
Cybercrime Detection
Defend your organization’s digital presence with Netcraft’s comprehensive cyber attack detection and monitoring

Protecting the world’s leading brands from cyber threats
Netcraft’s automated brand protection platform operates around the clock to detect cyber threats including phishing, advance fee or authorized push payment fraud, executive impersonation, fake shops and 100+ more attack types.
Searches cover a wide range of digital channels including typosquatting or lookalike domains, compromised websites, social media platforms, search engine ads, email and SMS. Processing over five million threat reports each day, Netcraft continuously monitors for occurrences of our customers’ brand names, logos and trademarks online.
Defeating cyber attacks with unmatched scale and effectiveness
Netcraft’s online brand protection operates 24/7 to discover phishing, fraud, scams, and cyber attacks through extensive automation, AI, machine learning, and human insight. Our disruption & takedown service ensures that malicious content is blocked and removed quickly and efficiently—typically within hours.

0%
of the world’s phishing attacks taken down

0M+
threat reports and suspicious URLs analyzed every day

0M
cybercrime attacks blocked to date

0M+
attacks taken down and growing
Sophisticated detection techniques
At the core of Netcraft’s detection capability are highly effective searches across internet-scale datasets derived from Netcraft’s decades of experience mapping the internet.
Netcraft’s global feeds cover cybercrime targeting any institution, including non-customers, and are widely licensed by browsers and antivirus companies. These feeds drive the powerful detection of compromised sites hosting attacks impersonating your brands.
Detected threats are analyzed using our automated threat intelligence platform and those targeting customers begin the disruption & takedown process.
Technology, expertise, and unparalleled speed and accuracy
Building on more than 25 years of experience surveying the internet, we detect cyber attacks by conducting the following searches
DNS Searches
Netcraft monitors for lookalike domains which are deceptively similar to your legitimate websites that lend credibility to a cyber attack, and also probes for potential domains at common TLDs and registrable points (such as .com, .net, .free.fr).
Netcraft uses its deceptive domain score and search patterns to rank those most likely to be impersonating your brands. Suspected attacks are combined with common paths to monitor for malicious content.
Front Page Searches
Since there is no guarantee that a fraudulent website will be using a suspicious domain, Netcraft also searches the front page content of websites.
App Store Searches
Netcraft searches official and unofficial third-party app stores to find fake apps that impersonate your organization’s legitimate applications.
These clone apps may contain malware, or be constructed to trick victims to gain access to security details.
Search Engine Advertising Searches
Netcraft detects adverts targeting your brands including country-specific adverts, on search engines including Google, Bing, Yahoo and DuckDuckGo.
The results are automatically classified and monitored—including the destination websites—to detect those which are malicious.
DMARC Forensic Report Processing
Netcraft processes DMARC reports on your behalf, which are sent by ISPs and email receivers when they see any emails which claim to be from one of your own domains.
SSL Site Searches
Netcraft monitors certificate transparency logs together with millions of SSL certificates found by the Netcraft SSL Server Survey to detect certificates issued to domains and hostnames that are deceptively similar to your own.
Frequently Asked Questions
A malicious website being used in a cyberattack—for example a phishing site impersonating your brand—can be hosted on existing websites or on purpose-created lookalike domains. Around one-third of phishing threats taken down by Netcraft in 2022 were on deliberately registered domains.
Lookalike domains directly impersonate your organizations and will be created purposely for fraud – these might look like examp1eb4nk.com. The domain name itself is under the control of the criminal. On otherwise legitimate platforms where criminals can control only a portion of the domain, you may find examples like examp1eb4nk.example.com.
Alternatively, criminals may compromise an existing legitimate website and make the attack available there – for example at example.com/wp-includes/examp1eb4nk/login.php.
Other infrastructure involved can include URL shorteners, redirectors, drop sites, messaging platforms and more. Sophisticated attackers can layer multiple techniques to make attacks stickier.
Detecting fraudulent lookalike websites and domains relies on extensive proactive searches across the internet for instances of your brand name, slogans, trademarks. These proactive searches focus on:
- Domain name zone files: For example, on a list of all new .com domains. Access to zone files is typically only available to vetted parties.
- Certificate Transparency logs: Freshly issued SSL certificates are logged publicly and can provide an early indicator of fraudulent intent.
-
Internet survey data and other sources: Robust internet survey data and other sources can power additional detection, particularly with subdomains like
examp1eb4nk.weebly.comthat would not appear in domain lists or in wildcard certificates.
Netcraft uses its industry-standard malicious site feeds to detect cyber attacks targeting our customers on compromised websites. These feeds are widely licensed by browsers, antivirus companies and across the internet industry
Compromised sites will not appear in many of the most common sources of data on new domain registrations as these attacks do not rely on a lookalike domain. For example, they may have a URL that looks like example.com/wp-includes/examp1eb4nk/login.php and there is no indication of malicious activity based on the example.com domain name.
Finding attacks in these high-volume, low-signal sources can be like finding a needle in a haystack and requires sophisticated automated processing to discover, classify, and validate attacks as targeting your organization. Netcraft’s digital risk protection platform deliveries a complete end-to-end service covering the whole pipeline.
Some of these tricks used by criminals to create lookalike domains include using internationalized domain names with lookalike characters, substituting similar-looking characters, manipulating character order, and adding prefixes or suffixes to mimic trusted domains. Combining these tricks with Netcraft’s extensive data on cybercrime impersonation, we use these signals to calculate a deceptive domain score.
By analyzing the minimum number of edits needed to transform one domain name into another, considering tricks commonly used to deceive victims, such as double letters or confusing character combinations. The algorithm also checks against a list of deceptive prefixes and suffixes used by previously blocked attacks.
The domains in the table below have previously hosted phishing attacks and are shown together with their deceptive domain score.
| Domain | Target | Deceptive Domain Score |
|---|---|---|
|
xn--blockchan-n5a.info (blockchaín.info) Matched ‘blockchain’ (Blockchain) |
blockchain.info | 9.50 |
|
ppayparl.com Remove character: p<p>ayparl Remove character: paypa<r>l Looks like ‘paypal’ (PayPal) |
paypal.com | 9.00 |
|
update-capitalone.ga Matched ‘capitalone’ (Capital One) Change registerable point from .ga to .com |
capitalone.com | 8.51 |
|
fcbook.com Remove character: f<c>book Looks like ‘fbook’ (Facebook) |
facebook.com | 7.60 |
|
american-express-r2se3.com Remove character: american<->express Looks like ‘americanexpress’ (American Express) |
americanexpress.com | 6.72 |
|
steamupdatex.com Remove suffix of ‘updatex’ Matched ‘steam’ (Steam) |
steampowered.com | 4.20 |
|
rdjfa.com String Entropy |
(none) | 3.24 |
You can take advantage of Netcraft’s automated cybercrime detection and threat intelligence to process reports from your own customers. Netcraft offers both email and API-based reporting options to automatically extract potentially malicious URLs and other threat indicators from customer reports received by your team.
By using Netcraft’s automation, you can make the most of what can be a high-volume, low-confidence source of suspicious URL reports and free up your analysts’ time to invest elsewhere.
Insights
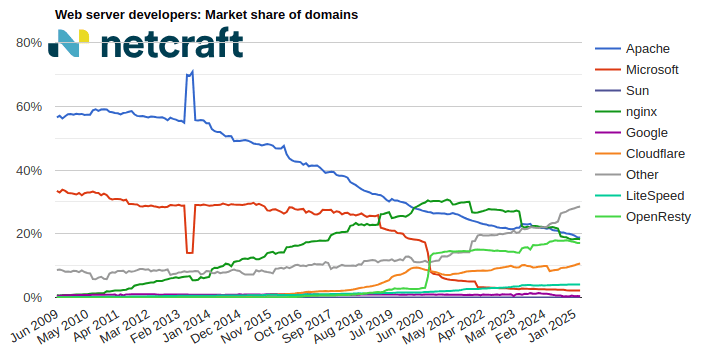
Blog
March 2025 Web Server Survey
In the March 2025 survey we received responses from 1,197,680,522 sites across 275,633,322 domains and 13,402,722 web-facing computers. This reflects … Read More
Learn More
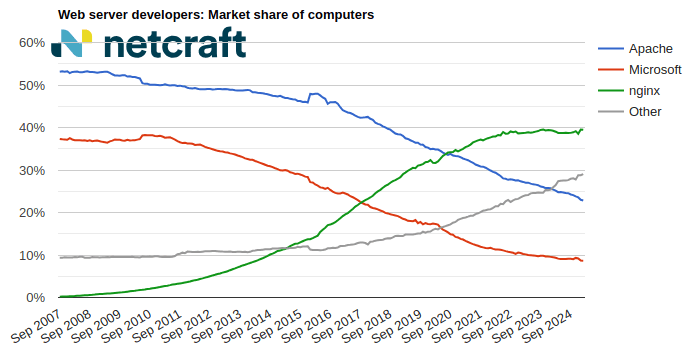
Blog
February 2025 Web Server Survey
In the February 2025 survey we received responses from 1,180,650,484 sites across 274,656,941 domains and 13,480,350 web-facing computers. This reflects … Read More
Learn More

Blog
The Bleeding Edge of Phishing: darcula-suite 3.0 Enables DIY Phishing of Any Brand
Key Data Overview The criminals at darcula are back for more blood, and they mean business with one of the … Read More
Learn More
Schedule time with us
Learn more about Netcraft’s powerful brand protection, external threat intelligence and digital risk protection platform
Social Media Searches
Netcraft regularly searches social media and chat platforms to find fraudulent ads, profiles, groups, and posts. This includes Facebook, Twitter, LinkedIn, TikTok and Instagram.