Guide to Preventing Phishing and Other Cyber Attacks
It’s not just large online brands and organizations that are at risk from phishing and other cyber attacks. The majority of threats are opportunistic, with cybercriminals only too happy to exploit any online weaknesses, regardless of the targeted organization’s size, cybersecurity budget, or the sector that it operates in.
Speaking to CBS News’ 60 Minutes, Federal Reserve Chair Jerome Powell said “The world evolves. And the risks change as well. And I would say that the risk that we keep our eyes on the most now is cyber risk” (cbsnews.com). The online environment “has become a more popular target for illicit trade which poses a major challenge to an innovation-driven global economy” according to a report (europa.eu) carried out by the EUIPO (European Observatory on Infringements of Intellectual Property Rights) and the OECD (Organisation for Economic Co-operation and Development).
A phishing attack impersonating a US Bank
In this guide, we will focus on how to detect, disrupt, and ultimately neutralize online threats impersonating your brands. Phishing and other cyber attacks can damage your organization’s reputation, cause huge financial losses, disrupt operations and the provision of services, and also threaten the online safety of your customers and prospects.
We’ll also take a look at how the most common cyber attacks work, and examine how Netcraft’s anti-cybercrime platform is uniquely positioned to combat online threats with unparalleled speed and accuracy.
Cybercrime threats, at a glance
The majority of cybercriminals are motivated by financial gain, and will use a variety of attack methods, requiring only modest technical ability, to exploit your organization’s digital channels.
They might construct fake shops purporting to sell branded goods that drives traffic away from your legitimate site. Or register a domain name that is so similar to yours that customers believe they’re using your website, when it’s in fact controlled by a criminal.
Alternatively, they could establish phishing sites designed to steal payment and personal information from your existing (and potential) customers. Or they might create convincing social media profiles or ads to mislead customers or direct them to malicious websites.
This is just a small selection of the types of cyber attack that criminals will exploit. Below are descriptions of the most common attack types and techniques.
Phishing attacks
Phishing is a type of online scam where criminals impersonate legitimate organizations in an attempt to trick victims into sharing personal information, such as passwords or credit card numbers. These scams can be very convincing and use logos, colors, and website layouts that look identical to those used by the impersonated organization. Phishing attacks can lead to real personal losses for each victim, as well as reputational and financial risk for the organizations that are targeted.
Phishing attacks are often launched on a massive scale, as criminals can send millions of scam emails and SMS messages quickly, at virtually no cost. If a victim clicks on a link from within the scam message, they’ll be directed to a phishing website, designed to look like those operated by established organizations. From here, the criminals will attempt to lure visitors into disclosing private and sensitive information (which can be used for future cyber attacks), or may trick victims into transferring funds into an account they control.
Phishing attacks have evolved over the years, going far beyond the stereotype of criminals in a far-off place sending millions of misspelled emails in the hopes of tricking a naive user to submit their bank account details. Modern phishing emails can be very difficult to spot, even by experienced users, and are expertly designed to mimic official communications.
Fake shops
Claiming to offer highly discounted goods, fraudulent online stores (or fake shops) impersonate the websites of luxury brands and established retailers. These shops are often a front to capture payment details (and other sensitive information) that users submit at the checkout stage of the transaction. These details can then be used to create convincing phishing attacks (described above) or sold on to other cybercriminals. For most victims, goods are rarely delivered, and those that are will most likely be counterfeit.
Fake shops don’t just harm your existing customers; they also drive your prospects away from your legitimate online store, costing brands financially and in terms of reputational damage.
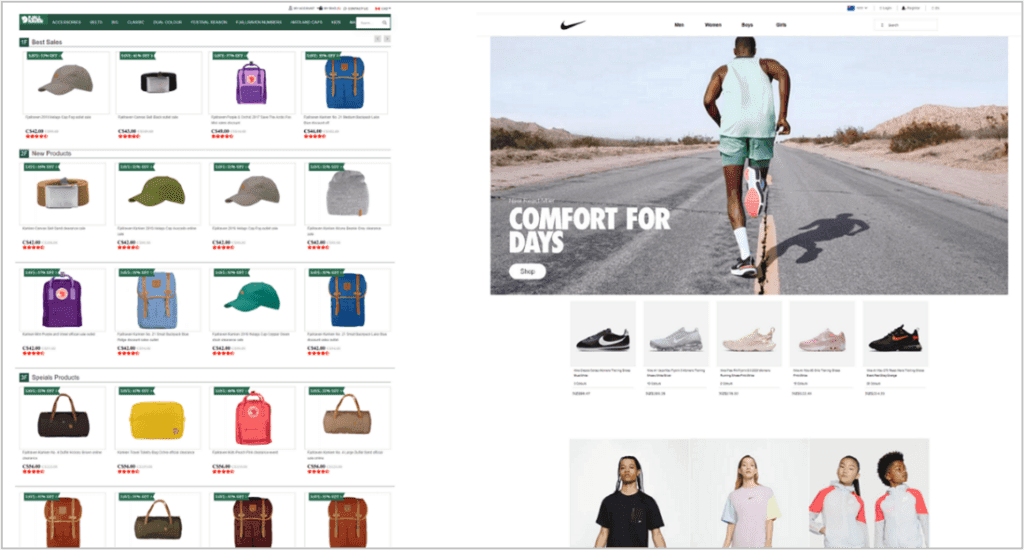
A fake shop selling luxury sporting goods
Deceptive domains
Online retailers and businesses across all sectors use websites and domains to sell services and develop their brand. Criminals will ‘spoof’ legitimate domains (website addresses) in order to make their cyber attacks appear more convincing. This includes a number of techniques to make the domain look authentic, such as substituting lookalike characters – such as “o” (letter O) and “0” (zero) – or ‘typosquatting’ (when criminals register a common misspelling of another organization’s domain as their own).
The fake website will often include duplicated logos, trademarks and products of the spoofed site to make the scam more convincing. Victims are reassured when they see familiar branding, and are less likely to suspect malicious activity.
Fake mobile apps
The popularity of apps, which are installed on millions of phones and tablets, has led to cybercriminals creating fake copies of official apps in order to impersonate legitimate organizations . The aim is, again, to obtain their customers’ personal information or financial details, which are often required in order to install the app. Criminals will take organizations’ official apps from the Google Play and the Apple store and redistribute copies on their third-party sites, giving them opportunity for the app to be hacked before it’s installed.

A mobile banking app available to download on an unofficial app store
Social media impersonation
Cyber criminals will create fraudulent Facebook pages, as well as fake Twitter and Instagram accounts, created to mislead and confuse potential victims. They can include scam celebrity endorsements designed to trick victims into visiting fake shops and other malicious websites, or fake profiles of your key employees (known as ‘executive impersonation’) that appear on LinkedIn and other professional networking sites.
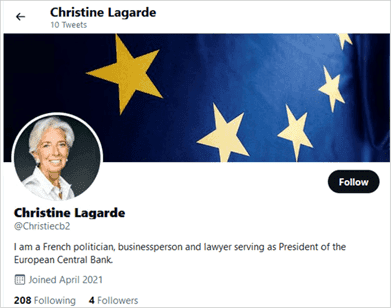
Fake accounts exploiting famous political personas on Twitter
Netcraft’s cybercrime platform
Netcraft’s automated brand protection platform operates around the clock to detect cyber threats including phishing attacks, deceptive domains, executive impersonation, fake shops and 100+ more attack types.
Sophisticated detection techniques
At the core of Netcraft’s detection capability are highly effective searches across internet-scale datasets derived from Netcraft’s decades of experience mapping the internet.
Searches cover a wide range of digital channels including typosquatting or lookalike domains, compromised websites, social media platforms, search engine ads, email and SMS. Processing over five million threat reports each day, Netcraft continuously monitors for occurrences of our customers’ brand names, logos and trademarks online.
Detected threats are analyzed using our automated threat intelligence platform and those targeting customers begin the disruption & takedown process.
Disrupting cyber attacks
Once a cyber attack—a phishing website, fake social media profile, or fraudulent email, for example—has been detected through Netcraft’s cybercrime detection or by your own team and validated with our threat intelligence process, Netcraft blocks access to the attack and begins the takedown process.

Once blocked, users of the Netcraft apps and extensions are immediately protected. Netcraft also licenses its feeds to browsers and antivirus companies along with internet infrastructure companies, protecting billions of internet users from potential exposure while Netcraft’s automated takedown services work to rapidly take the attack offline completely.
Rapid takedown of malicious content
To conduct a takedown, Netcraft gathers evidence of the cyber attack, and begins to identify the relevant parties providing resources to the attacker. In parallel, Netcraft automatically contacts hosting providers, domain registrars, webmasters and others via email, API, private contact, or otherwise.
A suspected attack can be analyzed, validated, and takedown notifications dispatched within minutes of discovery. This is thanks to Netcraft’s highly automated takedown process which uses rule-based matching (and other machine learning technologies) to gather the necessary evidence that providers require to take down the malicious content.
Our automated takedown process is designed to rapidly identify and block malicious or fraudulent websites and domains in order to restore a safe online environment for you and your customers.
In the know, at all times
The takedown process is easy to follow for Netcraft customers, who can track the progress using our web portal, email or API. You can easily monitor every aspect of the cyber attacks impersonating your brands, from initial detection through disruption and takedown. Netcraft provides an JSON API which allows integration with your internal applications. In addition, we have integrations for Splunk and Azure Sentinel allowing convenient integration of the takedown system with those platforms.
The Netcraft difference
We are the world’s largest takedown provider, and centrally positioned in the global fight against cybercrime. Our detection, disruption, and takedown solutions are highly automated, powered by the vast amounts of data we collect every day and backed by the expertise of our in-house team.
A unique combination of cutting-edge automation, unmatched scale, and a reputation for excellence and transparency built over decades of work—all powered by a passion to make the digital world a safer place—gives Netcraft’s solution an edge that simply cannot be replicated.
Rapid disruption and takedowns
Core to Netcraft’s digital risk protection platform is its automated takedown services which leads the industry in terms of speed, effectiveness, and sheer volume—Netcraft takes down 15 million cyber attacks each year and is responsible for one-third of global phishing attack takedowns.
Using Netcraft’s extensive knowledge of internet infrastructure, and its position as a highly respected authority within the space, Netcraft knows precisely who to reach out to, which channels to use, and what to say.
Unmatched volume & scale
Netcraft’s cybercrime detection, disruption and takedown platform is powered by sophisticated automation operating at scale, built with unique insight from our people. Able to operate autonomously and around the clock, Netcraft identifies and validates cybercrime attacks quickly and accurately. Early detection leads to early disruption, which reduces the impact of cyber threats.
Trusted threat intelligence
Netcraft transforms millions of daily reports of into actionable threat intelligence covering diverse threat types including phishing, scams, fake social media profiles and malware. We use real-world web browsers, flexible automated interaction, machine learning, and AI to explore cyber attacks and their inner workings.
Our external threat intelligence data is used to protect billions of people through partnerships with browsers, antivirus companies and internet infrastructure providers. Netcraft’s feeds are global, and cover all impersonated institutions, not just our takedown customers.
At the heart of the internet ecosystem
We capitalize on our long-standing relationships within the infrastructure community to quickly mitigate the harmful impact of cyber attacks. Netcraft has spent decades at the heart of the internet ecosystem. High-quality data combined with a focus on demonstrating evidence and clear communication has earned Netcraft the respect and trust of key internet infrastructure providers, such as leading domain name registrars and hosting companies.
This commitment to transparency can be observed across the detection and disruption process—from providing comprehensive evidence of a validated cyber attack to infrastructure partners to sharing real-time status updates on an active takedown with our customers.
About Netcraft
Netcraft — the global leader in cybercrime detection and disruption — is a trusted partner for three of the four largest companies, twelve of the fifty largest banks, and five of the largest economies in the world. Our comprehensive threat feeds, early fraud detection capabilities and swift automated countermeasures are unparalleled in the industry.
We perform takedowns for nearly one-third of the world’s phishing sites, blocking more than 170 million malicious sites and counting. Many of the largest brands and organizations around the world trust Netcraft. Our customer base includes a diverse mix of industries, sizes, and organizational types, including leading companies within the financial, retail and technology sectors.
Find out more
Netcraft’s mission is to detect and disrupt cybercrime at scale through constant innovation, extensive automation, and unique insight, delivering a safer online experience for everyone.
To find out how Netcraft’s cybercrime detection, disruption and takedown platform can protect your organization and your customers, you can request a demo or find out more about our platform.






