In the wake of the second US presidential election debate between Democrat Kamala Harris and Republican Donald Trump (September 10), Netcraft identified a series of crypto investment scams monopolizing on the publicity around this key event.
Our research uncovered 24 crypto-doubling scam domains related to the debate, including 14 phishing websites using the word “debate” in their domain, e.g. debatetrump[.]io, tesladebate[.]com, and debate[.]money.
All the examples exploit the image of Republican presidential nominee Donald Trump, tech entrepreneur and billionaire, Elon Musk, or a blend of both. Criminals likely use these personas to add legitimacy to their crypto investment theme—one political leader, one policy influencer, both conveying the perception of wealth and authority.
Netcraft observed similar tactics being used in attacks in March, during some of the earlier primary elections. In July, following the assassination attempt of Donald Trump, others were also discovered.
In the lead up to the US presidential election on November 5, we expect to see these kinds of attacks continue. To help brands and internet users act with greater caution during that time, this article analyzes the different variants from this latest, debate-themed scam. It also includes guidance for organizations at risk from similar impersonation of their brand, intellectual property (IP), and executive personas.
What is crypto-doubling?
Crypto-doubling scams lure victims into transferring cryptocurrency under the false pretence that their investments will be doubled. The perpetrators of these scams commonly use social engineering tactics via email, social media platforms, and messaging apps to coax victims into visiting a phishing website where the fraudulent transaction then takes place.
Crypto-doubling scams use the following tactics:
- Promises of quick returns, which often emphasize a rapid doubling of the victim’s investment.
- A sense of urgency to encourage immediate action.
- Fake endorsements that falsely claim support from public figures.
- A lack of transparency that withholds any real detail about the scheme.
Crypto doubling leaves harms victims financially and emotionally and impacts customer/voter trust in the brands and personas being imitated.
Variants
The three crypto-doubling variants identified through our research use similar tactics, but their variances reflect how criminals’ resource and time investment differs scam to scam. Individually and together, they help us understand the mindset behind this kind of malicious activity in greater depth.
Variant 1: “Elon Musk X Donald Trump Crypto Giveaway”
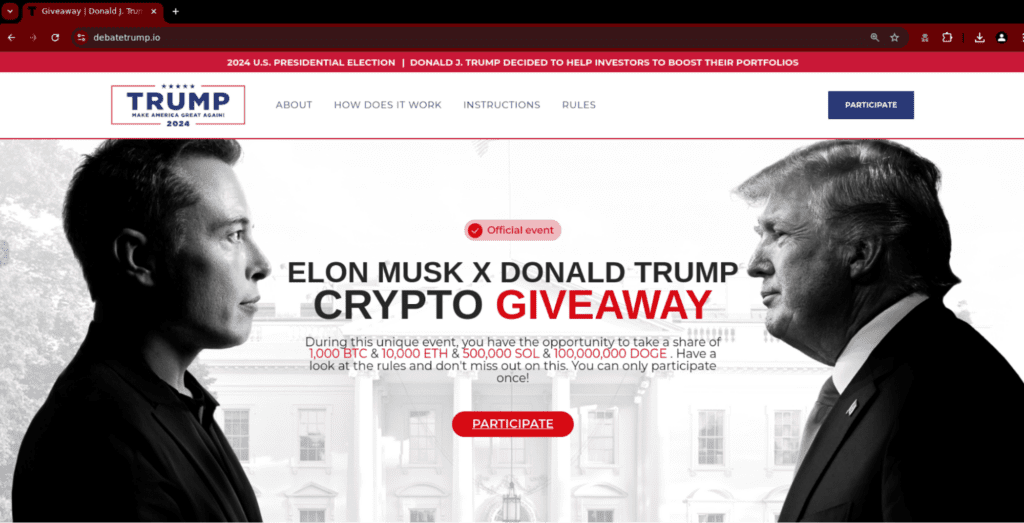
Fig. 1. Above the fold screenshot from the variant 1 website
In this first example, custom copy (see fig. 2.) and trusted brand logos are used to legitimize the website. The page content is rich, incorporating graphs and diagrams with step-by-step instructions and QR codes linking victims to a payment page.
Although the content itself doesn’t directly reference the debate it does use the domain debatetrump[.]io.
Off-brand language and grammatical errors—common telltale signs of fake content—still occur across the site, such as, “Donald Trump immersing himself in the world of cryptocurrency to offer a nice gift to cryptoinvestors” or simply “Check instruction”.

Fig. 2.
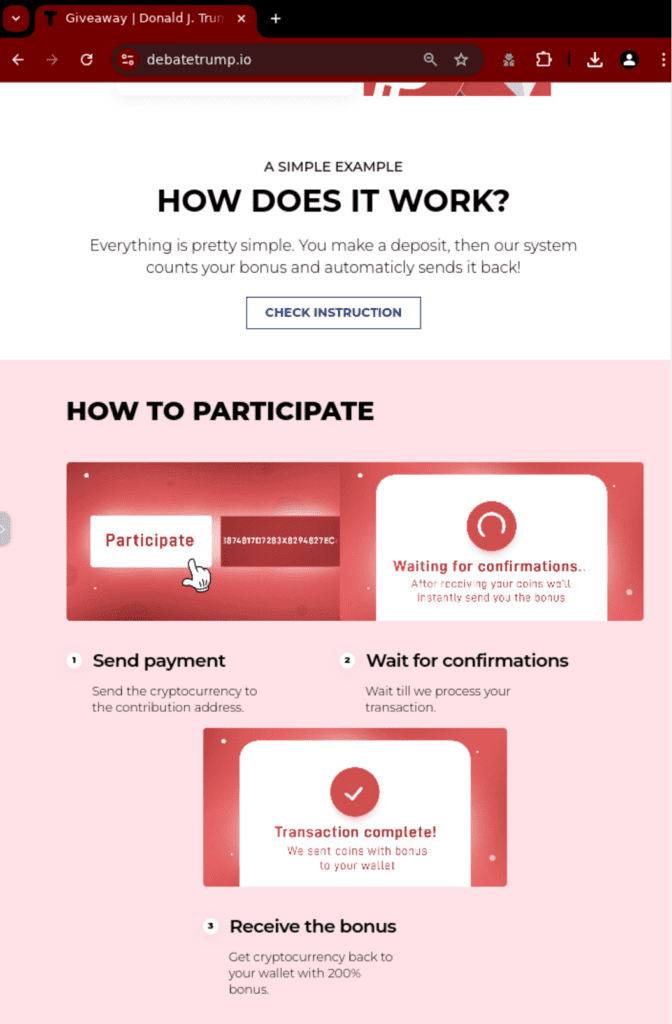
Fig. 3.
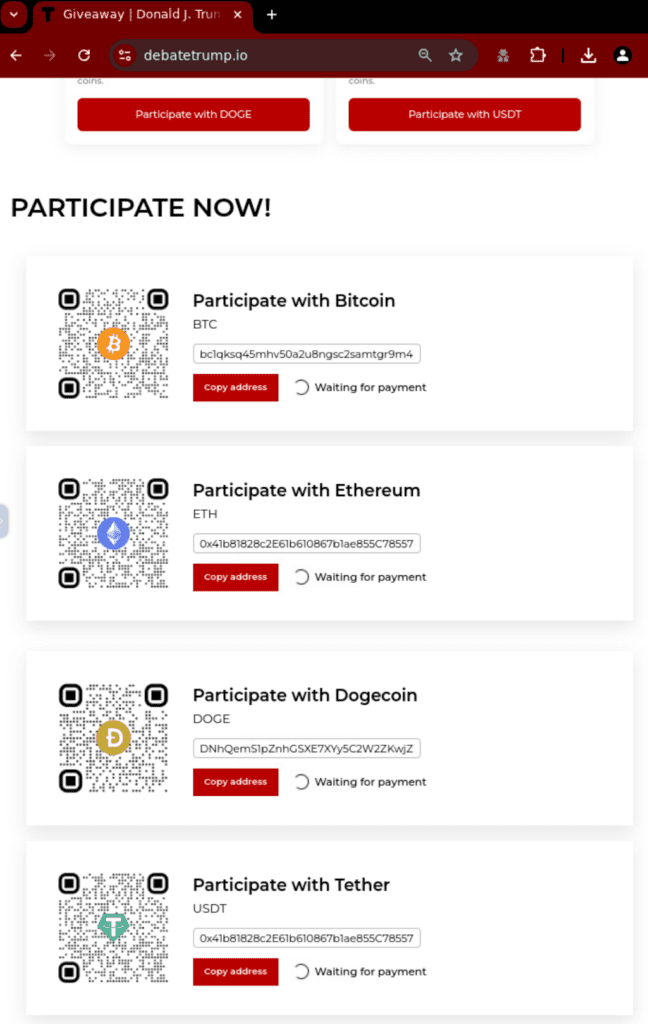
Fig. 4. (Fig. 2 – 4. Below the fold screenshots from the variant 1 website)
Variant 2: “Huge giveaway during Trump and Kamala Debate”
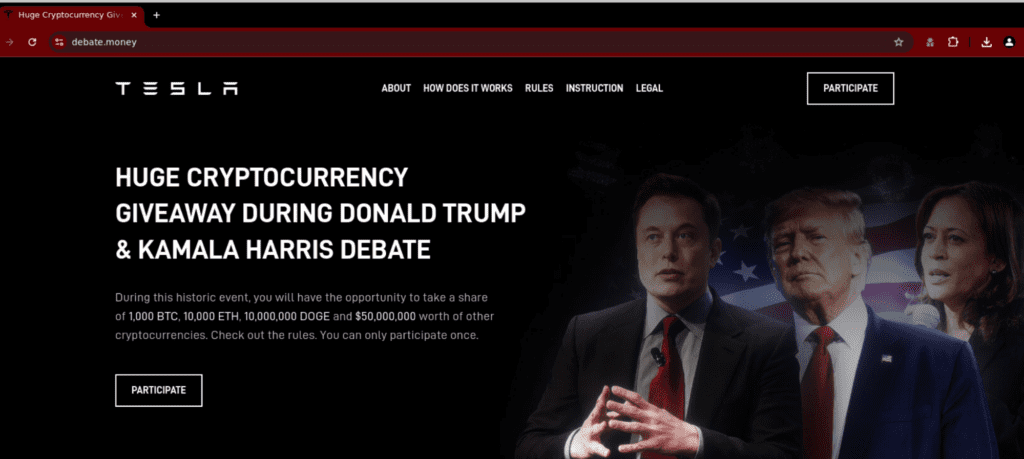
Fig. 5. Above the fold screenshot from the variant 2 website
Variant 2 utilizes content assets like those in variant 1. However, it calls out the US presidential election debate between Donald Trump and Kamala Harris directly in the text (see fig. 5 and fig. 7). It also uses an image featuring Harris, the Democrat presidential nominee.
The page features Elon Musk’s Tesla logo instead of Trump’s campaign logo, demonstrating how criminals tailor their content to appeal to different audiences, i.e., politically engaged vs cryptocurrency minded.
Unlike variant 1 (and variant 3), variant 2 includes an extra “What’s Happening” section, providing context on the cryptocurrency “giveaway” (see fig. 6).
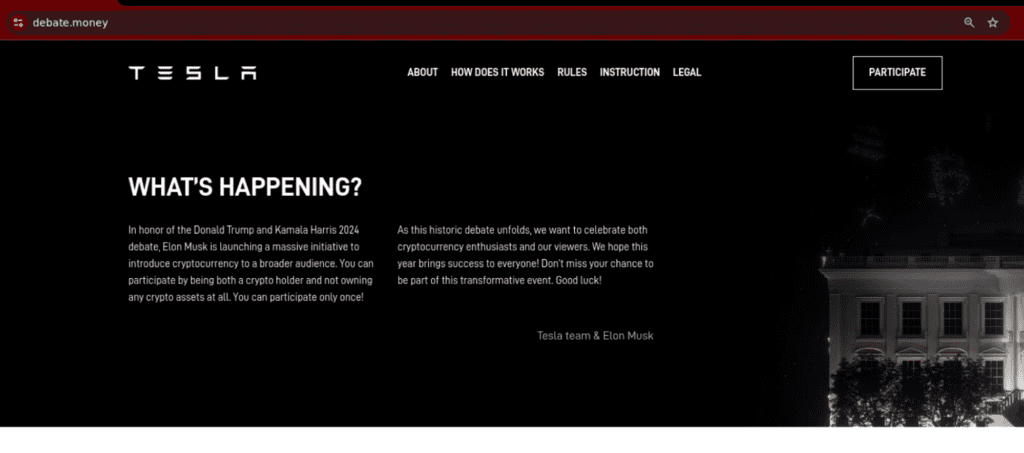
Fig. 6.
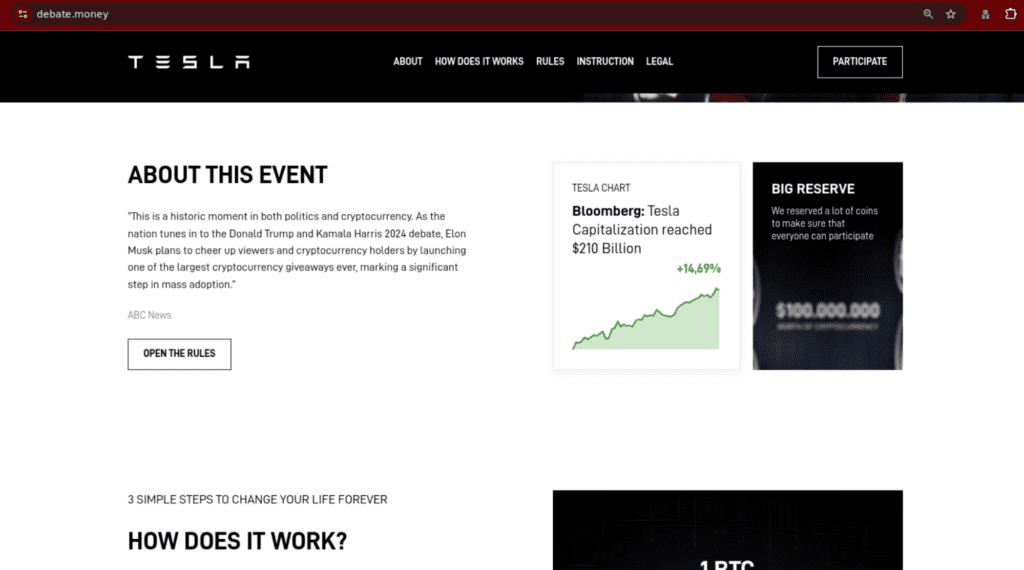
Fig. 7 (Fig. 6 – 7. Below the fold screenshots from the variant 2 website)
Variant 3: “Biggest Crypto Giveaway”
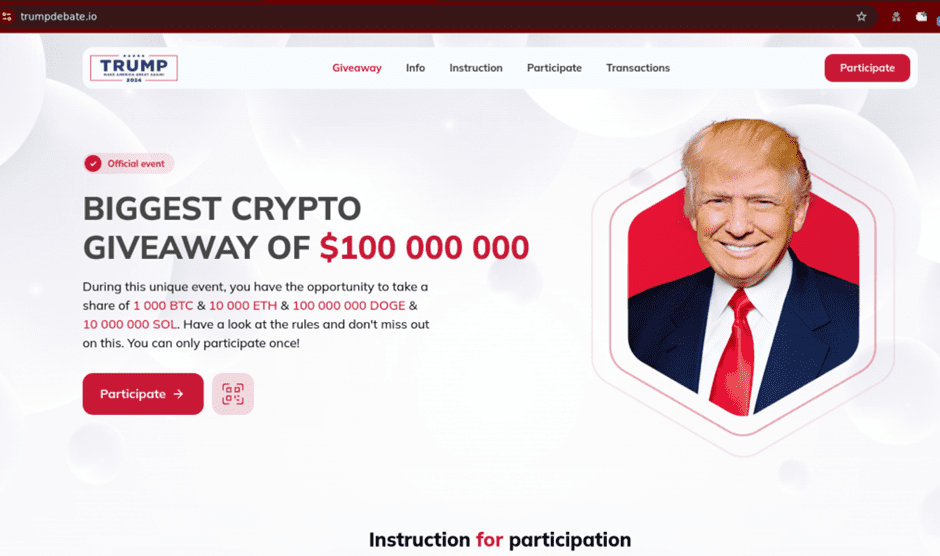
Fig. 8.
Variant 3 appears to hot swap personas while retaining the same core content, i.e., a new persona is used, while the other webpage assets remain the same. Netcraft has identified many examples using this approach, which is distinguished by its use of the distinctive hexagonal image frame and stock copy. The only variances in these examples are the target personas (different headshots) and in some cases the page colour and/or appearance (see fig. 10).
In variants both 1 and 2, we observe extra, custom assets (logos, text, diagrams, etc.) being used to provide a theme to the web content. No such efforts are made with variant 3, which utilizes the same assets across the board.
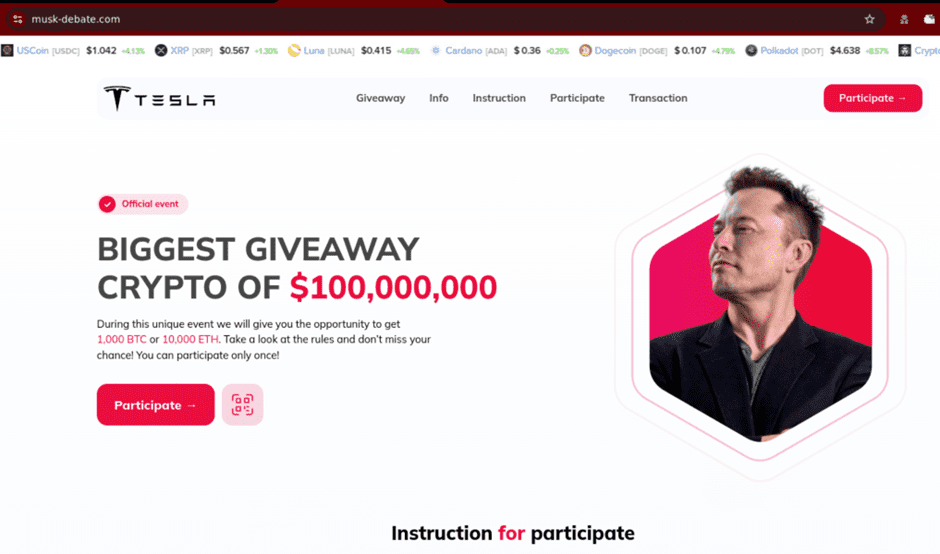
Fig. 9. (Fig. 8 – 9. Above the fold screenshots from the variant 3 website)
The characteristics of variant 3 are particularly interesting in the context of resource expenditure on the criminals’ behalf. By removing the need for custom text, and by using short, generic copy, threat actors alleviate any need to review their content or adapt it for different scenarios. To summarize, variant 3 demonstrates the speed and efficiency with which threat actors make use of ready-made, easily customizable assets to improve the efficiency of their campaigns, potentially increasing their gains.
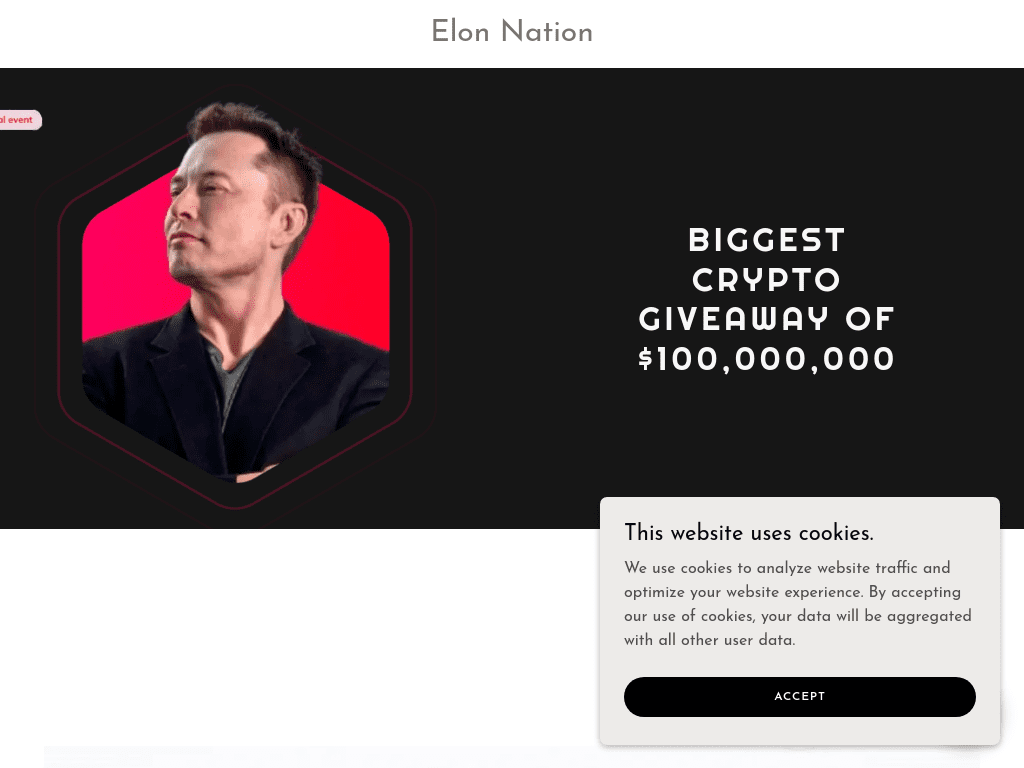
Fig. 10. Screenshot demonstrating subtle changes to the variant 3 template.
Characteristics of variant 3
Netcraft logged the following common characteristics from variant 3 in this crypto-doubling scam.
Website headers
The scam uses the same header, which consists of a logo, navigation links to page sections, and a “Participate” call to action (CTA) which links to a page containing wallet addresses for the transaction.


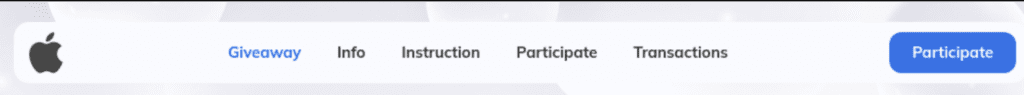

Fig. 11. Screenshots of the different headers used in the variant 3 template
Page sections
Above the fold
Above the fold, the variant 3 template focuses on grabbing attention with bold H1 text (“BIGGEST GIVEAWAY CRYPTO OF $100,000,000”). It also uses:
- A seal icon with a tick and the text “official event”
- Text paragraph explaining the giveaway, including the different acceptable currencies
- The standard “Participate” CTA
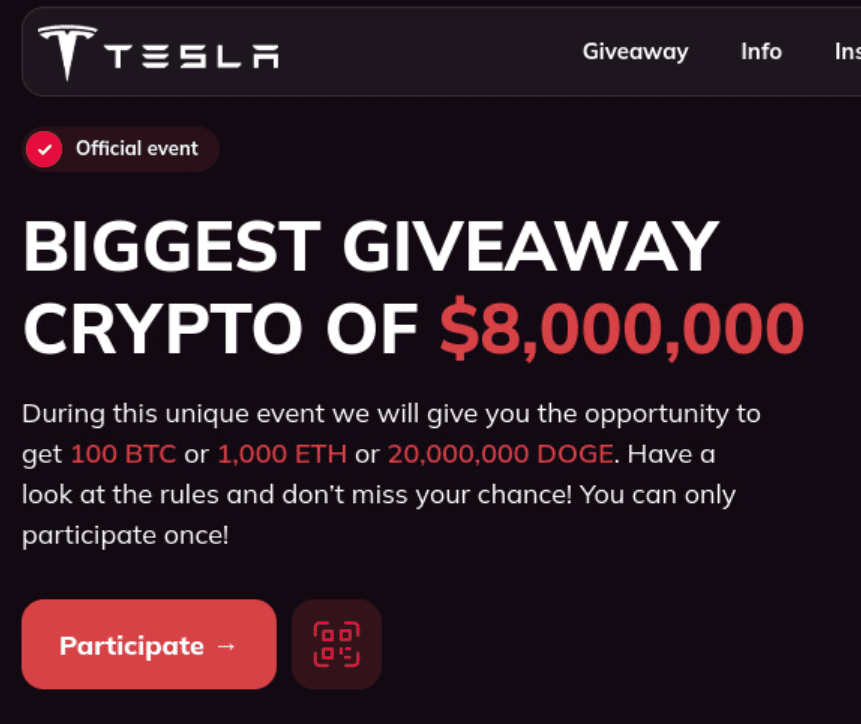

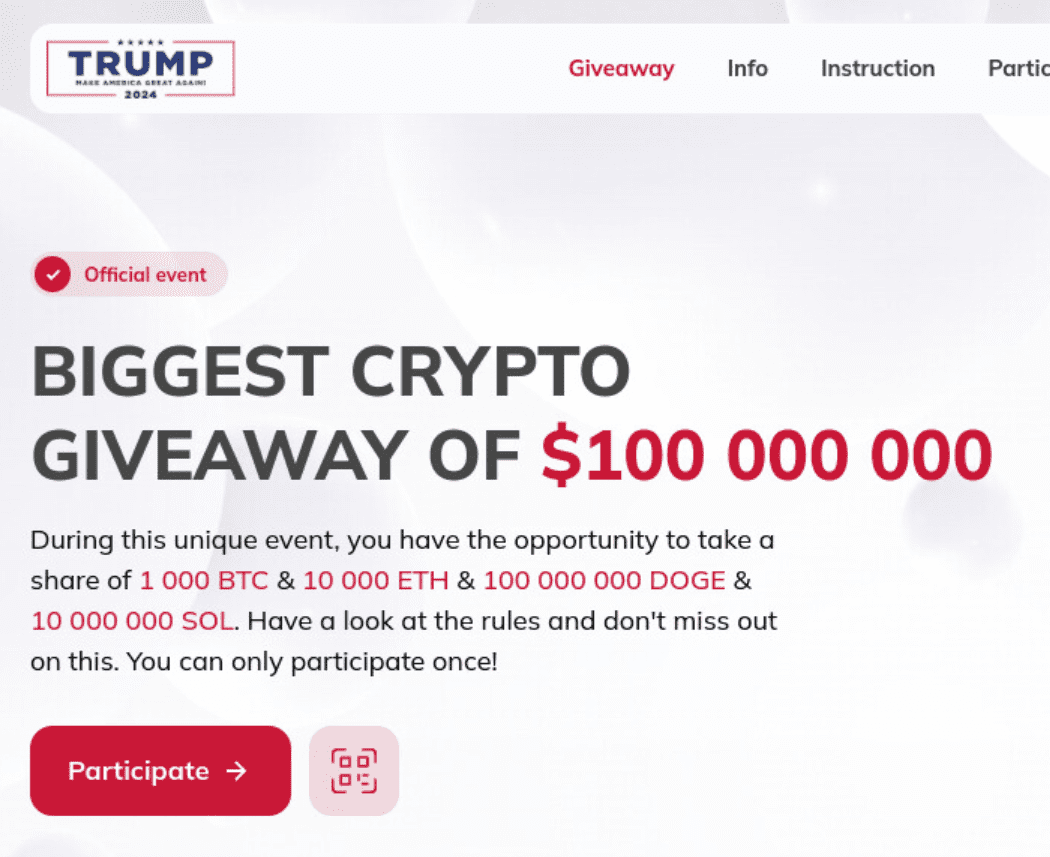

Fig. 12. Screenshots of the different above the fold variations
Instructions and information
Directly below the fold, the variant 3 template includes two sections:
- “Instruction for participation”: a step-by-step diagram purporting to show the crypto investment process (note the grammatical error in “Instruction”).
- “Rules & Information”: two text blocks explaining (left) why the giveaway is happening and (right) the accepted cryptocurrencies and minimum payment amount.
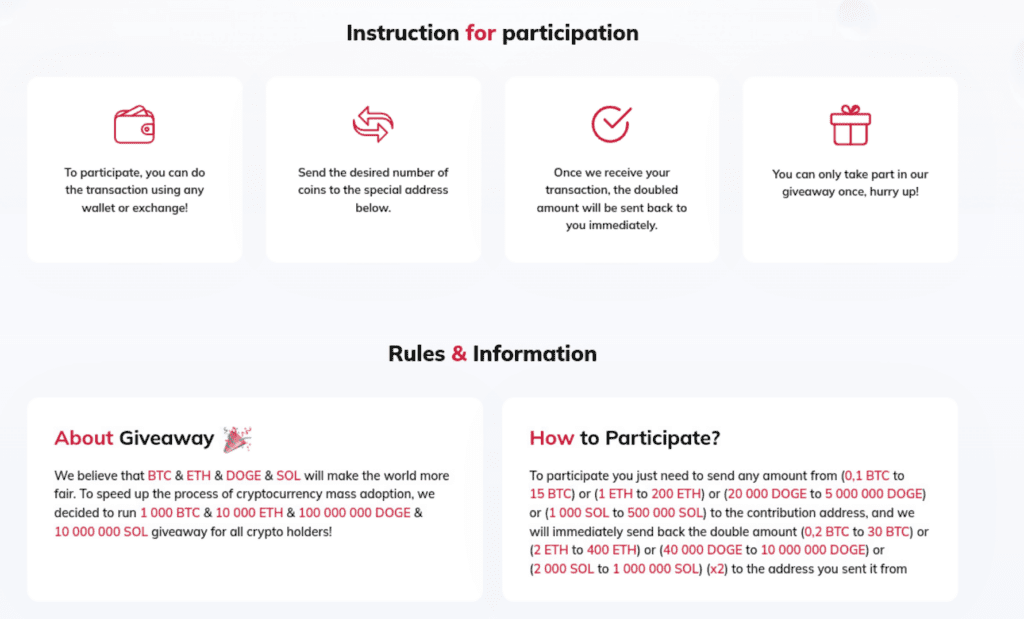
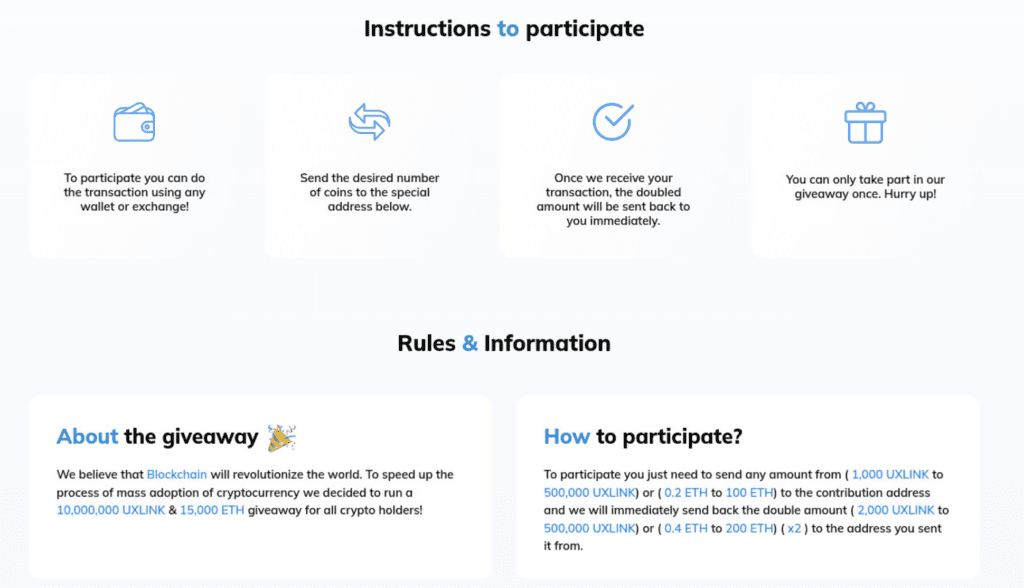
Fig. 13. Side-by-side comparison of the lower page sections from two of the phishing websites
In some examples (fig. 14), a calculator is embedded into the page to illustrate the amount the victim will allegedly receive in return for their investment.
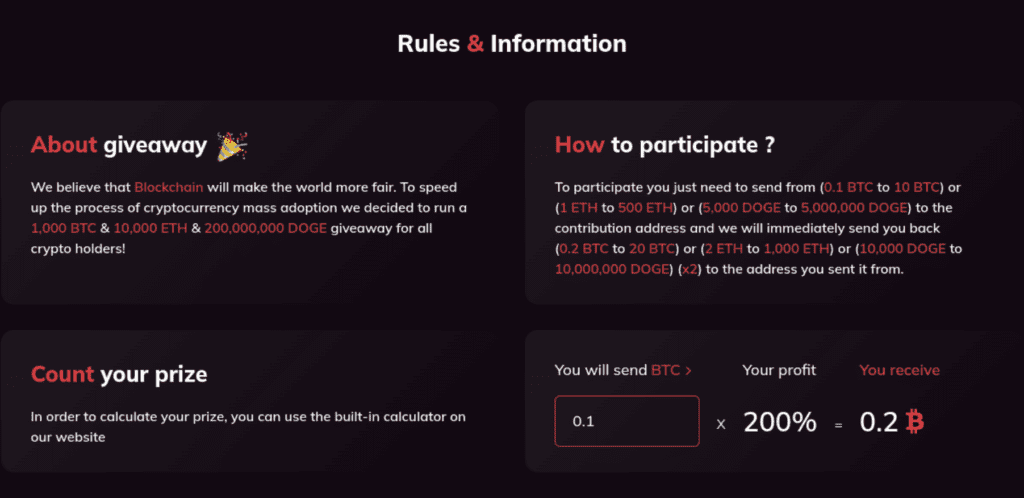
Fig. 14. Screenshot showing variant 3 example with investment calculator
How are these scams being distributed?
Netcraft has observed these scams being distributed via YouTube featured in videos in which Elon Musk discusses the US presidential election debate (see fig. 15). The YouTube channels used include purpose-registered examples and others which have been compromised. Other external analyses report distribution via X, Facebook, Instagram, and Telegram.
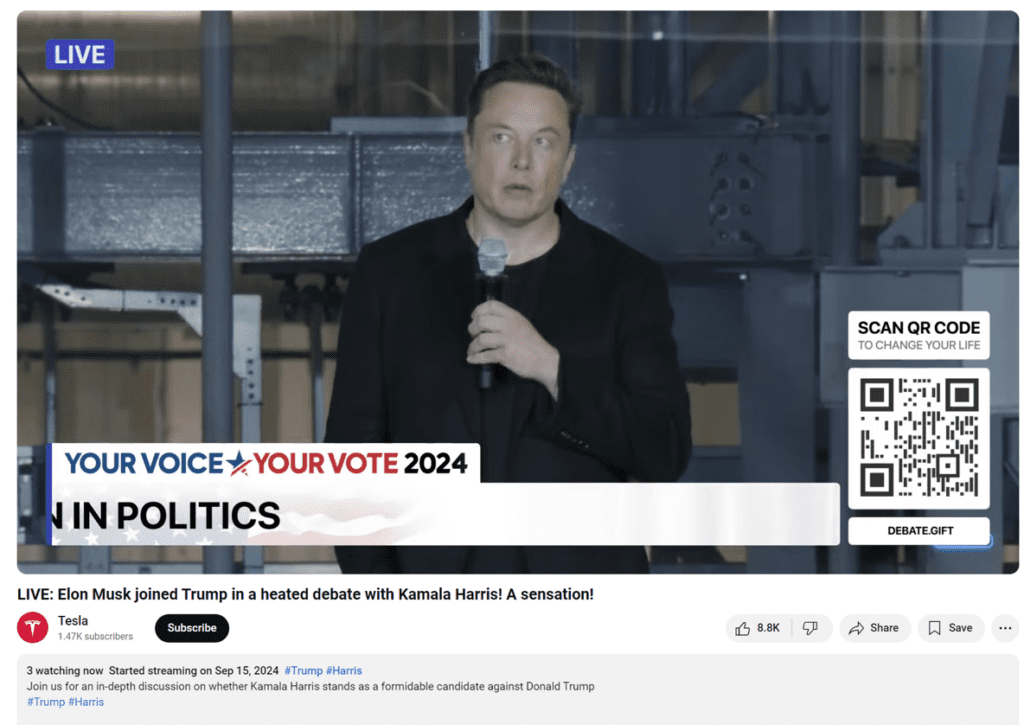
Fig. 15. Screenshot from a fake YouTube video featuring Elon Musk
How to protect your brand
The volume of these crypto-doubling scams, the variations identified, and the different tactics used indicate the scale at which threat actors can target would-be cryptocurrency investors.
For the brands and personas imitated, this type of scam erodes trust and credibility and may lead to a backlash from victims, as well as surplus legal and customer service costs. The time it takes to recoup these losses can have far-reaching consequences.
Identifying and removing the digital content used to target victims through these campaigns requires speed, accuracy, and scale. Netcraft offers all three. Our Brand Protection services make use of the industry’s largest and most powerful dataset to continuously search the internet for any misuse of your brand name and likeness. Our website takedown times are the fastest and most reliable in the brand protection space, reducing the number of scams attempting to exploit your brand, IP, and customers.
To find out what ROI Netcraft can offer your organization, and to see our solutions in action, book a demo now.