
Blog
Governments Introduce Coronavirus-specific Cybercrime Legislation
Governments and organisations globally have been making announcements that just a few weeks prior would have been unprecedented. As more of our lives are moving online in an attempt to adapt to changes brought about by the Coronavirus pandemic, many are trying out services they were previously unfamiliar with, such as video conferencing or online grocery shopping. While others are finding themselves with more time to pursue online hobbies such as gaming.
The combined effect of information overload and a mass of people using unfamiliar software and services has created an environment ripe for exploitation by cybercriminals.
Netcraft has tracked Coronavirus-themed cybercrime since 16th March, shortly after it was declared a pandemic by the World Health Organisation. While Netcraft continues to see high volumes of Coronavirus-inspired fake shops, advance fee fraud, phishing and malware lures, this post covers some of the trends Netcraft has observed since our previous posts on the topic.
Recently observed Coronavirus-themed threats
Fake Government information sites and mobile malware
Many governments have set up dedicated websites offering advice and services to support their citizens through the pandemic. Cybercriminals are taking advantage of this by providing copy-cat sites with a malicious twist.
In one recent campaign, the cybercriminals deployed a site that poses as the UK Government and offers “credit card refunds” for “COVID-19 support”. The fraudulent site uses UK Government branding and collects the victim’s personal information – including their credit card number, date of birth and telephone number.
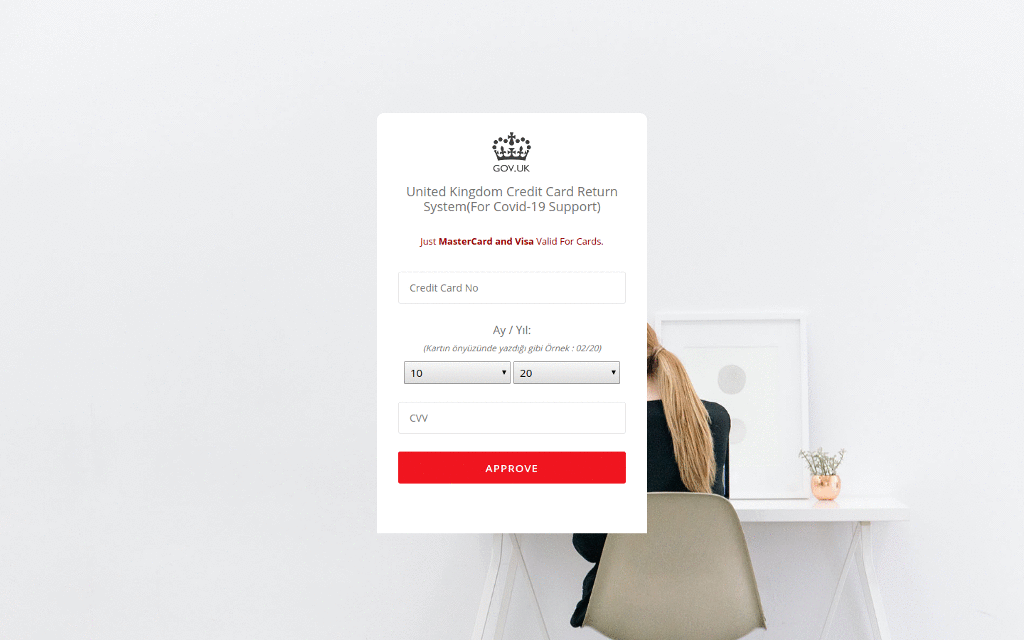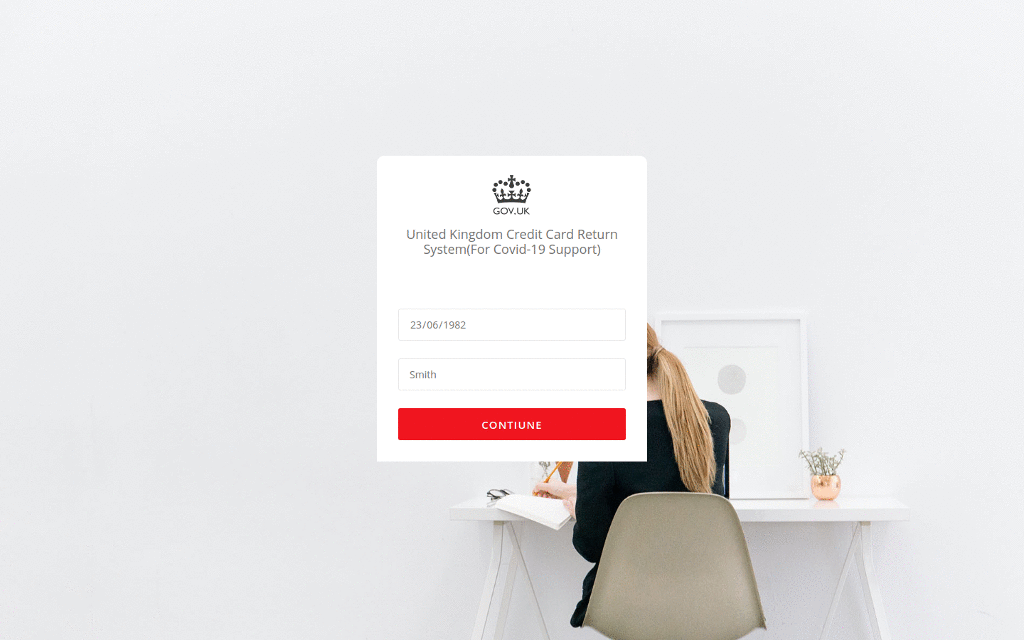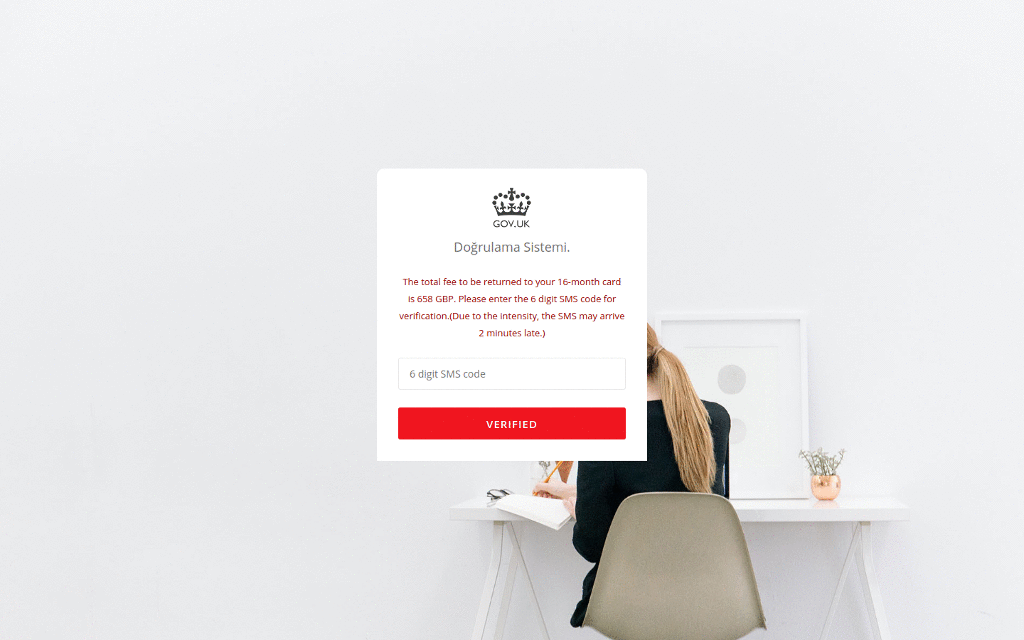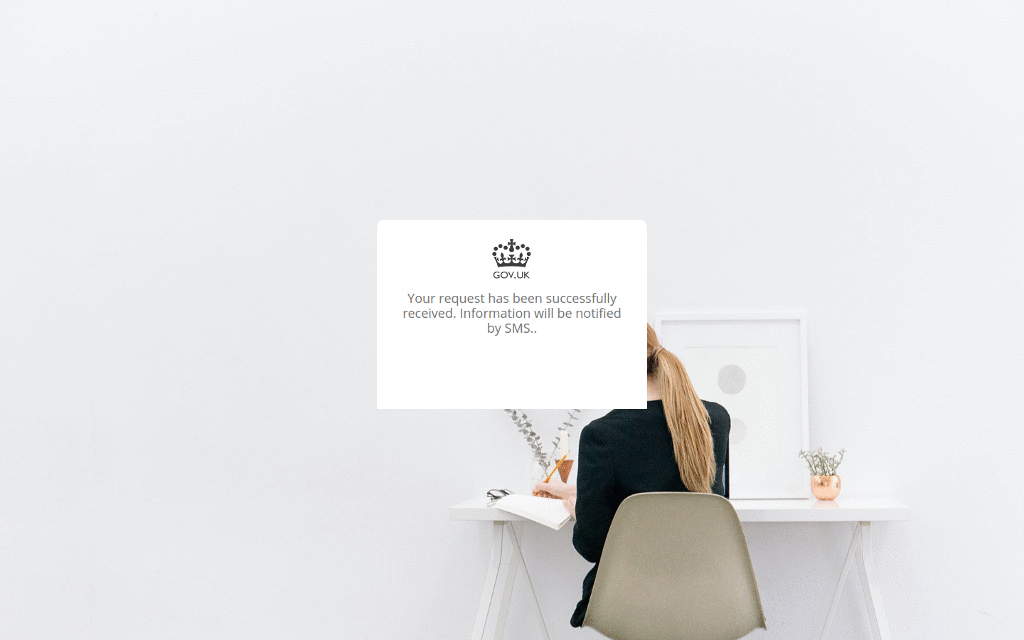
In another case, cybercriminals set up a fake site which looked identical to the Australian Government’s. But rather than providing the government’s latest Coronavirus advice, it included a link to an Android application which claimed to provide information on how to get tested. In reality, the mobile application deployed Cerberus, a popular Android banking trojan, which ...
Learn More

Blog
Netcraft Adds Coronavirus-related Cybercrime Protection to its Apps and Browser Extensions
Netcraft has added protection from Coronavirus-related cybercrime to its mobile apps for Android and iOS, and to its browser extensions for Chrome, Firefox, Opera, and Microsoft Edge.
Learn More

Blog
April 2020 Web Server Survey
In the April 2020 survey we received responses from 1,246,121,153 sites across 260,089,947 unique domains and 9,669,267 web-facing computers. This reflects a gain of 10,000 computers and 2.90 million domains, but a loss of 16.9 million sites.
nginx and Microsoft lost the most sites this month — 13.4 million and 10.4 million each — but like all other major vendors, they both gained domains.
Since attaining the largest share of domains last month, nginx has extended its lead with net growth of 1.84 million domains and now has a 28.5% share of this market, compared with Apache’s 27.8%.
Although Apache gained the largest number of sites this month — more than 2 million — it lost 598,000 active sites and its presence amongst the top million websites decreased by 4,230 sites, which took its top-sites count down by 1.43%. Nonetheless, Apache still has the largest share of the top million sites for now (29.1% compared with nginx’s 25.5%), and also continues to lead in terms of active sites and web-facing computers.
Vendors respond to COVID-19
As the coronavirus pandemic continues to affect many people’s lives in an unprecedented fashion, some web server vendors have offered to help in a variety of direct and indirect ways.
Microsoft has made an initial $1 billion donation to Puget Sound’s COVID-19 Response Fund; published a map that tracks active, recovered and fatal cases; and has offered its Healthcare Bot service powered by Microsoft Azure to help frontline organisations screen patients for potential infection and care.
NGINX and F5 are offering free resources for websites impacted by the crisis. This includes free access to its core training for NGINX Open Source; providing additional help and one free year of NGINX Plus to the education, public government and non-profit sectors; and encouraging its employees to respond ...
Learn More

Blog
Coronavirus Cybercrime Scaling Up
Just like Coronavirus itself, the Coronavirus-themed cybercrime it has spawned is quickly becoming a pandemic of its own. Cybercriminals have been quick to take advantage of the media attention on the story, using lures with a Coronavirus theme. Many of the attacks Netcraft has observed have used the fear and uncertainty surrounding the situation to trigger a response from their victims.
Netcraft has tracked Coronavirus-themed cybercrime since 16th March, shortly after it was declared a pandemic by the WHO. This post covers some of the trends Netcraft has observed since our previous post on the topic.
Coronavirus certificates
Analysis of certificate transparency logs for new certificates covering hostnames containing keywords “COVID” and “Coronavirus” shows increasing numbers of certificates are being issued for Coronavirus-themed hostnames.
Whilst some of the certificates included in the graph will be being used for legitimate purposes, many certificates – particularly those which have been registered since the outbreak started – are being used to spread disinformation, host fake shops and pharmacies, serve phishing websites and to disseminate malware.
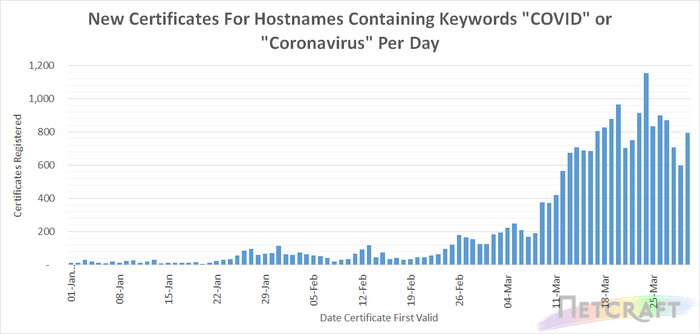
Numerous governmental, research and healthcare organisations are making use of organisation and EV certificates to provide higher levels of assurance to visitors to their website. Organisation and EV certificates (excluding Cloudflare organisation validation certificates which validate Cloudflare, not the website owner, as the organisation responsible for the certificate) account for 10.5% of certificates included in the chart above.
The more recent plateau in certificate issuance for Coronavirus related hostnames may in part be due to registrars, such as Godaddy and Namecheap, restricting the registration of these domains in response to the New York Attorney General’s request on March 20th. Richard Kirkendall, Namecheap CEO wrote to customers on March 25th stating:
...we are actively working with authorities to both proactively prevent, and take down, any fraudulent or abusive domains
Learn More

Blog
Coronavirus Cybercrime
Netcraft has tracked Coronavirus-themed cybercrime since 16th March, shortly after it was declared a pandemic by the WHO. Scammers have been quick to take advantage of the massive worldwide attention to Coronavirus (COVID-19), and are increasingly making use of it as a theme for online fraud.
Netcraft is the largest provider of anti-phishing takedowns in the world and provides countermeasures against some 75 other types of cybercrime for governments, internet infrastructure and many of the world’s largest banks and enterprises. Coronavirus-themed cybercrime accounts for around 5% of all the attacks we perform countermeasures against, even without accounting for attacks that may otherwise be attributed to existing phishing targets.
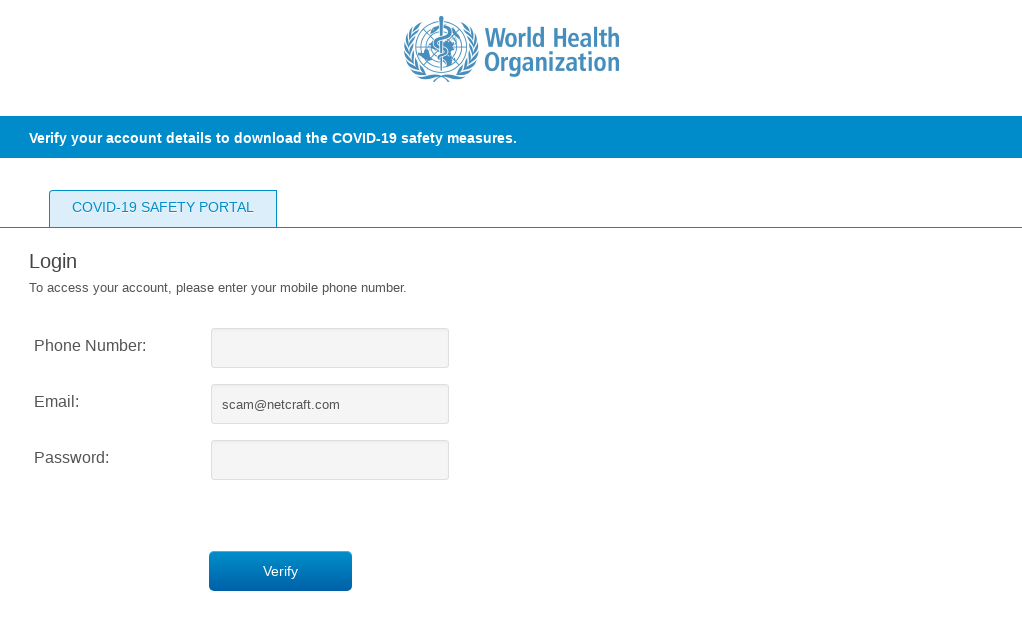
Coronavirus Phishing attack impersonating the World Health Organisation
Coronavirus Themed Attacks
Advance Fee Frauds
Advance fee frauds typically involve promising the victim a large amount of money, with only a relatively small up-front fee required (for example, to cover processing). These attacks have required only very small changes to adapt to Coronavirus. Examples include:
...
I am currently receiving treatment for the COVID-19 in Huoshenshan Hospital, Wuhan, China. I am 68 years old and I have been told that I will not survive this virus. I need you to help claim and distribute my funds (us$7.5M.) to support people with the COVID-19…
My Name is Andrew Contarini from Venice Italy. I was diagnosed with Leukemia which has defied all forms of medical treatment, and last week miraculously survived Coronavirus infection… I intend and willing to empower the change of ownership for the transfer of my wealth to your possession for further Investment and Charity Disbursement to the Less Privileged and Homeless…
The COVID-19 Cash Donations policy is a 30-day free coverage that provides you to help people in your community, for hospital confinement and a benefit lump sum payout ($2,000,000.00) for you .