Phishers are still using look-alike domain names to steal Steam credentials from unsuspecting victims, which suggests that this approach is proving rather successful for the criminals. These types of attack are particularly effective if carried out within Steam’s own browser, which lacks the protective features seen in most mainstream browser software.
Since Netcraft first highlighted this issue in June last year, nearly a third of all phishing attacks against Steam users continue to make use of look-alike domains. Some of these domain names, such as "steamcornmunity.com", look practically identical to the real steamcommunity.com domain, particularly when displayed in the address bar of the built-in Steam browser:
Look-alike domains play a particularly important role in Steam phishing attacks, as victims are often tricked into visiting these phishing sites by fraudsters sending messages through Steam’s own chat client or by enticing them to visit links in forum posts. These spearphishing attacks are obviously more likely to succeed if a victim believes the link is going to take him to the genuine Steam Community website.
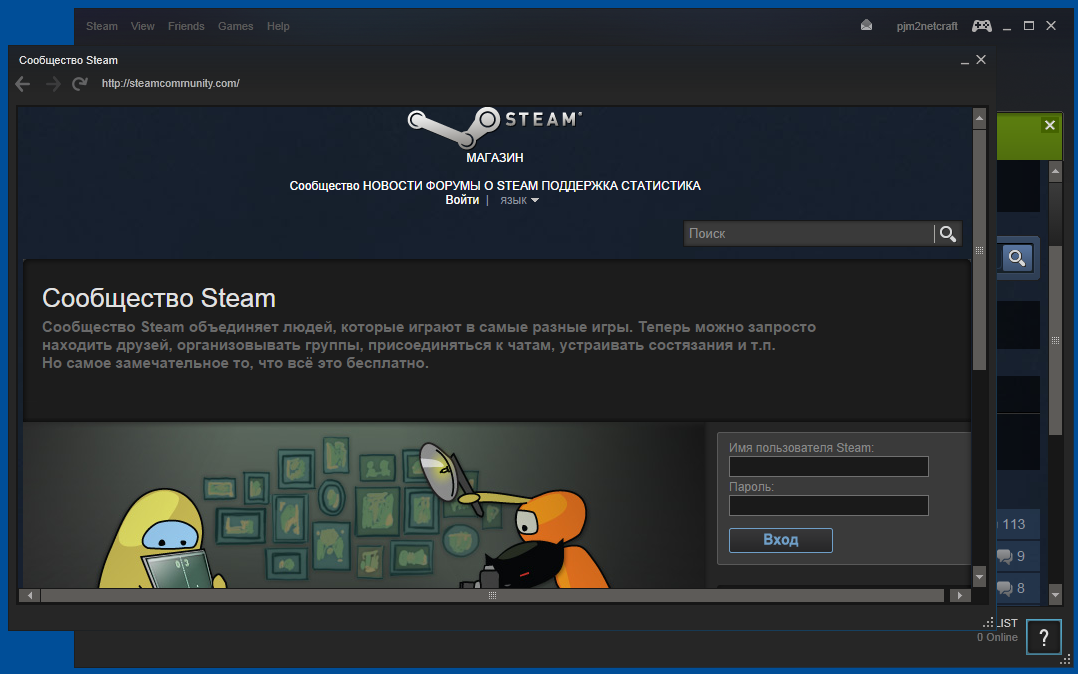 First seen more than a year ago, the look-alike domain steamcomrnunity.com is still being used for Steam phishing attacks today. After stealing a victim’s credentials, it redirects the browser to the genuine Steam Community website.
First seen more than a year ago, the look-alike domain steamcomrnunity.com is still being used for Steam phishing attacks today. After stealing a victim’s credentials, it redirects the browser to the genuine Steam Community website.
It is very unusual for such a high proportion of a target’s phishing attacks to make use of custom paid-for domain names. The vast majority of phishing attacks against other targets, such as banks, are typically hosted on existing compromised websites (where the domain name obviously cannot be changed), or make use of specially crafted subdomains on free hosting platforms.
Many of the other attacks against Steam users fall into the latter category, attempting to mimic the Steam brand by using less-convincing subdomains that are cheaper or free to obtain. Examples of these have included stempowered.16mb.com, steamsupportcom.esy.es and steamcomnunity.besaba.com.
Netcraft has blocked a total of 2,000 unique Steam phishing URLs in the past three months alone. Interestingly, more than 600 of these URLs were used by attacks carried out on Christmas day. This is often thought to be a good time for these types of attack, as many technical support and customer services representatives are generally unavailable during this period. This gives the fraudsters additional time to monetize stolen accounts, as it is likely to be a few days before anyone can respond to a victim’s compromised account enquiries.
Steam Trading makes it possible to monetize stolen Steam accounts, and provides an obvious incentive to go phishing on Steam. This in turn explains why many users have opted to increase the security of their accounts by enabling Steam Guard, which is essentially a two-factor authentication mechanism. Even if the phisher manages to steal a victim’s Steam username and password, he will not be able to log into the account without also submitting a special access code.
The special access code is sent to the victim via email, so in order to fully compromise the Steam account, the fraudster must also compromise the victim’s email account, trick the victim into disabling Steam Guard, or trick him into submitting the access code on behalf of the fraudster. Many of the previous attacks enticed victims to download and run a SteamGuard.exe executable, which was actually malware designed to steal a special authentication file from the victim’s computer. This allowed the Steam Guard protection to be bypassed whilst also paving the way for instant trading by eliminating the new-device time delay protection which would have applied if only the access code was stolen.
2% of the domains used in these attacks make use of the .ru top-level domain (steamsommunlty.ru, for example) rather than the more intuitive .com. This choice of TLD is perhaps no coincidence, as some of the fake Steam Guard binaries point to a website called SteamComplex, which also uses a .ru top-level domain.
Hosted on the CloudFlare content distribution network, steamcomplex.ru is written in Russian and appears to be selling the Steam malware used in these attacks. Many of the Steam phishing attacks, such as the one shown in the screenshot above, are also clearly aimed at Russian speakers.
Is Steam doing enough to protect its users?
The ongoing recurrence of these attacks suggests that Steam might not taking the appropriate action to deal with these phishing sites, or if it is, its actions are ineffectual. For example, the steamcomrnunity.com look-alike domain has been serving the same Russian phishing content for around a month. It is hosted at a place which is usually responsive to takedown requests, which strongly indicates that no effort has been made to take it down.
Additionally, when victims are redirected from a known phishing site to the real Steam site, the location of the phishing site is revealed in the HTTP Referer header (shown below). This would allow the Steam Community website to recognise that the user’s credentials may have just been phished, but it does not take the opportunity to display any warnings in the victim’s browser.
GET / HTTP/1.1
Host: steamcommunity.com
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:33.0) Gecko/20100101 Firefox/33.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-GB,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://steamcomrnunity.com/
Cookie: [removed]
Connection: keep-alive
Finally, while all mainstream browsers deny access to known phishing sites like the ones shown above, Steam’s own built-in browser does not. This lack of blocking, coupled with the easily-spoofed address bar, makes the Steam browser remarkably vulnerable to these attacks.
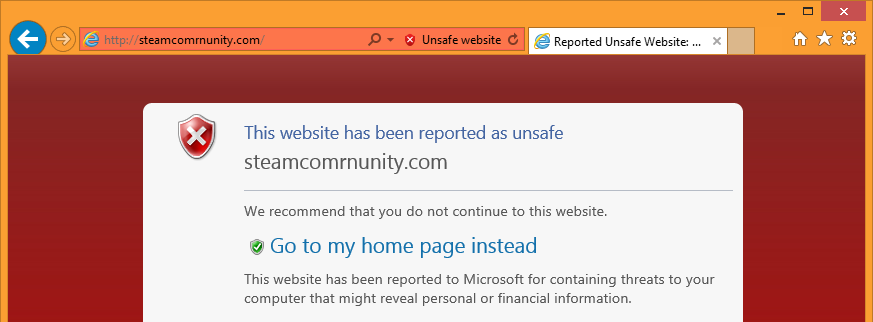 The “steamcomrnunity.com” phishing site is blocked natively within Internet Explorer. The domain in the address bar is also displayed more clearly, allowing sharp-eyed users to identify it as fake.
The “steamcomrnunity.com” phishing site is blocked natively within Internet Explorer. The domain in the address bar is also displayed more clearly, allowing sharp-eyed users to identify it as fake.
In mitigation, some users have noticed that the Steam chat client has started removing some of these malicious links in recent days, which will hopefully limit the effectiveness of the chat-based attack vectors.
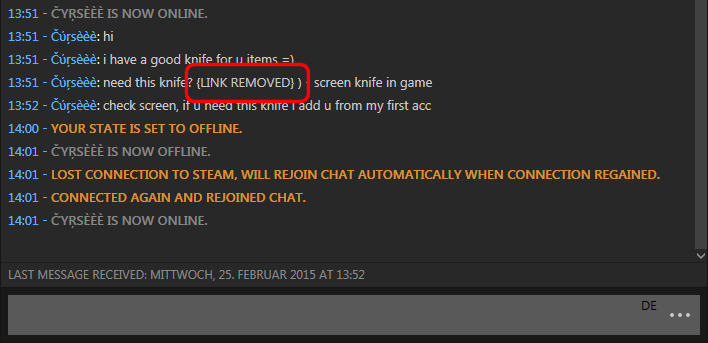 A malicious link removed from a Steam chat message (highlighted).
A malicious link removed from a Steam chat message (highlighted).
Netcraft’s phishing site feed is used by all mainstream browsers. For more information about this and our phishing site takedown service, please contact us at sales@netcraft.com.