On 17th March Microsoft issued a security alert regarding a buffer overflow vulnerability which allows attackers to execute arbitrary code on Windows 2000 machines. The vulnerability is triggered by the Microsoft-IIS/5.0 implementation of the World Wide Web Distributed Authoring and Versioning (WebDAV) protocol and is specific to Microsoft-IIS/5.0 – WebDAV was not supported in Microsoft-IIS/4.0, and Microsoft-IIS/6.0 is reported to be unaffected.
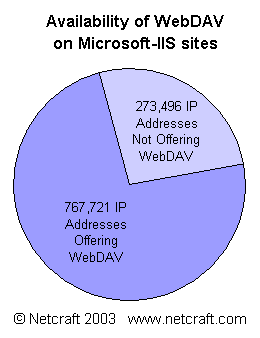
Microsoft-IIS/5.0 runs about 9 million web sites on just over 1 million ip addresses, making it the most widely deployed web server that has WebDAV enabled by default. Many sites disable WebDAV: best practice dictates that features that are not used should be disabled, and the IIS Lockdown tool recommended by Microsoft can disable WebDAV. However, although the number of sites that have disabled WebDAV is significant, our own data indicates that around three quarters of Microsoft-IIS/5.0 servers have WebDAV enabled, implying that at the time of announcement there were over 6 million vulnerable web sites.
The actual vulnerability occurs in a system DLL called by the WebDAV component, not in the WebDAV support itself. There may be ways to exploit this vulnerability via other components, or even other products. There is believed to be an exploit already in the wild for this vulnerability, and Windows 2000 administrators should apply the patch as soon as possible. CERT have issued an advisory (CA-2003-09), and Microsoft have issued a patch (see bulletin MS03-007).
The patch requires a reboot to become effective, and we have noticed that over half of the Microsoft-IIS/5.0 servers on the internet were rebooted during a two day period after the annoucement. The number of sites rebooting sets a lower bound on the uptake of the patch [a reboot is necessary as part of the patch installation] but will overstate the number of patched systems, as some sites will have rebooted for other reasons.