Netcraft has to date identified nearly 10,000 websites used in the distribution of the FluBot family of Android malware. As detailed in our previous articles on FluBot, these sites are unwittingly hosting a PHP script that acts as a proxy to a further backend server, allowing otherwise legitimate sites to deliver Android malware to victims. When visited by the intended victim, a “lure” is displayed that implores them to download and install the FluBot malware.
The most common lure themes are parcel delivery and voicemail messages, where the user is told to install the malicious app to track a parcel or listen to a voicemail message. One particularly interesting lure took advantage of FluBot’s infamy, by offering a fake “Android security update” that claimed to protect against the malware family. Users installing this “security update” would instead be infected with FluBot.
Most sites distributing FluBot malware also host legitimate content, suggesting they were compromised by the operators of this malware distribution network, without the knowledge of the site operator. While the use of unrelated domains makes the lures less convincing, as compared to domains specifically registered for fraud, it allows the malware distribution network to operate at a much larger scale.
These affected sites all have one factor in common: they run self-hosted WordPress instances. Netcraft believes the operators of this malware distribution network are actively exploiting well-known vulnerabilities in WordPress plugins and themes to upload malicious content onto insecure sites, joining a growing list of threat actors doing the same.
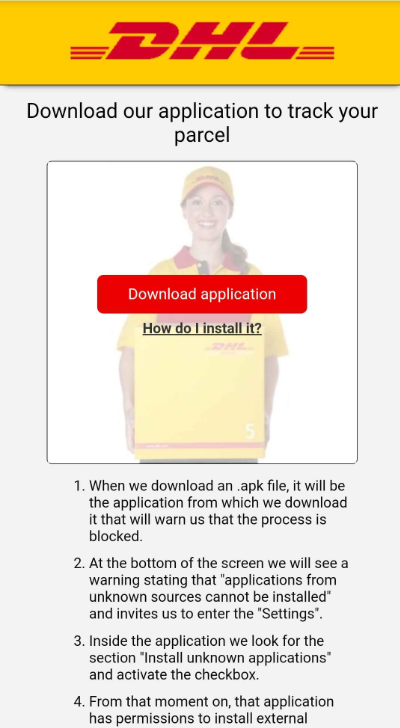

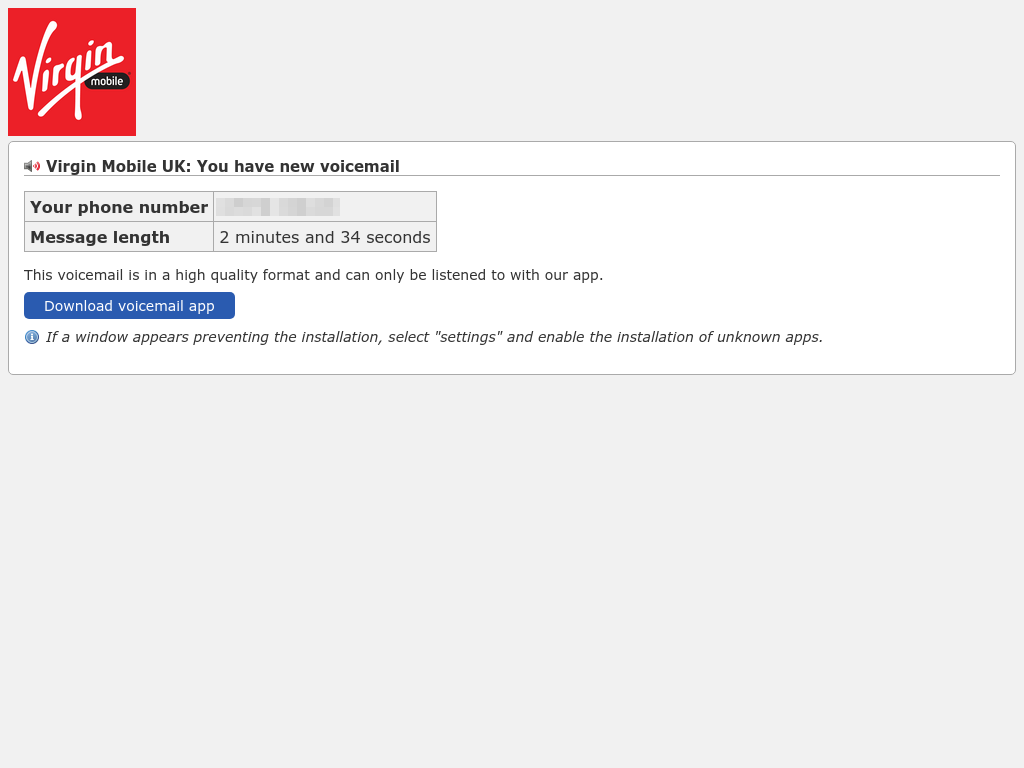
A collection of lures used by the FluBot distribution network
What’s in a WordPress plugin?
WordPress is an extremely popular Content Management System (CMS) – used in 42% of the top 10 million websites – that allows sites to host content including online shops, news, educational sites, and general-purpose websites. Many of these roles are made possible by a large ecosystem of community-contributed plugins and themes.
WordPress uses PHP for server-side scripting, with a MySQL or MariaDB database providing persistent data storage. This makes WordPress sites very flexible; themes and plugins, depending on server configuration, may:
- Make arbitrary changes to the site, including modifying all site content, configuring user accounts, and altering and extending the WordPress admin tools.
- Run commands in the context of the web server user (usually
www-dataorapache), which may open the door to privilege escalation, and give the attacker access to other systems on the same network. - Communicate with other systems on the Internet.
- Change parameters of the web server itself, using an
.htaccessfile.
With almost 60,000 published WordPress plugins, a large number of vulnerabilities are publicly known. One scanning vendor claims to have a database of nearly 25,000 security issues from across the WordPress ecosystem. Previous Netcraft research indicates cybercriminals have been exploiting vulnerable WordPress sites for over a decade.
Common plugin weaknesses include Cross-Site Scripting (XSS), where attacker-controlled content is included within the page content; SQL Injection, where an attacker can exploit improperly formed SQL commands to execute their own statements; and arbitrary file uploads, allowing an attacker to place their own files on the server. Arbitrary file uploads admitting PHP scripts are particularly dangerous, as they can grant attackers full access to the WordPress instance as the web server user.
Widely-available tools allow attackers to enumerate plugins installed on a WordPress server, identify their versions, and to list any known vulnerabilities. Similar tools are able to automatically compromise the site, requiring little to no technical knowledge, and are distributed by crime-as-a-service threat actors. These tools are used by other criminals for purposes including site defacement, hosting phishing kits, performing Distributed Denial of Service (DDoS) attacks, and sending spam mail.
One example of a serious vulnerability is an arbitrary file upload vulnerability in the Contact Form 7 plugin, known as CVE-2020-35489.
Contact Form 7’s page on WordPress.org
Contact Form 7 is one of the most popular WordPress plugins, with more than five million active installs as of writing. CVE-2020-35489 is present in plugin versions prior to 5.3.2, which allow PHP files to be uploaded if the filename includes an unusual character, bypassing a filter that should disallow that file type. If PHP script execution is not disabled in CF7’s upload directory, an attacker can easily upload and execute a script such as a web shell and gain access to the rest of the WordPress installation. Around 20% of CF7 installs use a vulnerable version.
Affected site operators are victims of cybercrime
With their web servers broken into and used to distribute malware without their knowledge, affected site operators are the victims of cybercrime. The scale of this operation is impressive, with some weeks seeing more than 1,000 new sites infected with FluBot lures: an average of one site every ten minutes!
Unless the original vulnerability is rectified, other attackers will also be able to upload their own malicious content. Hosting malicious content puts the rest of the site at risk, as the ISP, hosting providers, or domain registrar may stop providing service to protect Internet users and their other customers. The site may also be added to block lists, removing it from search engines and displaying a security warning in most users’ browsers.
Official and government sites also affected
Of note is that several FluBot lures have been detected on the official sites of various government organisations. These include:
- The website of Manolo Fortich, a municipality of around 100,000 people in the Philippines.
- A currently-defunct website for Baghdad Airport, alongside cryptocurrency investment scams and web shells.
- A site used by Mesquita, a municipality of around 175,000 people in the state of Rio de Janeiro, Brazil.
- The site of the State Prosecutors of the Pasuruan Regency, representing a regency of population 1,500,000 in East Java, Indonesia.
In particular, websites associated with functions of the Indonesian Government are a relatively common host of scam content, with three other .go.id domains noted to host FluBot lure site scripts in the past. Netcraft have detected more than 400 attacks of various descriptions hosted on .go.id domains, including DPD parcel delivery scams, several cryptocurrency investment scams, web shells, and phishing attacks targeting brands including Netflix and Microsoft. Many of these official sites use WordPress.
The .go.id second-level domain is intended for official government use only, much like the .gov top- and second-level domains used elsewhere, making scams hosted under these domains particularly dangerous.
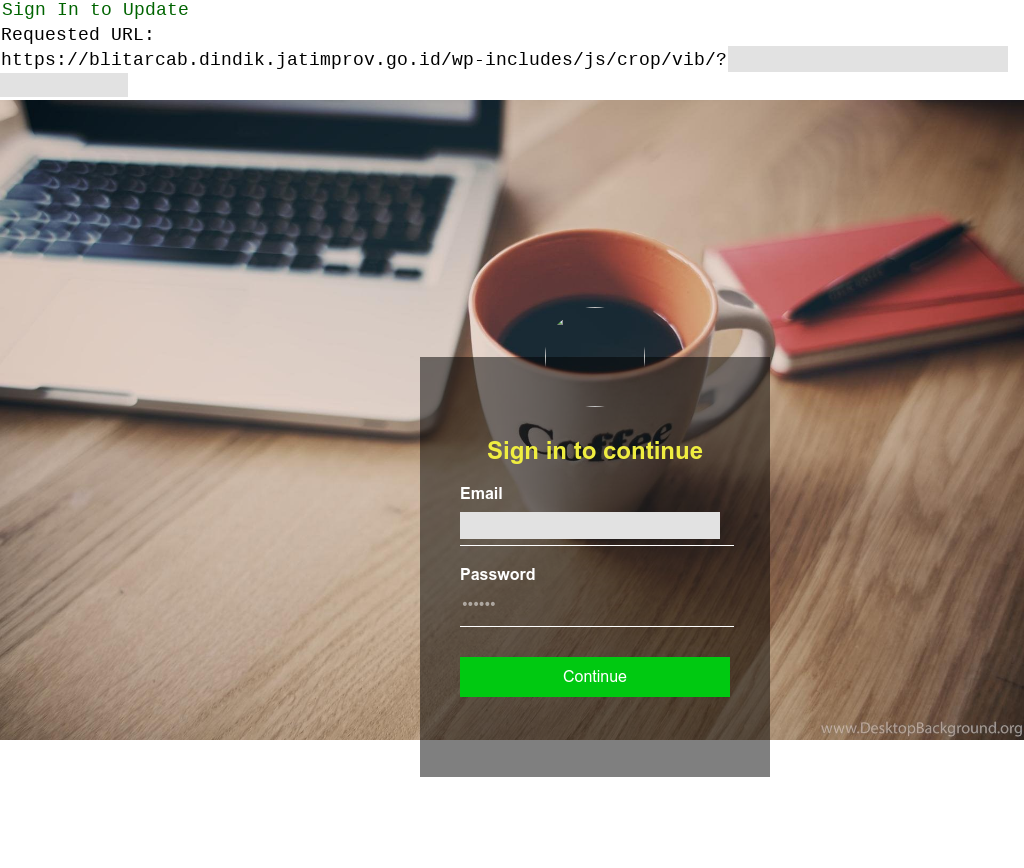
A generic phishing attack targeting email account credentials, hosted on a domain associated with the provincial educational office of East Java
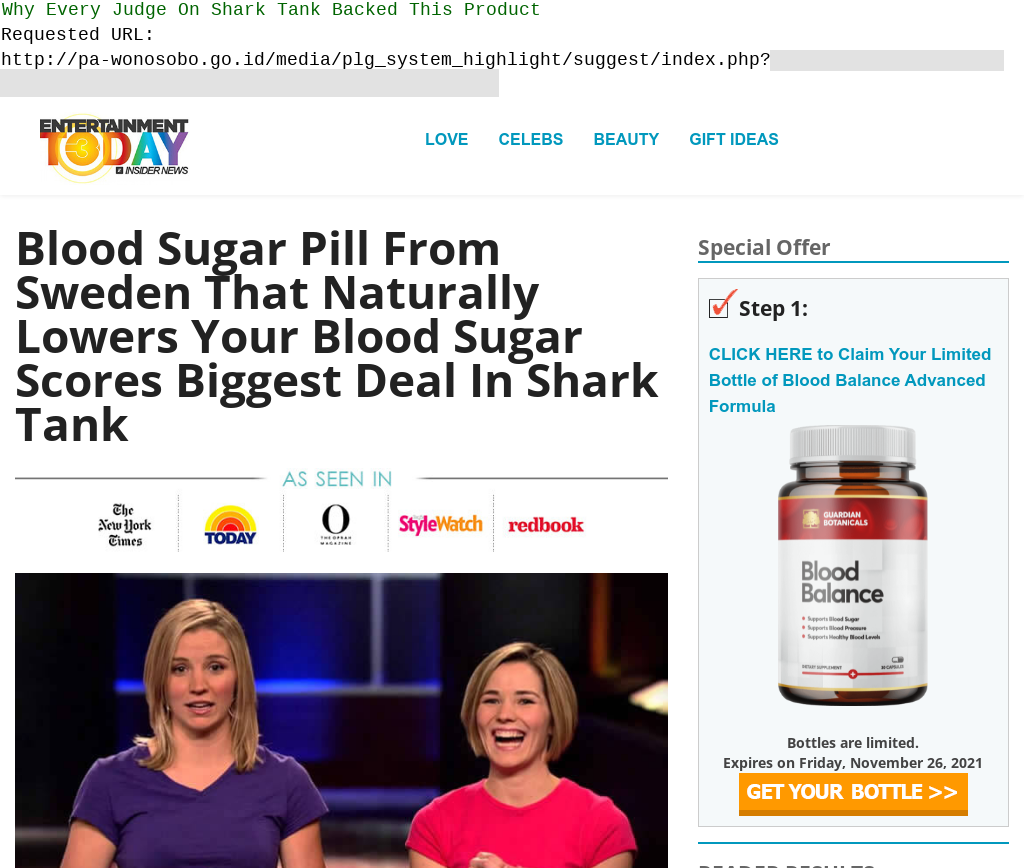
A health product scam accessible from a domain used by the Wonosobo Religious Court, Central Java
Protecting sites
Organisations can improve the security of their WordPress instances by following advice provided at WordPress.org, including:
- Considering the use of a hosted WordPress service, where many aspects of maintaining a WordPress instance is handled on your behalf. This may carry other risks.
- Keeping the web server itself, and WordPress’s core, plugins, and themes up-to-date.
- Removing unused and unmaintained plugins and themes, to reduce the WordPress instance’s attack surface.
- Restricting permissions for the web server user and its root directory, making important files and directories read-only where possible. This could include disallowing execution of server-side scripts outside of expected locations, and particularly in directories where user-uploaded files are stored.
- If the plugins and themes installed don’t require them, disable risky PHP functions and features, particularly those that can run commands (such as
exec,passthru,system, andshell_exec) or provide access to the network (file_get_contents, thecurlextension’s functions, and others).
While no computer system can be perfectly secure, hardening a WordPress instance can provide partial or complete mitigations for whole classes of vulnerabilities, including vulnerabilities that aren’t widely known. In the case of CVE-2020-35489, disabling script execution from Contact Form 7’s upload directory would make exploitation of that vulnerability much more difficult.
Protecting users
The Netcraft browser extension and apps use our malicious URL feeds to block dangerous content on the Internet, including FluBot lures, phishing sites, and fake shops.
Affected organisations are invited to get in touch with Netcraft to discuss our range of services, including our automated security scanning and web application security testing, which can help protect your business and customers by identifying known vulnerabilities in applications and services.