
Domain Protection
Protect your domain portfolio against cybercrime and misuse, including detecting, disrupting and taking down cyber attacks impersonating your brand
Protecting your domain portfolio
Protecting your domain name portfolio against cybercrime has two major components: better defending domains already owned by your organization against threats like business email compromise and using external threat intelligence to detect, disrupt and takedown cyber attacks—including phishing, scams, and malware—hosted on lookalike domains.
Netcraft’s platform monitors the email security and DMARC settings across your domain portfolio, highlighting insecure configurations and automatically and transparently handling any incoming reports of misuse.
Our highly automated digital risk protection platform searches for typosquatting, homoglyph attacks and other lookalike domains. Discovered impersonations are monitored, and as soon as malicious content is detected, they are taken down.
Defeating cyber attacks with unmatched scale and effectiveness
Netcraft’s online brand protection operates 24/7 to discover phishing, fraud, scams, and cyber attacks through extensive automation, AI, machine learning, and human insight. Our disruption & takedown service ensures that malicious content is blocked and removed quickly and efficiently—typically within hours.

0%
of the world’s phishing attacks taken down

0M+
threat reports and suspicious URLs analyzed every day

0M
cybercrime attacks blocked to date

0M+
attacks taken down and growing
Detecting deceptive domains
Netcraft monitors DNS registrations, zone files and certificate transparency logs for domains and hostnames deceptively similar to your own. This is complemented by our cybercrime detection and global cyber threat intelligence.
Our insight into the tricks used by criminals—such as substituting lookalike characters, inserting/deleting/re-ordering characters, or adding keywords such as ‘update’, ‘login’ and ‘secure’—feeds into the deceptive domain score that is used to rank the likelihood of misuse.
Where an attack has yet to be launched, we’ll monitor to keep looking for fraud. This includes fetching from different locations. Once an attack has been detected and verified, it is blocked within minutes for the billions of people, and taken offline within hours.

Cyber attacks that exploit your brand
Building on more than 25 years of experience surveying the internet, we use our extensive collection of domain information, website front pages, search engine advertisements, social media sites, spam mail feeds, and app stores to identify the following online threats:
Phishing Attacks
Attempts to deceive account holders into giving their account credentials (or other sensitive material) away.
Malware Infrastructure URLs
URLs that malware attempts to connect to, including those that download further stages of cyber attacks (or receive payment for malware such as ransomware).
Malicious Email Addresses
Email addresses participating in advance fee fraud schemes, found in the millions of spam emails that Netcraft analyzes.
Rogue Mobile Apps
Fake apps which impersonate organizations’ legitimate applications, in order to gain access to their users’ personal details
Fake Shops
Claiming to offer highly discounted goods, they are simply a front to capture users’ payment information, and will deliver counterfeit products (or none at all)
Deceptive Domains
Domains which are deceptively similar to legitimate websites, thus lending credibility to a cyber attack.
Frequently Asked Questions
Online retailers and businesses across all sectors use websites and domains to sell services and develop their brand. Criminals will ‘spoof’ your legitimate domain in order to make their cyber attacks appear more convincing.
Your brand reputation, your customer loyalty, and ultimately your financial bottom line is at risk because a website is often the primary point of interaction between a business and its customers (and also its employees, partners, and prospective employees).
Criminals will use a number of techniques in order to trick a victim into thinking that the fraudulent website is legitimate. This includes registering substituting lookalike characters, such as “o” (letter O) and “0” (zero) with the domain.
The fake website will often include duplicated logos, trademarks and products of the spoofed site to make the scam more convincing. Victims are reassured when they see familiar branding, and are less likely to suspect malicious activity.
Typosquatting is when criminals register a common misspelling of another organization’s domain as their own. If you mistype the legitimate site (for example, www.bbcco.uk) you’ll arrive at the criminal’s site instead. In some cases, the site will have been crafted to resemble the legitimate site you intended to visit.
Insights
Blog
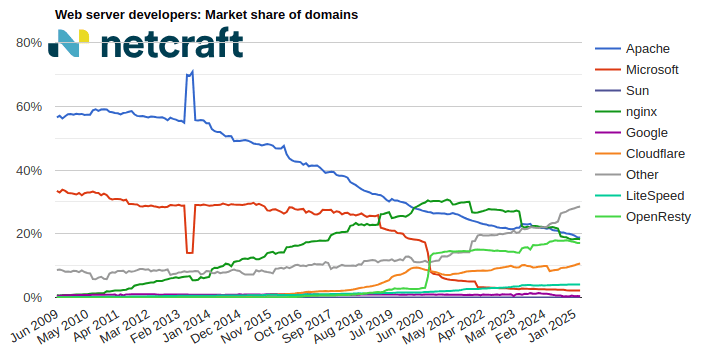
March 2025 Web Server Survey
In the March 2025 survey we received responses from 1,197,680,522 sites across 275,633,322 domains and 13,402,722 web-facing computers. This reflects … Read More
Learn More
Blog
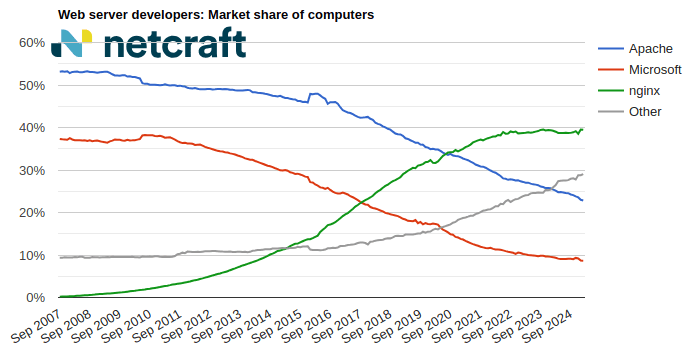
February 2025 Web Server Survey
In the February 2025 survey we received responses from 1,180,650,484 sites across 274,656,941 domains and 13,480,350 web-facing computers. This reflects … Read More
Learn More

Blog
The Bleeding Edge of Phishing: darcula-suite 3.0 Enables DIY Phishing of Any Brand
Key Data Overview The criminals at darcula are back for more blood, and they mean business with one of the … Read More
Learn More
Schedule time with us
Learn more about Netcraft’s powerful brand protection, external threat intelligence and digital risk protection platform
Social Media Impersonation
Fraudulent Facebook pages (as well as fake Twitter and Instagram accounts) created to mislead and confuse potential victims.