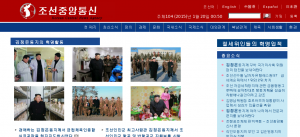
North Korea’s presence on the internet has remained extremely patchy for more than a month, with little improvement since a suspected DDoS attack that took place just before Christmas.
The state-run Korean Central News Agency website at www.kcna.kp has been barely reachable since Christmas day. Only 13% of requests to the site succeeded during the past month, with the worst period being around the end of January when the site became completely unavailable for several days in a row from our network of performance monitors.
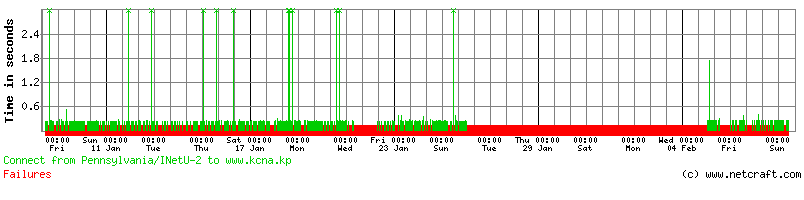
Although the articles on www.kcna.kp are written in multiple languages, the KCNA clearly acknowledges that North Korea has never been an ideal location to host material that is intended for global consumption — for greater dissemination, the agency continues to publish articles to a secondary site at www.kcna.co.jp, which is hosted at a much more reliable location in Japan.
Even so, both of these sites remain deliberately inaccessible from some parts of the world. Access to both has been blocked in South Korea, and addresses in New Zealand were blocked after scraping content to be used on the KCNA Watch website, which tracks North Korean media.
When they do succeed, most requests to www.kcna.kp are met with an HTTP 1.0 response, which renders as a blank page. These responses can take a few minutes to be received:
$ curl -i http://www.kcna.kp HTTP/1.0 200 OK Connection: Close Pragma: no-cache cache-control: no-cache Refresh: 0.1 Content-Type: text/html; charset=iso-8859-1 <!DOCTYPE html PUBLIC "-//W3C//DTD HTML 4.01//EN" "http://www.w3.org/TR/1999/REC-html401-19991224/strict.dtd"> <!-- <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN" "http://www.w3.org/TR/html4/strict.dtd"> --> <HTML> <HEAD> <META HTTP-EQUIV="Refresh" CONTENT="0.1"> <META HTTP-EQUIV="Pragma" CONTENT="no-cache"> <META HTTP-EQUIV="Expires" CONTENT="-1"> <TITLE></TITLE> </HEAD> <BODY><P></BODY> </HTML>
Occasionally, www.kcna.kp will return its proper content in a HTTP 1.1 response which uses JavaScript to redirect the browser to http://www.kcna.kp/kcna.user.home.retrieveHomeInfoList.kcmsf, but this page — as well as all of the images and scripts it uses — suffers from similar performance issues, making the site practically unusable from many locations outside of North Korea.
Roughly half of the small number of websites hosted in North Korea, including www.kcna.kp, use Apache 2.2.15 running on the Linux-based Red Star 3.0 operating system. The Korea Computer Center (which also administers the .kp top-level domain) released this version of Red Star in 2013, but it was not until the end of last year that the rest of the world gained hands-on experience with it after an ISO image of the installation disk was distributed via bittorrent.
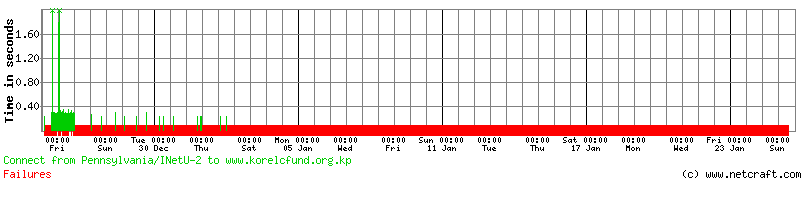 One of the sites using Apache 2.2.15 and Red Star 3.0 is the Korea Elderly Care Fund website at www.korelcfund.org.kp, which seemed to disappear completely for a few weeks after Christmas.
One of the sites using Apache 2.2.15 and Red Star 3.0 is the Korea Elderly Care Fund website at www.korelcfund.org.kp, which seemed to disappear completely for a few weeks after Christmas.
The rest of North Korea’s websites are served by Apache running on CentOS, which is a free operating system derived from the sources of Red Hat Enterprise Linux. Websites using this platform in North Korea include the Korea National Insurance Corp site at www.knic.com.kp and the Committee for Cultural Relations with Foreign Countries at www.friend.com.kp, which ironically failed to respond to 84% of requests from our network of performance monitors.
Two years ago, Netcraft noted that kcna.kp used to run on Apache 2.2.3 with Red Hat Enterprise Linux 5. As this Linux distribution is owned, distributed and supported by an American multinational company, it is subject to U.S. export controls, which specifically prohibit its use in North Korea. As a result, this installation was likely unlicensed and so may not have received security updates, and would certainly not have received any official support.
North Korea normally has a very small presence on the internet, even when everything is working properly. Before the alleged attacks, Netcraft’s Web Server Survey found 916 million websites around the globe, but only 24 of these sites were hosted in North Korea. To put that in perspective, you would have more chance of winning the UK’s National Lottery jackpot than you would of randomly picking a North Korean website out of our survey.
Despite having an estimated population of 25 million people, North Korea has relatively few IP addresses of its own – just 1,024 in total. A third of the websites hosted in North Korea are served from a single IP address within this block, so a successful DDoS attack against this address is likely to take out several sites at once.
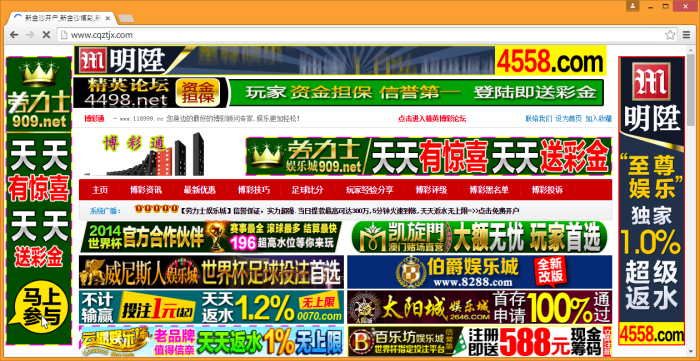 Hosted on an IP address assigned to North Korea, cqztjx.com is plastered with adverts for online gambling services.
Hosted on an IP address assigned to North Korea, cqztjx.com is plastered with adverts for online gambling services.
In addition to North Korea’s 1,024 native IP addresses, a block of 256 IP addresses in the range 5.132.126.0 – 5.132.126.255 has also been assigned to an End User in North Korea. These addresses appear to be used solely for hosting online gambling websites on virtual private servers. This block is marked as ASSIGNED PA, which means it is not permanently allocated to North Korea; the range will be lost if the local issuing internet registry, Outside Heaven, terminates its services.
inetnum: 5.132.126.0 - 5.132.126.255 netname: OUTSIDEHEAVEN_MUTI-IP_VPS descr: OUTSIDEHEAVEN_MUTI-IP_VPS infrastructure country: KP admin-c: OHS18-RIPE tech-c: OHS18-RIPE status: ASSIGNED PA
North Korea’s other additional assigned network block at 77.94.35.0 – 77.94.35.255 does not currently appear to be used for hosting websites.