The redirector at kickme.to/has.it forwards to a Barclays spoof site hosted at Pochta.ru in Moscow. The spoof loads a page from the actual Barclays site, and then launches a data collection form in a pop-up window from the Russian server:
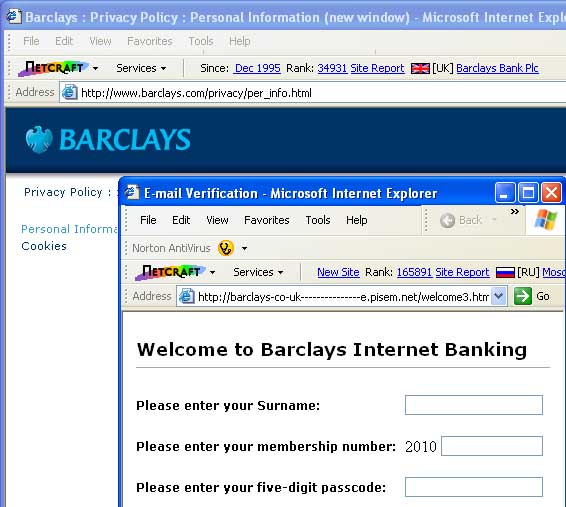
Barclays is aware of the fraud and has posted a warning to customers on its web home page. Some of the URLs function only in selected browsers. For example, the URLs using the pipe character will resolve on Windows XP, but not Linux. Windows XP browsers support a broader character set to accommodate migrations from Windows NT4, which allows the use of the pipe character in identifying network assets.
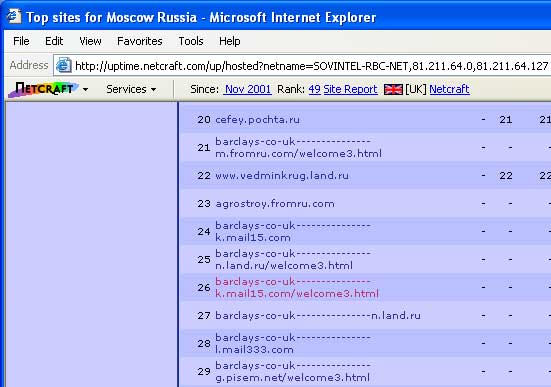
Some of the URLs stop working as redirection functions at kickme.to go offline. But the spoofed pages remain online at Pochta’s Moscow server, which houses four of the domains hosting scam pages (pisem.net, mail333.ru, mail15.com and from.ru), which are brazenly using the hyphenated “barclays-co-uk” in subdomains:
The Netcraft Toolbar offers protection against such phishing scams and will prevent access to these phishing URLs. Netcraft also provides a range of other anti-phishing services to banks and financial institutions and a phishing countermeasures service that can offer to close down phishing sites quickly and effectively.