The cross-site scripting (XSS) vulnerability, which was harnessed by fraudsters to execute a convincing phishing attack against PayPal users, may have been exploitable for two years previously.
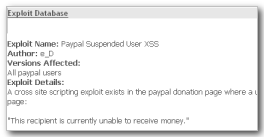
Despite the prompt action taken by PayPal to address the security flaw after it was reported by Netcraft last month, it became apparent that the very same flaw had been discovered and documented two years earlier. The page – cached by the Wayback Machine – describes a cross site scripting attack that affected donation pages for suspended users, and is the exact method exploited by the phishing attack in June 2006.
Chris Marlow tried to warn PayPal about the flaw in June 2004, but claims the PayPal representative he spoke to did not understand what cross-site scripting was, and – due to company policy – was unable to provide an email address to allow a proof-of-concept exploit to be demonstrated. Frustrated at being unable to convey the seriousness of the issue, Mr Marlow then posted details about the exploit to his web site but did not receive any response from PayPal.
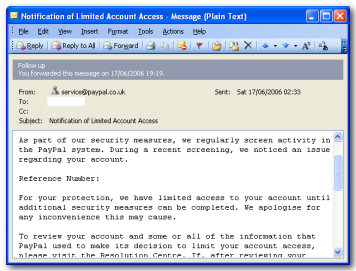
PayPal fixed the flaw after reports of the phishing attack were published by Netcraft. A PayPal company spokesman initially said that they did not know how many people had fallen victim to the scam, although as the fraud was committed using PayPal’s own web site, analysis of log files, if available, would have allowed PayPal to identify users at risk and take appropriate action.
Netcraft offers a Web Application Security Testing service, which can discover a number of security flaws, including cross-site scripting vulnerabilities like these.