromised and cardholder account data has not been placed at risk. While we have seen limited interruption in some web-based services, cardholders can continue to use their cards for secure transactions globally.”
… however, its corporate website at mastercard.com then became innaccessible due to the DDoS attack.
Real-time performance graphs for www.mastercard.com, mastercard.com and several other sites involved in the WikiLeaks attacks can be monitored at http://uptime.netcraft.com/perf/reports/performance/wikileaks