A new internet browser, Comodo Dragon, reports that more than half of the world’s valid SSL certificates are unsafe.
Comodo Dragon is based on the open source Chromium project, but includes additional security and privacy features. In particular, when a user browses to a site that uses a domain-validated SSL certificate, Comodo Dragon will warn the user that the site may not have undergone trusted third-party validation.
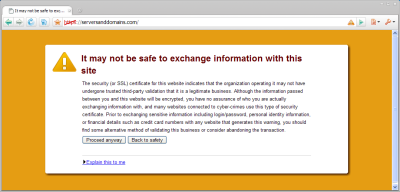
Users are presented with buttons to “Proceed anyway”, or go “Back to safety”. The warning message explains why such a site is deemed to be unsafe:
The security (or SSL) certificate for this website indicates that the organization operating it may not have undergone trusted third-party validation that it is a legitimate business. Although the information passed between you and this website will be encrypted, you have no assurance of who you are actually exchanging information with, and many websites connected to cyber-crimes use this type of security certificate. Prior to exchanging sensitive information including login/password, personal identity information, or financial details such as credit card numbers with any website that generates this warning, you should find some alternative method of validating this business or consider abandoning the transaction.
Mainstream adoption of this behaviour would have a huge impact on e-commerce — more than half of the SSL certificates in use on the web are domain-validated, and this market continues to show strong growth due to the generally lower costs and ease of issuance when compared with organisation and extended validation certificates.
However, none of the popular browsers provides an explicit warning when browsing to a domain-validated site. With such widespread use of domain-validated certificates, it would undoubtedly lead to uproar if any of these browsers were to display warnings when users browse to domain-validated sites.
Although Comodo states that many websites connected to cyber-crimes use domain-validated certificates, Netcraft’s phishing site feed shows that only 0.3% of reported phishing sites use HTTPS, including those running on compromised servers with SSL certificates already in place.
Netcraft found 683,563 valid domain-validated certificates in its March 2010 survey. Go Daddy has issued more than half of these, which it currently sells at $29.99 per year for new purchases.
Comodo itself is also a sizable player in the domain-validated SSL market, accounting for 7.6% of all domain-validated certificates. Ironically, domain-validated certificates signed by Comodo are also reported as being potentially unsafe, including those sold via hosting companies such as DreamHost.
DreamHost’s CTO, Dallas Kashuba, told Netcraft: “I think the information being presented about the nature of the SSL certificate is useful, but the approach Comodo has taken to present the information is heavy-handed and seems a bit too close to “crying wolf”. I worry that users of the browser will see that warning so frequently that they will become desensitized to all warnings.”
Last year, DreamHost launched an amusing tirade against certificate authorities, criticising the “entirely automated” process of issuing domain-validated certificates. To prove a point, DreamHost then began offering domain-validated certificates to existing customers for only $15, stating: “…we’re not making anything on them because we feel the whole business is a scam!”
DreamHost’s Kashuba also told Netcraft: “I think Extended Validation SSL certificates are a good way to reduce the impact of phishing and other similar nefarious activities, but is not a necessary expense for most secure websites.”
There is no doubt that upsetting the current level of trust in domain-validated certificates would cause problems: Many FDIC members continue to use domain-validated certificates for their banking sites, including Bank of the Sierra, Bank of Hawaii, TierOne Bank and Great Western Bank.
For additional information or details on how to order the Netcraft SSL Survey, please contact us at sales@netcraft.com.