A recurrent group of Moroccan fraudsters calling themselves Mr-Brain has launched a website dedicated to offering easy-to-use phishing site code, email templates and other hacking tools. The website offers phishing kits for many of the most common targets, such as Bank of America, eBay, PayPal and HSBC.
The tools and code provided by Mr-Brain are designed to make it extremely easy for other fraudsters to deploy realistic phishing sites. Only a very basic knowledge of programming is required to configure the PHP scripts to send victims’ details to the fraudsters’ chosen electronic mail address. Deploying one of these fully working kits can be done in as little as one minute – another factor that adds to their appeal.
Tricking the Fraudsters
Mr-Brain’s intentions are to encourage as many people as possible to use their phishing kits, for all is not what it seems at first glance. Careful inspection of the configuration script reveals deceptive code that hides the true set of electronic mail addresses that are contacted by the kit – every fraudster who uses these kits will unwittingly send a copy of each victim’s details back to the Mr-Brain group.
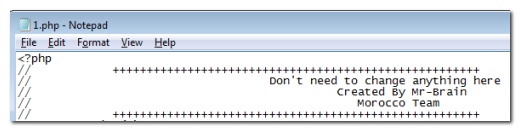
The configuration script exploits the case-sensitivity in PHP variable names to disguise Mr-Brain’s electronic mail address as an unrelated but seemingly essential part of the script, encouraging fraudsters not to alter it. The injected electronic mail address is actually contained in a completely separate PHP file, where it is encrypted in a hidden input field named “niarB”, or “Brain” backwards. Yet another PHP script reads the value from this input field and decrypts it before supplying it to the configuration script. Most fraudsters are unlikely to notice this level of obfuscation and will assume the script is working normally, as they will also receive a copy of any emails produced by the script.
When Netcraft decrypted the contents, the hidden input field revealed one of Mr-Brain’s Gmail addresses, which is used to covertly capture details from all of the phishing kits that have been deployed on their behalf by other fraudsters. A comment at the top of one of the scripts aims to deter these fraudsters from examining the script that decrypts the hidden field:
Earlier this month, Netcraft also exposed a similar phishing scam targeting Bank of America. This, too, was authored by Mr-Brain and was configured to covertly send harvested credentials to a different Gmail address.
Each phishing kit listed on their website is accompanied by a description, showing what kind of information it steals from victims. One page on their website lists a selection of Social Security numbers, credit card numbers and PINs under the heading “Free and Freash [sic] Credit Card”.
Mr-Brain claims that all of the scam pages offered on its site are undetected by Mozilla, Opera and Internet Explorer. Netcraft blocks these sites when they are detected by the Netcraft Toolbar community, and propagates the block to all companies which licence the Netcraft Phishing Site Feed.