WikiLeaks experienced some website downtime last night, coinciding with its release of the US embassy cables at cablegate.wikileaks.org.
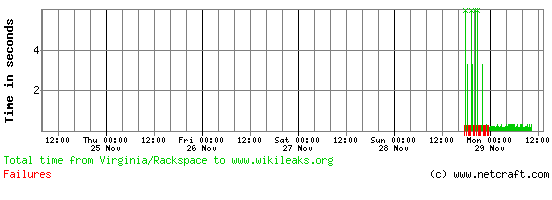
Just before the latest leak was released to the world via their new “cablegate” site last night, WikiLeaks tweeted that they were under a mass distributed denial of service attack, but defiantly stated that “El Pais, Le Monde, Speigel, Guardian & NYT will publish many US embassy cables tonight, even if WikiLeaks goes down”.
Twitter user th3j35t3r claimed to be carrying out the denial of service attack against www.wikileaks.org, although in a tweet that has since been deleted, th3j35t3r stated that it was not a distributed attack. If WikiLeaks believed the attack to be distributed, it could suggest that other parties had also been carrying out separate attacks at the same time.
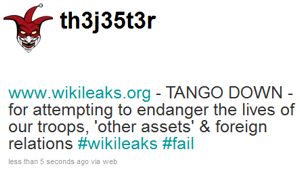
th3j35t3r’s Twitter profile lists his location as “Everywhere” and he describes himself as a “Hacktivist for good. Obstructing the lines of communication for terrorists, sympathizers, fixers, facilitators, oppressive regimes and other general bad guys.“.
th3j35t3r’s Twitter feed lists dozens of other sites that have also been taken down, mainly communicated through “TANGO DOWN” messages posted via the XerCeS Attack Platform. The “tango down” phrase is used by special forces and is often heard in FPS games such as Rainbow 6 and Call of Duty, where it is used to describe a terrorist being eliminated.
Referring to the success of the attack, th3j35t3r also tweeted, “If I was a wikileaks ‘source’ right now I’d be getting a little twitchy, if they cant protect their own site, how can they protect a src? “
The main www.wikileaks.org site appeared to bear the brunt of the attack, suffering patchy or slow availability for several hours. Last night, the site was hosted from a single IP address, but has since been configured to distribute its traffic between two Amazon EC2 IP addresses on a round-robin basis. One of these instances is hosted in the US, while the other is in Ireland.
Meanwhile, cablegate.wikileaks.org has so far escaped any significant downtime. This site has used 3 IP addresses since its launch, probably in anticipation of being attacked or deluged with legitimate traffic. Two of these IP addresses are at Octopuce in France, which also hosts the single IP address now used by warlogs.wikileaks.org. Ironically, the third IP address being used to distribute secret US embassy cables is an Amazon EC2 instance hosted in – you guessed it – the US.
Performance graphs are available here: