Despite the inconsistent treatment of certificate revocation by browsers, providing reliable revocation information is an integral part of operating a trustworthy certificate authority (CA) and a well-accepted requirement of Mozilla’s CA root program. However, there are presently thousands of certificates in use which are irrevocable in some major browsers, and hundreds in those browsers which do everything right.
Without the ability to revoke a certificate, a CA has no control over whether a certificate is accepted by browsers or relied upon for secure communication after its issuance and before its expiry. A compromised private key and certificate in the hands of an attacker could be devastating: he would be able to use the private key to decrypt some intercepted SSL-secured traffic and the certificate to impersonate the targeted site. Even if the CA becomes aware of the problem, they can do nothing about it directly without having to rely on the browser vendor’s support. CAs use two main technologies for browsers to check whether a particular certificate has been revoked: using the Online Certificate Status Protocol (OCSP) or looking up the certificate in a Certificate Revocation List (CRL). OCSP provides revocation information about an individual certificate from an issuing CA, whereas CRLs provide a list of revoked certificates and may be received by clients less frequently.
Assessing browser support for the two forms of revocation is complicated by Google Chrome’s varying behaviour, depending on the platform, browser settings, and its use of pre-aggregated crlsets which contain revocation information for a limited selection of certificate authorities. Firefox does not automatically download CRLs for non-EV certificates so, by default, must rely on OCSP alone. Both Internet Explorer and Opera are more secure in this context: they support OCSP and CRLs and make suitable checks for all types of certificate. Safari does not make revocation checks at all by default for non-EV certificates and the mobile version does not provide the option to do so. For most Safari users, whether or not a certificate is irrevocable is immaterial — Safari does not check for revocation by default.
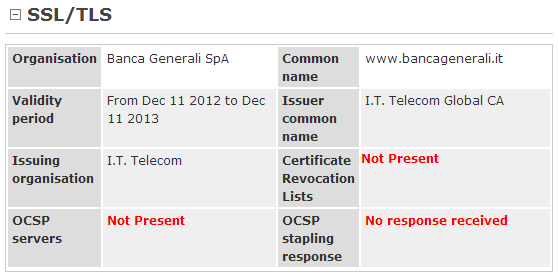
Excerpt from Netcraft’s site report for https://www.bancagenerali.it showing the lack of any revocation method available.
Netcraft has found hundreds of certificates trusted by major browsers which are effectively irrevocable; that is they do not contain valid entries in the crlDistributionPoints X509 extension or OCSP URLs in the AuthorityInformationAccess extension. There may be appropriate CRLs or OCSP responders available, but there is no standard automated means to discover them. Without these two extensions, there is some chance a browser will use a cached CRL (downloaded after visiting another site using the same intermediate certificate) and have access to revocation information not otherwise available. It is easy, however, to envision many scenarios where this fortunate event hasn’t occurred before a person visits a site with a revoked certificate.
The CA/B forum — an organisation of both CAs and browsers — publishes a set of Baseline Requirements (BR), which allow a CA to rely on OCSP stapling for “high-traffic” FQDNs and omit OCSP URLs from the certificate. However, currently there is not a widely supported method for enforcing the use of OCSP stapling. The draft TLS Security Policy extension can contain a must-staple directive, which, if present, will indicate to clients to reject any connection without a stapled OCSP response.
In Netcraft’s May 2013 SSL survey, more than 300,000 certificates did not contain an OCSP responder URL and are thus irrevocable in Firefox (except for a handful of hard-coded OCSP responder URLs); of these, almost 9,000 were issued this year. Around 800 did not contain URLs for either revocation method, making them effectively irrevocable.
The table below shows some example certificates which are missing some or all of the URLs pointing to revocation methods.
| Example certificate | Site rank | Certificate Authority | OCSP servers | Certificate Revocation Lists | OCSP Stapling enabled | Self-declared BR compliance according to responses to Mozilla |
|---|---|---|---|---|---|---|
| fsgateway.aexp.com | American Express (Verizon Business) | No | No | No | Not yet compliant | |
| www.bancagenerali.it | 28,225 | I.T. Telecom (Verizon Business) | No | No | No | Not yet compliant |
| *.malaga.es | FNMT | No | No | No | N/A | |
| accounts.google.com | 7 | Google Internet Authority (Symantec) | No | Yes | No | Compliant |
| login.skype.com | 1,804 | Microsoft (Verizon Business) | No | Yes | No | Not yet compliant |
| query.rapidssl.com | 1,280,616 | Symantec | No | Yes | No | Compliant |
| www.faa.gov | 498,030 | Verizon Business | No | Yes | No | Not yet compliant |
| www.creditmutuel.de | KEYNECTIS | No | Yes | No | Compliant | |
| *.mygrants.gov.my | AlphaSSL (GlobalSign) | No | Yes | No | Partially compliant |
There are a number of certificate authorities which have issued such certificates, including the following:
- An American Express certificate, issued by their own certificate authority, does not contain URLs for either revocation method nor does it staple an OCSP response, making it totally irrevocable. American Express’s certificate authority eventually chains up to GTE CyberTrust (now Verizon Business). This certificate was issued before the effective date of the CA/B forum’s Baseline Requirements.
- Google Internet Authority, a subordinate CA of Equifax (now Symantec), does not include OCSP responder URLs in any of its certificates making the certificates effectively irrevocable in Firefox except by action by the browser vendor. Even if Google were to use OCSP stapling (which it does not appear to do — at least on some popular sites) people using Firefox would be no better off as support by default is still in the pipeline. The lack of OCSP URLs may be a conscious decision by Google to reduce the performance penalty of using SSL. The risk posed by not performing this check is not theoretical as one of Google’s CRLs contains 7 serial numbers for certificates which were revoked for ‘Key Compromise’, an event which can’t be dealt with directly by Google for users of Firefox.
- A number of other certificate authorities have issued certificates without OCSP responder URLs this year, including Symantec, Verizon Business, GlobalSign, Microsoft, and KEYNECTIS. The original Baseline Requirements document — effective from 1 July 2012 — stated that there MUST be at least one OCSP URL in the AuthorityInformationAccess extension.
- Several recently-issued irrevocable certificates violate other Baseline Requirements. For example many certificates also have RSA keys shorter than 2048-bits expiring beyond the end of this year — the CA will not be able to revoke them effectively on 1st January 2014 as is required. I.T. Telecom (which is a subordinate CA of Verizon Business) and FMNT (the Spanish Royal Mint) are the worst offenders, having issued totally irrevocable certificates with short public keys. Some major CAs have also signed certificates with short public keys and only CRL revocation available including Symantec and Verizon Business.
None of the example certificates mentioned above responded with a valid OCSP response stapled, so the limited exception allowed in the Baseline Requirements for high-traffic FQDNs isn’t applicable.
Whilst the majority of certificates issued by major CAs are revocable in line with the Baseline Requirements, browser vendors could consider enforcing the most security-critical requirements in the browser itself, raising the bar for all certificate authorities. Browser vendors are somewhat limited in the available methods to sanction or remove their trust in widely used CAs: straightforward revocation of intermediates or root certificates runs the risk of disabling a large proportion of secure websites leading users to question not the CAs, but the browser software and the web site they are visiting.
23/05/2013: Edited to correct attribution of Microsoft’s CA to Verizon Business.