Netcraft guide to detecting and disrupting fake apps
Mobile apps are a big deal —for consumers, brands, and developers alike. Consumers spend an estimated 5 hours per day using mobile apps in 2023, across various categories, from social media and entertainment to business, productivity, and banking.
The two most prominent platforms, Apple iOS and Google Android, account for the vast majority of the market. In 2023, Apple reported annual revenue across apps available in the App Store of more than $1.1 trillion. Google Play has many third-party apps with over a billion installs on Android devices.
Like desktop applications, there are serious cyber threats that impact mobile apps. Both iOS and Android can and do contain malware, and there are hundreds of third-party app stores that offer potentially unauthorized, often modified, copies of legitimate apps. For organizations whose apps are targeted, the damage to their reputation through the fraudulent use of their app, logos, and branding can be significant.
It’s more important than ever that consumers can trust the apps they rely on and that brand owners are confident that their organization’s apps and brand aren’t exploited and impersonated by cyber-criminals.
In this guide, we’ll:
Examine the threat that fake apps pose for both brand owners and consumers
Analyze some high-profile case studies to illustrate how fake apps are used to carry out cyber-attacks
Illustrate how Netcraft’s digital risk protection platform detects, blocks, and takes down fake apps and the mechanisms used to promote them, such as phishing and fake ads
What are fake apps?
A mobile application, or app, is a program that users can install on their device. Often associated with a well-known organization, apps can offer a wile range of functionality covering banking, social media, investing, news, gaming, and more.
Both IOS and Android offer the ability to install apps, with Apple devices limited to the official App Store and from the 7th of March some third-party app stores and Android offering both an official Google Play Store and the ability to use third-party stores or sideload applications directly from the internet.
Fake apps, found in both official and third-party Android and iOS stores, are unauthorized copies created by cyber-criminals, which mimic the logo, branding, and functionality of legitimate applications (like the fake banking app shown in the figure below), often with nefarious intentions, such as credential stealing, theft, or system access.
When apps are installed, users can grant permission for them to access other information on the device. While legitimate organizations will have technologies and processes to look after this information, cyber-criminals have no such obligation or intent. This means once a fake app has been installed, it may have access to sensitive data if the user grants permission under the mistaken assumption that a legitimate organization operates it.
In addition to accessing sensitive information acquired “with permission” under false pretenses, fake apps can also install malware onto the device, designed to exfiltrate data, damage the device, or overlay fake pages over real applications to steal sensitive data.
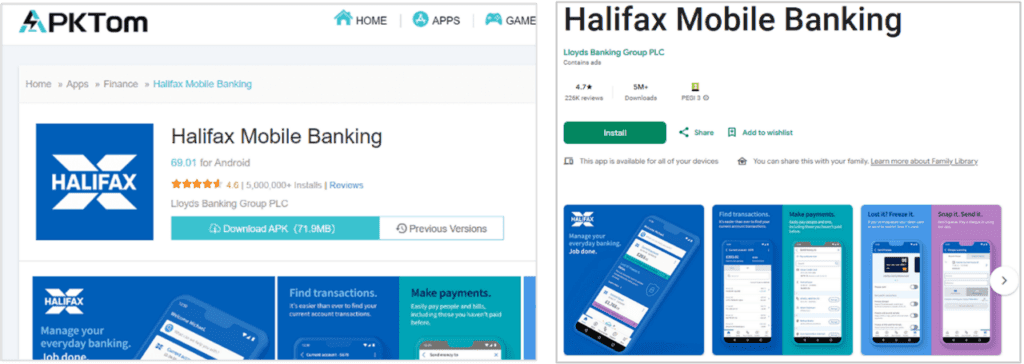
Figure 1 A fake banking app (left) available to download on a third-party app store, and the genuine app available on the Google Play store.
How are fake apps distributed?
Most mobile users download apps from the official Apple App Store and the Google Play Store.
Non-Google-manufactured Android devices often come with an app store operated by the original equipment manufacturer (OEM) pre-installed, such as the Samsung Galaxy Store for Samsung Galaxy devices or the Huawei AppGallery.
Uploading an app to either Google Play Store or the Apple App Store requires submitting it for vetting, so operators can check they are safe to use. This “walled garden” approach means that users can expect a safe experience with apps available in official stores.
Nevertheless, despite these vetting processes, malware continues to make it into stores. In 2020, Google reported that the Joker malware had infected many apps in its official Play store, while the XcodeGhost malware infected apps available from iOS App Store, which could have affected the 100 million users who downloaded compromised apps.
Third-party app stores
Today, the Android platform allows for third-party app stores, and iOS will soon follow in a more limited way in response to recent EU regulations. These are app stores that users must download or access separately, typically characterized by their focus on freedom (as opposed to the safety and privacy of users). While there are fewer people using third-party app stores in comparison to the official app stores, a lack of robust vetting processes means that users who download apps from third-party app stores are more likely to be downloading fraudulent and malicious apps.
Hundreds of third-party app stores claim to offer copies of legitimate Android apps; searching the web for the app’s name demonstrates the sheer number of unauthorized app stores. These copies can be benign (but still are unauthorized by the brand owners) or genuinely dangerous and may include malware or other unwanted software that the user unwittingly installs on their phone.
Even if unmodified, applications available on third-party stores can offer versions with known security vulnerabilities or offer retired functionality.
Doctored apps can also be modified to insert adware which flood the unsuspecting user with hundreds of pop-up ads – many of which will be fake – to gain access to lucrative advertising revenue.
Experiences such as these result in damage and deterioration of trust and brand reputation to legitimate brand owners. No brand owner wants their product available in uncontrolled app stores, potentially tainted with adware, malware or other unwanted behavior.
Case study: the FluBot banking trojan
One of the most notorious Android viruses in recent years, FluBot, was able to spread around the world as Android users believed they were installing legitimate versions of popular apps, including parcel-tracking apps and a variety of banking apps (including Great Southern Bank, Suncorp and Ubank).

Figure 2 Fake versions of legitimate banking apps, sent by cyber-criminals to victim’s phones and designed to collect their login and password details
The victims were tricked into unwittingly installing malware that overlayed fake login forms on top of real applications to steal user details. This deception was initiated by sending users “missed parcel” phishing messages, usually by SMS, which contained links to malicious websites that encourage victims to install the fake app.

Figure 3 Examples of scam websites and messages, which contain links to fake apps that contain the FluBot malware.
The FluBot malware accessed the user’s contact list on infected devices and sent scam SMS messages to these numbers as well, thus helping the malware to spread across the world.
Rogue apps: a growing menace
The threat from fake apps is real and growing, so much so that the UK government is in the process of introducing a ‘Code of Practice for App Store Operators and App developers’1 that aims to protect consumers (and, by extension, the brands that downloaded rogue apps are impersonating) from cyber-criminals and malicious apps.
As the code of practice makes clear, most consumers:
• Have no way of knowing whether an app is secure
• Will not understand how their data is handled
• Implicitly trust apps that they believe they are downloading from established organizations
For all these reasons, rogue apps are an ideal ‘attack vector’ for cyber-criminals; not only does the malicious app, once installed on the consumer’s device, provide access to the vast amounts of personal data that it contains, but the consumer may not even be aware that their device is compromised.
Fake app detection and takedown from Netcraft
Netcraft searches official and unofficial third-party app stores to find fake apps that impersonate your organization’s legitimate applications. As previously mentioned, these fake apps may contain malware or be constructed to trick victims into gaining access to personal information, such as banking details, login details, and passwords.
Where app stores offer applications specific to a country, Netcraft will also run country-specific searches based on where you have a presence.
Apps impersonating your company (and unauthorized copies of your own apps in third-party stores) will be reported to the Netcraft takedown service. Netcraft can also search for and take down unauthorized copies of apps that misuse your trademarks, logos, and branding to defend your reputation and to protect your customers from potential malware.
Typically, the third-party app stores will respond positively to Netcraft’s takedown requests to remove applications that have been uploaded without permission.
Netcraft has spent decades at the heart of the internet ecosystem. We capitalize on our long-standing relationships within the infrastructure community to quickly mitigate the harmful impact of cyber-attacks. As a result of our extensive experience in the industry, in many cases, we have a direct reporting process for immediate takedown of these fake applications.
Protecting your customers from the threat of rogue apps
Malicious fake apps (like FluBot) can spread through SMS messages, which usually purport to be from a legitimate organization and contain a link to a ‘lure page’ that attempts to trick victims into downloading and installing the malware. Android and iOS users can protect themselves by using Netcraft’s app, which blocks lure pages (and other malicious sites) that host fake apps. This prevents users from being tricked into downloading and installing fake apps in the first place.

Once blocked, users of the Netcraft apps and extensions are immediately protected. Netcraft also licenses its feeds to browsers and antivirus companies along with internet infrastructure companies, protecting billions of internet users from being exposed to fake apps exploiting your reputation.
The Netcraft difference
Netcraft’s automated brand protection platform operates around the clock to detect cyber threats, including fake apps, phishing attacks, and social media impersonation, as well as more than 100 additional attack types. Detected threats are analyzed using our automated threat intelligence platform, and those targeting customers begin the disruption and takedown process.
We are the world’s largest takedown provider and centrally positioned in the global fight against cybercrime. Our detection, disruption, and takedown solutions are highly automated, powered by the vast amounts of data we collect daily, and backed by the expertise of our in-house team. A unique combination of cutting-edge automation, unmatched scale, and a reputation for excellence and transparency built over decades of work—all powered by a passion to make the digital world a safer place—gives Netcraft’s solution an edge that cannot be replicated.
About Netcraft
Netcraft — the global leader in cybercrime detection and disruption — is a trusted partner for three of the four largest companies in the world, twelve of the fifty biggest banks, and five of the leading governments in the world. Our comprehensive threat feeds, early fraud detection capabilities, and swift automated countermeasures are unparalleled in the industry.
We perform takedowns for nearly one-third of the world’s phishing sites, blocking close to 170 million malicious sites and counting. Many of the largest brands and organizations around the world trust Netcraft. Our customer base includes a diverse mix of industries, sizes, and organizational types, including leading companies within the financial, retail, and technology sectors.
Find out more
Netcraft’s mission is to detect and disrupt cybercrime at scale through constant innovation, extensive automation, and unique insight, delivering a safer online experience for everyone. To find out how Netcraft’s cybercrime detection, disruption, and takedown platform can protect your organization from the threat of fake apps, you can request a demo by visiting https://www.netcraft.com/book-a-demo/ , or find out more by visiting https://www.netcraft.com/platform/.






